Fidelis Common Criteria User manual

Fidelis Network™
Common Criteria
Configuration Guide
Version 9.0.3

Copyright © 2002–2018 by Fidelis Cybersecurity
All rights reserved worldwide.
Fidelis Cybersecurity
4500 East-West Highway, Suite 400
Bethesda, MD 20814
Fidelis Network™, version 9.0.3
Common Criteria Configuration Guide
Revised August 2018
Users are granted permission to copy and/or distribute this document in its original electronic form and
print copies for personal use. This document cannot be modified or converted to any other electronic or
machine-readable form in whole or in part without prior written approval of Fidelis Cybersecurity.
While we have done our best to ensure that the material found in this document is accurate, Fidelis
Cybersecurity makes no guarantee that the information contained herein is error free.
Fidelis Network includes GeoLite data created by MaxMind, available from http://www.maxmind.com/

Fidelis Network Common Criteria Configuration Guide Version 9.0.3 iii www.fidelissecurity.com
Table&of&Contents&
Common Criteria Configuration Guide .............................................................................. 1
Enhanced Information for Chapter 2, Appendix A and Appendix B of [1] ................. 2
Chapter 2 Setup and Configure .................................................................................................... 2
Default Accounts and Initial Passwords .................................................................................................... 2
Connect a Physical Appliance to the Network and Configure ................................................................. 3
Appendix A Security Certificates and Common Access Cards ............................................. 3
Obtaining and Importing a Certificate ........................................................................................................ 3
Appendix B Security Best Practices ........................................................................................... 4
User Access ................................................................................................................................................ 4
Change the Default Account Passwords .............................................................................................. 4
Command Line Session Inactivity Timeout........................................................................................... 4
Configure Password Requirements for Local Users ............................................................................ 5
Enhanced Information for Common Criteria Configuration of [1]................................ 7
Appendix C Common Criteria ....................................................................................................... 7
Common Criteria Compliant Configuration ............................................................................................... 7
Common Criteria Compliant Trusted Channels to External Components .............................................. 8
System Updates .......................................................................................................................................... 8
Digital Signatures for Updates ............................................................................................................... 8
Common Criteria Compliant Published Hash for Updates .................................................................. 8
Power on Self Tests and Process Manager ............................................................................................. 9
Audit Events ...............................................................................................................................................10
Making Configuration Changes ................................................................................................................18
Set Up FIPS 140-2 Certificates .................................................................................................................18
TLS..............................................................................................................................................................19
Remote Authentication ..............................................................................................................................20
Connections between Distributed TOE Components..............................................................................21
Secure Disposal of Equipment..................................................................................................................21
References............................................................................................................................. 22

Fidelis Network Common Criteria Configuration Guide Version 9.0.3 1 www.fidelissecurity.com
Common Criteria Configuration Guide
This document is the Fidelis Network Common Criteria Configuration Guide. It replaces Appendix C of the
Enterprise Setup and Configuration Guide [1]. The information in the following sections is new or
corrected information related to the Enterprise Setup and Configuration Guide [1] reproduced as entire
sections in this document. This document provides or references all the necessary instructions to
configure, monitor and maintain Fidelis Network as certified by Common Criteria.
This Configuration Guide is applicable to Fidelis Network Version 9.0.3, which is the Common Criteria
evaluated version of Fidelis Network.

