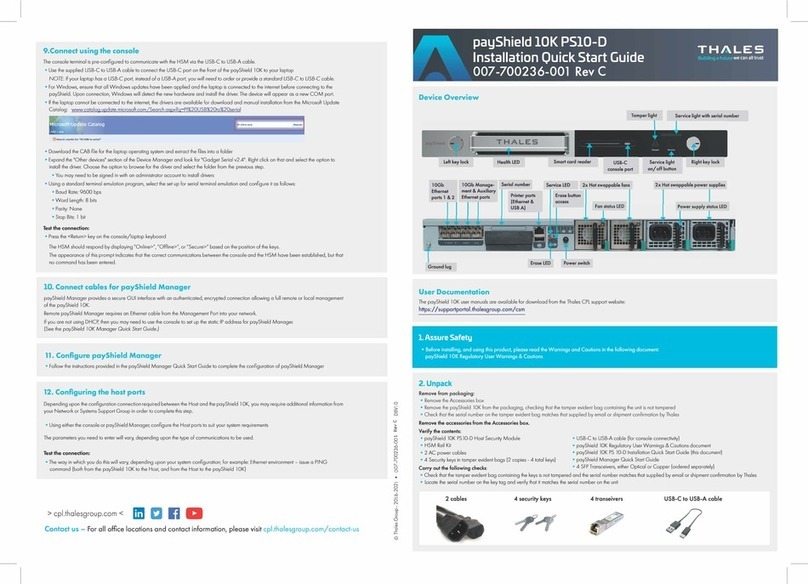
CipherTrust Manager k160
Quick Start Guide
007-500223-001, Rev. E
04/30/2023 Thales Trusted Cyber Technologies, Proprietary 3
HSM Root of Trust Configuration
The CipherTrust k160 utilizes a token HSM as its root of trust. After registering the first token HSM, additional tokens may be added.
Download the CLI Toolkit
1. In the web GUI, click the “API” button at the far right of the top
title bar to open the API Playground.
2. On the top left, click into the CLI Guide.
3. Download the ksctl_images.zip package using the blue
download button on the top right of the window.
This package contains the CLI tools and sample configuration
file to initialize the HSM tokens to the k160.
NOTE: Previous versions of KSCTL may not be fully
compatible. Use the CLI package as downloaded from the
k160 being deployed.
4. Unpackage the ZIP archive on your client workstation.
5. Navigate to the ksctl_images directory, copy the
config_example.yaml under a new name (e.g. “k160.yaml”),
and modify these lines within:
KSCTL_URL: <k160 IP>:443
KSCTL_PASSWORD: <password set in GUI above>
KSCTL_TIMEOUT: 360
Perform the HSM Setup
1. Insert the first token HSM into the front slot of the k160.
NOTE: Verify that the tokens are firmly inserted into their
USB interfaces and, if applicable, the High Assurance token
is not illuminated red.
2. From the CLI toolkit (ksctl_images) directory, execute the
following command, aligned to the model of k160:
ksctl.exe --configfile "<path>\<k160>.yaml"
hsm setup k160 --reset [--ha | --std]
“--ha”for High Assurance |“--std”for Standard
The HSM configuration validates and the system will reset.
NOTE: If you attempt to log inon the GUI, you will see various
messages about services starting up and it will take over 10
minutes to complete the start-up process.
3. Log back into the GUI with the original login credentials
(admin/admin) and reestablish a new admin password.
4. Verify the HSM token has been set up by visiting the HSM
settings page at “Admin Settings HSM.”
Register an Additional Token HSM
1. Keeping the first token inserted into the k160, insert
another token into a USB slot on the back of the k160.For
HA models, use the provided USB extender cable.
2. From the CLI toolkit (ksctl_images) directory, execute the
following command:
ksctl –-configfile "<path>\<k160>.yaml" hsm
tokens reg
3. Once the command completes, remove the additional
token from the back of the k160.
WARNING:Removing the token from the front of the k160
will cause a system restart.
Removing a Token During Operation
Removing the token HSM triggers the system services to shut down within 1 minute, shutting off all access to cryptographic materials and
rendering keys, stored objects, etc. encrypted and unusable.
•The system services enter into a restart loop, checking for the reintroduction of a registered token HSM.
•Once a registered token HSM is provided, the system will start back up and resume operations.
•Stored objects can only be recovered by reintroducing a registered token HSM or by performing a system reset and restoring from a
backup.