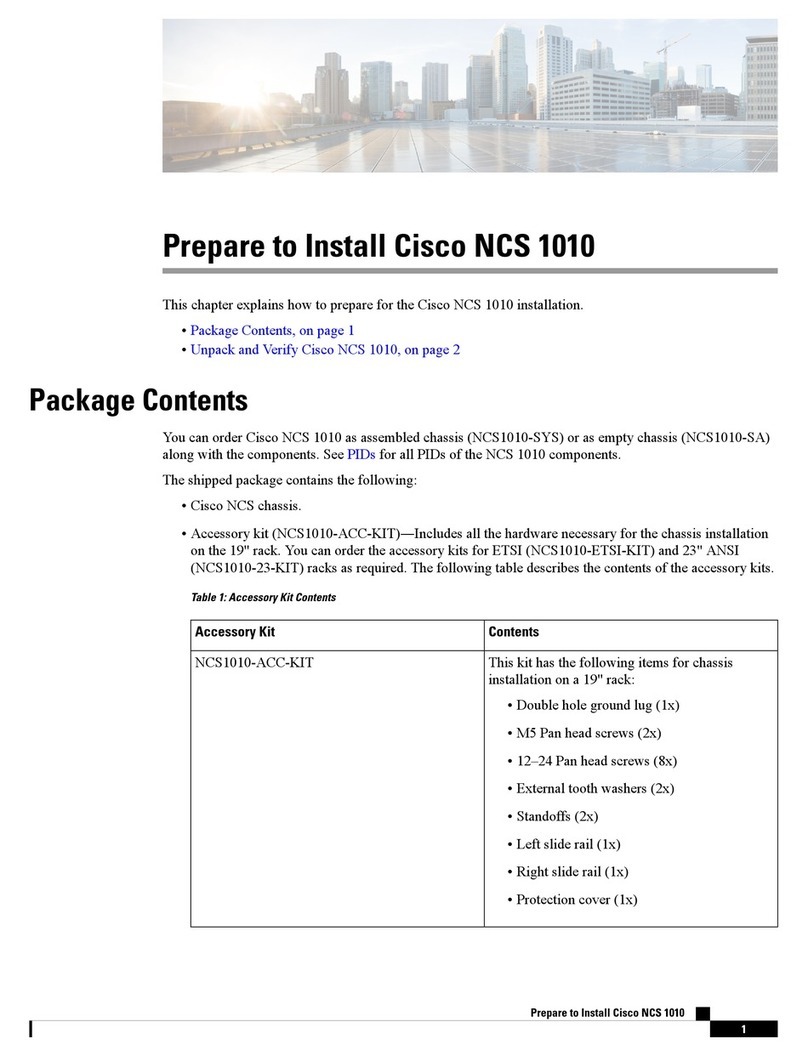
SSH Mgmt Access IPv4 netmask: 255.0.0.0
Firepower Chassis Manager cannot be accessed if HTTPS Mgmt Access is not configured.
Do you want to configure HTTPS Mgmt Access? (yes/no) [y]: y
HTTPS Mgmt Access host/network address (IPv4/IPv6): 10.0.0.0
HTTPS Mgmt Access IPv4 netmask: 255.0.0.0
Configure the DNS Server IP address? (yes/no) [n]: y
DNS IP address : 10.164.47.13
Configure the default domain name? (yes/no) [n]: y
Default domain name : cisco.com
Following configurations will be applied:
Switch Fabric=A
System Name=firepower-9300
Enforced Strong Password=no
Supervisor Mgmt IP Address=10.89.5.14
Supervisor Mgmt IP Netmask=255.255.255.192
Default Gateway=10.89.5.1
SSH Access Configured=yes
SSH IP Address=10.0.0.0
SSH IP Netmask=255.0.0.0
HTTPS Access Configured=yes
HTTPS IP Address=10.0.0.0
HTTPS IP Netmask=255.0.0.0
DNS Server=72.163.47.11
Domain Name=cisco.com
Apply and save the configuration (select 'no' if you want to re-enter)? (yes/no): y
Applying configuration. Please wait... Configuration file – Ok
.....
Cisco FPR Series Security Appliance
firepower-9300 login: admin
Password: Farscape&32
Successful login attempts for user 'admin' : 1
Cisco Firepower Extensible Operating System (FX-OS) Software
TAC support: http://www.cisco.com/tac
Copyright (c) 2009-2019, Cisco Systems, Inc. All rights reserved.
[...]
firepower-chassis#
Low-Touch Provisioning Using Management Port
When your Firepower 4100/9300 chassis boots up, if it does not find the startup configuration, the device
enters the Low-Touch Provisioning mode in which the device locates a Dynamic Host Control Protocol
(DHCP) server and then bootstraps itself with its management interface IP address. You can then connect
through the management interface to configure the system using SSH, HTTPS, or the FXOS REST API.
Getting Started
4
Getting Started
Low-Touch Provisioning Using Management Port