Fidelis Network Common Criteria Configuration Guide Version 9.0.3 2 www.fidelissecurity.com
Enhanced Information for Chapter 2, Appendix A
and Appendix B of [1]
The sections below provide corrected information required to configure, monitor and maintain a working
system as certified by Common Criteria. These sections are based on the information in the Enterprise
Setup and Configuration Guide [1], and are reproduced here in entirety with new or corrected information.
Chapter 2 Setup and Configure
Default Accounts and Initial Passwords
The information in this section applies to all appliances.
To access the appliance from the Linux command line, connect the appliance to a local keyboard and
monitor.
The Linux command line account and initial password for all appliances are:
Account
Initial password
How to reset
fidelis
fidelispass
/usr/bin/passwd
K2 GUI account and initial password are:
Account
Initial password
How to reset
admin
system
Click user name at the
top of the GUI.
For iLO the user ID and password are on the unit’s label on top of the server. Once the user connects to
the iLO via a web browser, these credentials are needed. After logging in, the user ID and password can
be changed.
For IMM account and initial password are:
Account
Initial password
How to reset
USERID
PASSW0RD (with a zero,
not the letter O)
Click Login Settings in
the left column of the
IMM GUI.
Important!
Ensure that you change the default password after the initial login. This can be performed in
the Configuration Wizard. Save the new password in a secure location so that you will have
access to accounts when needed.
Do not use the Linux command line account for normal system operation after initial setup
is complete. The account should only be used under the direction of Technical Support if
needed to determine the cause of system malfunction.
Only use the K2 GUI default account to run through the Configuration Wizard at initial setup.
The wizard will guide you through the creation of new user accounts and changing the
default password. Once user accounts are created, do not use the default account.

Fidelis Network Common Criteria Configuration Guide Version 9.0.3 3 www.fidelissecurity.com
Access to the iLO or IMM interface should be physically limited to only those users that
require access. These interfaces are not secured by Fidelis Network software.
Refer to Appendix B in the Enterprise Setup and Configuration Guide[1] for Security
practices regarding your installation.
Connect a Physical Appliance to the Network
and Configure
The first four steps in this section apply to physical appliances. The remaining steps apply to physical and
virtual appliances. For virtual appliances, you also need to refer to chapter 3 in the Enterprise Setup and
Configuration Guide [1].
1. Rack the unit with access to proper power, cooling, and ventilation.
2. Connect power cables and attach to the power supplies in the back of the appliance.
3. Refer to the Quick Start Card for initial post-factory installation of the product if needed. It will guide
you through the process of finalizing Fidelis Network software installation.
4. Connect a keyboard and monitor to the appliance.
5. After configuration is complete, type exit to log out.
Appendix A Security Certificates and
Common Access Cards
Obtaining and Importing a Certificate
Follow instructions in this section to generate a Certificate Signing Request (CSR); obtain a certificate, CA
certificates, CRL; import these for use by a Fidelis Network component. Run all commands in this section
as root. In all commands, <subsystem> is the affected part of Fidelis Network functionality and must be
one of the recognized subsystems listed above.
1. Generate a Certificate Signing Request (CSR).
This will generate a new RSA private key, and create a new CSR based on it.
The --subject-dn=<component_dn> argument specifies the component's Distinguished Name (DN),
which will be used in the CSR and will eventually be used as a subject in the certificate.
If it is not specified, the component's hostname will be used as the default Common Name (CN).
/FSS/bin/cert_manager --subsystem=<subsystem> --action=export-csr --csr-
outfile=/tmp/<output_CSR_file>.pem --subject-dn='<component_dn>'
The Subject Distinguished Name should be provided in the form:
--subject-dn='/C=US/ST=MD/L=Bethesda/O=MyCompanyName/OU=IT
Department/CN=sensor1.mycompany.local'
where the DN fields are separated by ‘/’, with keys separated from values with ‘=’.
Supported DN fields are:

Fidelis Network Common Criteria Configuration Guide Version 9.0.3 4 www.fidelissecurity.com
‘C=’ – two letter country specification. See openssl documentation for details.
‘ST=’ – state.
‘L=’ – locale / city.
‘O=’ – organization name.
‘OU=’ – organizational unit.
‘CN=’ – common name
All fields in the Distinguished Name (DN) are optional, except for Common Name (CN).
For example,
/FSS/bin/cert_manager --subsystem=internal --action=export-csr --csr-
outfile=/tmp/sensor1_internal.csr --subject-
dn='/O=MyCompanyName/CN=sensor1.mycompany.local'
2. Send the generated CSR to your desired Certificate Authority (CA) for it to issue a certificate. Each
CA may have different procedures for issuing certificates. Contact your CA for detailed instructions.
Note: for “--subsystem=internal”, the certificate, generated from the CSR created on the TOE component
as described above, must be signed by Certification Authority in a way that also adds X509v3 extension
Subject Alternative Name that contains IPv4 and IPv4-mapped IPv6 or IPv6 address of the component to
the certificate. For example, the component with IPv4 address ‘192.168.1.40’, hostname ‘sensor1’, and
domain ‘mycompany.local’, should have Subject Alternative Name, as follows:
X509v3 extensions:
X509v3 Subject Alternative Name:
IP Address:191.168.1.40, IP Address: 0:0:0:0:0:FFFF:C0A8:128,
DNS:sensor1, DNS:sensor1.mycompany.local
In Common Criteria-compliant mode of operation, the verifyhost parameter in configuration file
/FSS/etc/ssl.cf must be set to “1”.
Appendix B Security Best Practices
User Access
Change the Default Account Passwords
When you receive the Fidelis system, you receive an initial login and password for command line access.
You should change this password. To do this:
1. Connect to the appliance CLI via console using the fidelis account and default password .
2. Change the password using the command: /usr/bin/passwd
3. Repeat for each sensor and K2.
Command Line Session Inactivity Timeout
To force command line sessions, including local console sessions, to log out after a certain period of
inactivity:
1. As the root user, create the file: /etc/profile.d/autologout.sh
2. Set the permissions of /etc/profile.d/autologout.sh by running the following command:
# chmod 0644 /etc/profile.d/autologout.sh

Fidelis Network Common Criteria Configuration Guide Version 9.0.3 5 www.fidelissecurity.com
3. Add the following lines to /etc/profile.d/autologout.sh. The value given to the TMOUT
variable is in seconds, hence the example below sets an inactivity timeout of 15 minutes:
readonly TMOUT=900
export TMOUT
The inactivity timeout will be applied to all new login sessions. The TMOUT value in seconds should be
greater than 1 and less than 86400 (24 hours). Recommended default value is 900 (15 minutes). Setting
TMOUT to 0 or removing it from the configuration above will disable session inactivity timeout.
Configure Password Requirements for Local Users
Failed Login Attempts: Specify the maximum number of failed login attempts allowed. The “Failed Login
Attempts” parameter defines the number of unsuccessful login attempts the user is allowed before the
user account is locked out and is configurable between 1 and 999. Recommended value is 5. To
reactivate the locked-out account, an administrator must reset that account’s password. The default
“admin” user cannot be deleted. If any other user remote access is blocked the default admin can login to
unlock these accounts.
The minimum password length is administrator configurable from 1 to 999 characters. Recommended
value is 8.
Fidelis Network components utilize Linux Pluggable Authentication Module (PAM), which provides
dynamic authentication support for component applications and services. To configure minimum
password length for logging into the component via the console, the pam-cracklib module “minlen”
parameter must be set to the desired value in /etc/pam.d/system-auth PAM System
Authentication Configuration file, as shown below.
[root@linux90s ~]# cat /etc/pam.d/system-auth
#%PAM-1.0
# This file is auto-generated.
# User changes will be destroyed the next time authconfig is run.
auth required pam_env.so
auth sufficient pam_fprintd.so
auth sufficient pam_unix.so nullok try_first_pass
auth requisite pam_succeed_if.so uid >= 500 quiet
auth required pam_deny.so
account required pam_unix.so
account sufficient pam_localuser.so
account sufficient pam_succeed_if.so uid < 500 quiet
account required pam_permit.so
password requisite pam_cracklib.so try_first_pass minlen=12 retry=3
password sufficient pam_unix.so md5 shadow nullok try_first_pass use_authtok
password required pam_deny.so
session optional pam_keyinit.so revoke
session required pam_limits.so
session [success=1 default=ignore] pam_succeed_if.so service in crond quiet
use_uid
session required pam_unix.so
[root@linux90s ~]#
Figure 1. PAM System Authentication Configuration

Fidelis Network Common Criteria Configuration Guide Version 9.0.3 6 www.fidelissecurity.com
Note that “minlen” is not just a number of characters in the password. It is a computed value and includes
the number of characters in the password, as well as complexity factors from the password itself. For
example, if and how many capitals, numbers, or special characters it has. In addition to the number of
characters in the new password, credit (of +1 in length) is given for each different kind of character (other,
upper, lower, and digit). The default for this parameter is 9.

Fidelis Network Common Criteria Configuration Guide Version 9.0.3 7 www.fidelissecurity.com
Enhanced Information for Common Criteria
Configuration of [1]
Appendix C Common Criteria
This appendix includes information about the following Common Criteria compliant configuration and
other pertinent information.
Common Criteria Compliant Configuration
K2 and the Fidelis Network module have earned Common Criteria Certification. The following provides
the steps required to create the security configuration used for Common Criteria Certification.
1. During initial setup, make sure that NTP is setup correctly and servers are reachable from the
appliance.
2. Change the default passwords for command line for each appliance by following Change the
Default Account Passwords.
3. Change the default passwords for admin GUI account (provided in the Quick Start Card) for each
K2.
4. Configure password strength (Password Strength Requirements) and account lockout due to
requirements for failed login attempts.
5. Create a user with system administrator privileges.
6. Log in as the system administrator user and create user accounts for each person who will use the
K2. The admin account should not be used anymore.
7. Ensure that session timeouts are set for command line (Command Line Session Inactivity
Timeout) and GUI access (GUI Session Inactivity Timeout).
8. Create a custom login banner. Refer to Custom Login Banner.
9. If you are using LDAP, you must configure it to communicate using TLS. Refer to chapter 13 in the
User Guide.
10. Enable FIPS 140-2 compliant encryption for the K2 database. Refer to Encrypted Storage.
11. Before registering any components, obtain X509 certificates as described in Security Certificates
and install them on the K2 (Installing a K2 Certificate) and all the components being registered to
the K2 (Installing Certificates for Inter-Component Communications).
12. Enable sending syslog to a remote server over TLS using configuration described in Enable Client
Authenticationat Security Practices.
13. Enable TLS auditing. At System / Components / K2/ Config / Audit, select everything for TLS
Handshake.
14. To perform system updates, see Common Criteria Compliant Published Hash on published
hash as a common criteria compliant trusted system update.
Fidelis Network Common Criteria Configuration Guide Version 9.0.3 8 www.fidelissecurity.com
The certified configuration includes only the Fidelis Network configuration, including admin interface. Any
additional interface available by your hardware appliance is not certified. For example, the Integrated
Lights-Out (iLO) and the Integrated Management Module (IMM) are excluded from the certified
configuration.
Fidelis Common Criteria certification excludes the fidelis account for command line access (refer to
Default Accounts) after initial configuration. This account is used for initial system configuration. After
initial setup, the fidelis account should not be used unless directed by Fidelis Cybersecurity Technical
Support to diagnose problems.
Common Criteria certification applies to Rev H hardware. Contact Technical Support to determine your
hardware revision. Virtual appliances are supported by the certification on host hardware that includes
Intel Core or Xeon processors based on the Ivy Bridge or Haswell microarchitecture, which implement
Intel Secure Key.
The sections below provide additional information required to monitor and maintain a working system
configured for Common Criteria.
Common Criteria Compliant Trusted Channels to
External Components
Fidelis establishes secure connections to external components within the customer network. Fidelis will
establish trusted channels with an external audit and LDAP servers with TLS enabled communications.
Refer to Enable Client Authentication .
Refer to chapter 13 of User Guide.
System Updates
Digital Signatures for Updates
Fidelis checks for software updates available on the Fidelis Insight Cloud using HTTPS connections. A
software update is available as a tar package along with its digital signature created using RSA secret
key. Fidelis will download both via HTTPS and verify the signature using the on-board public key
(corresponding to the RSA key used to create the signature). If the verification fails, it is assumed that the
download was corrupted and hence the package and its signature are deleted.
Common Criteria Compliant Published Hash for Updates
Software and Policy updates for Fidelis Network are available at the Fidelis Support portal. Fidelis also
publishes the SHA256 hash with the updates. The Common Criteria compliant trusted update mechanism
for Fidelis Network is for an administrator to:
1. Operate the K2 in air gap mode. Refer to chapter 10 in the Guide to Creating Policies.
For Air Gap operation, access the K2 GUI and navigate to the System / Version Control / Download
Control page. Ensure that the parameter: Check for Updates is set to: Never. The K2 GUI page
System / Version Control / Scheduled Installs will then display: No scheduled installs, indicating that
automatic updates are disabled.
2. Download the updates and the hash files from the Fidelis Support portal.
3. Verify the SHA256 hash of the downloaded package is the same as published hash on the portal,
using openssl command line utility, for example:
openssl dgst -sha256 fidelis_xps_9.0.3.x86_64.tar

Fidelis Network Common Criteria Configuration Guide Version 9.0.3 9 www.fidelissecurity.com
SHA256(fidelis_xps_9.0.3.x86_64.tar)=
cb314f328f1e82789f23a6d78e861f3a1adf39bdb683fb2c1e72fd01969d1653
cat sha256
cb314f328f1e82789f23a6d78e861f3a1adf39bdb683fb2c1e72fd01969d1653
4. If the hash values agree, upload the package on the K2 using the File Management configuration in
System / Version Control.
The installation package is uploaded to the File Management page and the policy updates are
uploaded to Policies / Insight / Air Gap Upload.
The TOE calculates the SHA256 hash and displays it to the administrator.
5. If the hash values agree; initiate installation to the distributed components from the K2.
K2 will copy the package to the desired component.
When the package reaches the intended component, the component will then be shut down, the
update installed, and restored to functionality at the new version.
Components that are not subject of the update (other than K2) are functional during update of other
components. K2 Management Console is unavailable while updates are in progress.
In case of component update failure, automatic roll-back action performed by the component and the
error message posted on K2. Depending on the type of failure, user can take appropriate action. For
example, redownload the update tar file in case of hash verification check failure.
Power on Self Tests and Process Manager
Each system daemon that utilizes Cryptographic Module of the component, openssl-1.0.1e-fips, performs
Power on Self-Test (POST) upon initialization. In case of POST failure, the process or service will fail to
initialize, and the Cryptographic Module initialization failure messages are entered in
/var/log/messages, for example:
Jun 3 23:01:01 linux90s db_maint.log[9313]: Error getting system time from
10.91.130.123, output tcp_cli_init
: error initializing ssl library
Jun 3 23:01:01 linux90s , error fips.c(143): OpenSSL internal error,
assertion failed: FATAL FIPS SELFTEST FAILURE
Jun 3 23:01:01 linux90s db_maint.log[9313]: Error getting system time from
10.91.130.120, output tcp_cli_init: error initializing ssl library
Jun 3 23:01:01 linux90s , error fips.c(143): OpenSSL internal error,
assertion failed: FATAL FIPS SELFTEST FAILURE
The POST failure messages include identification of the distributed component (“linux90s” in the example
above) that sustained the failure.
WARNING: In case of fatal POST failures, contact Fidelis Support immediately.
The process manager service checks the binary integrity of every Fidelis daemon dedicated to the
primary security function of the product before it starts any of them. If a single integrity check fails,
process manager aborts, none of the daemons will be started, and the event will be logged in
/var/log/messages, for example:
Aug 12 08:14:23 linux76 pman[29765]: "/FSS/sbin/spoold": wrong checksum
Aug 12 08:14:23 linux76 pman[29765]: Giving up.

Fidelis Network Common Criteria Configuration Guide Version 9.0.3 10 www.fidelissecurity.com
If a system daemon fails to start for other reasons than integrity check failure, the event will be logged in
/var/log/messages. Depending on the daemon and the reason for its failure, more detailed
information may be found in the corresponding log in /FSS/log/.
Audit Events
The table below lists and describes applicable audit events and administrative actions for each of the
security functional requirements (SFRs) covered by Common Criteria.
The general order of the audit events is as follows:
1. Date.
2. Time.
3. TOE Component IP address.
4. TOE Component name (hostname).
5. Process name or audit function name (e.g. FSS audit).
6. Process ID (optional).
7. Audit event description string. This is specific to audit event type.
See the table below for examples and details.
Table 2. SFRs and Auditable Events
SFR
Event
Additional
Information
Sample Log
FAU_GEN.1
Start-up of audit
functions
None
Sep 8 11:38:12 10.42.212.199 localhost
syslog-ng[2368]: syslog-ng starting up;
version='3.7.3'
Sep 8 14:25:43 localhost FSS
audit[2423]: System startup
Shutdown of audit
functions
None
Sep 8 11:34:59 10.42.212.199 04
localhost syslog-ng[2369]: syslog-ng
shutting down; version='3.7.3'
Sep 8 14:23:17 localhost FSS
audit[4273]: System shutdown
FCO_CPC_
EXT.1
Enabling
communications
between a pair of
components.
Disabling
communications
between a pair of
components.
Identity and
type of TOE
component
being
registered or
unregistered.
Identities of
the TLS
endpoints
involved in
the
transaction.
Sep 7 16:47:22 localhost FSS
audit[70423]: admin registered Sensor
linux90col Type: metadatav
Sep 7 16:47:22 localhost FSS
audit[70437]: Sensor <linux90col> TLS
SUCCESS: Local: localhost, Remote:
10.89.184.31
Sep 7 16:47:23 localhost FSS
audit[70441]: Sensor <linux90col>
sensor registered successfully
FCS_HTTPS
Failure to establish a
Reason for
Mar 17 10:01:51 10.42.209.241 FSS:
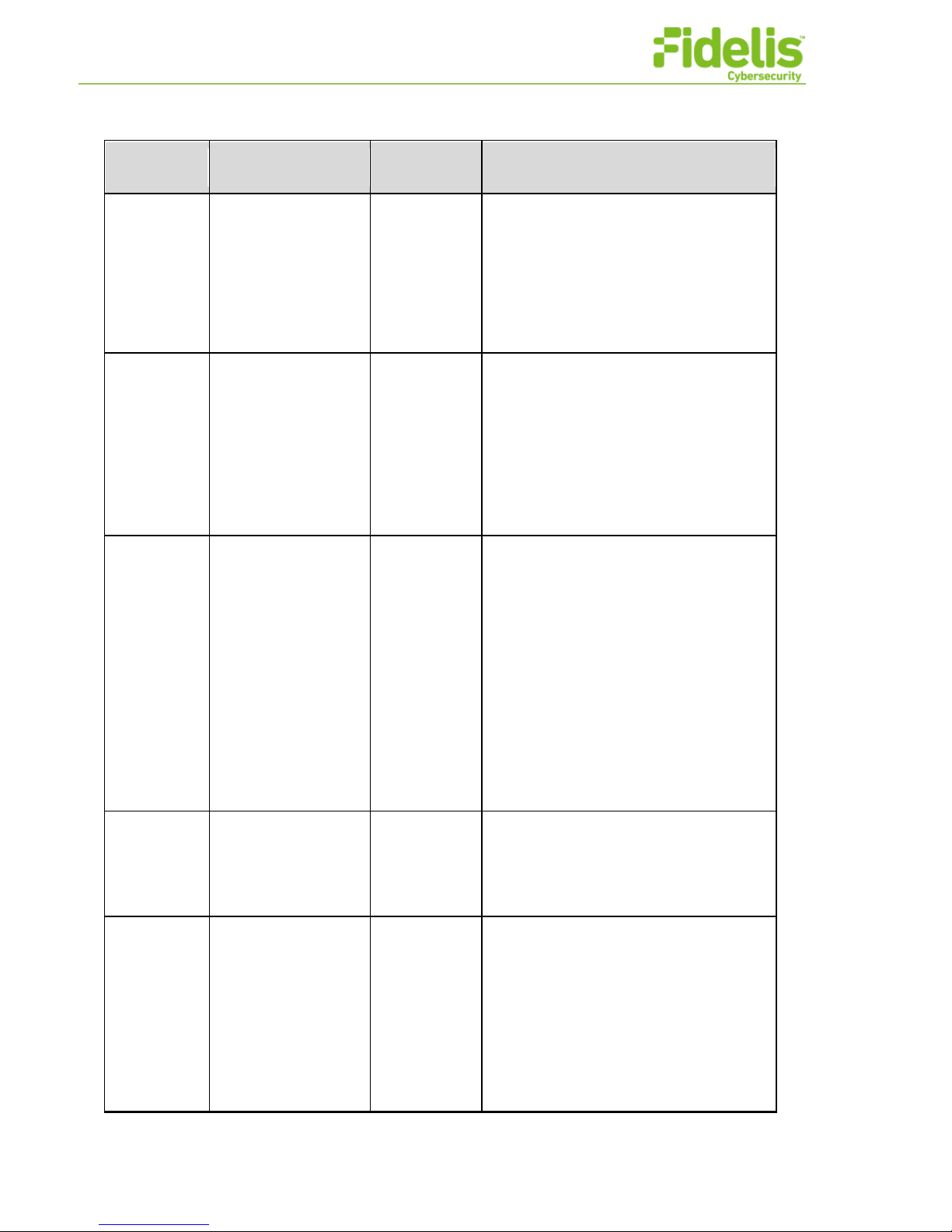
Fidelis Network Common Criteria Configuration Guide Version 9.0.3 11 www.fidelissecurity.com
SFR
Event
Additional
Information
Sample Log
_EXT.1
HTTPS Session.
failure.
Non-TOE
endpoint of
connection
(IP address)
for both
successes
and failures
audit: admin failed attempt to login from
10.42.209.155 (calling: login)
FCS_HTTPS
_EXT.1
Establishment/Termi
nation of a HTTPS
session.
Non-TOE
endpoint of
connection
(IP address)
for both
successes
and failures.
Mar 17 09:52:00 10.42.209.241 FSS:
audit: admin logged on from
10.42.29.155
Mar 17 10:00:07 10.42.209.241 FSS:
audit: admin logged out from
10.42.209.241
Mar 17 10:01:51 10.42.209.241 FSS:
audit: admin failed attempt to login from
10.42.209.155 (calling: login)
FCS_TLSC_
EXT.1
Failure to establish a
TLS session
Reason for
failure
Aug 10 10:31:28 localhost FSS
audit[91999]: Sensor <linux90s-sensor>
Error loading CA file:
/FSS/etc/pki/cacert.pem
Aug 10 10:31:28 localhost TLS ERROR:
error:02001002:system library:fopen:No
such file or directory
Aug 10 10:31:28 localhost
error:2006D080:BIO
routines:BIO_new_file:no such file
Aug 10 10:31:28 localhost
error:0B084002:x509 certificate
routines:X509_load_cert_crl_file:system
lib
FCS_TLSC_
EXT.2
Failure to establish a
TLS Session
Reason for
failure
Aug 10 10:22:04 localhost FSS
audit[85359]: Sensor <linux90col> TLS
ERROR: Local: 10.89.184.32, Remote:
10.89.184.31, Failed to obtain peer
certificate
FCS_TLSS_
EXT.1
Failure to establish a
TLS Session
TLS
endpoints
identification
(if applicable),
certificate
depth, Issuer,
Subject (if
applicable),
and reason
for failure
Aug 7 12:01:01 localhost FSS
audit[27394]: Sensor <linux90s-sensor>
TLS ERROR: Local: ::ffff:10.89.184.31,
Remote: ::ffff:10.89.184.32,
error:1408A0C1:SSL
routines:SSL3_GET_CLIENT_HELLO:n
o shared cipher

Fidelis Network Common Criteria Configuration Guide Version 9.0.3 12 www.fidelissecurity.com
SFR
Event
Additional
Information
Sample Log
FCS_TLSS_
EXT.2
Failure to establish a
TLS Session
TLS
endpoints
identification
(if applicable),
certificate
depth, Issuer,
Subject (if
applicable),
and reason
for failure
Aug 11 13:34:33 localhost FSS
audit[42996]: TLS ERROR: Local:
::ffff:10.89.184.31, Remote: ::ffff:10
.89.184.32, Certificate verification error
26 : unsupported certificate,
Aug 11 13:34:33 localhost Depth = 0,
Aug 11 13:34:33 localhost Issuer =
/C=US/ST=MD/L=Bethesda/O=Fidelis
Cybersecurity/OU=Research and De
velpoment/CN=Vadim-Fidelis-
RootCA1/emailAddress=VF-
RootCA1@fidelissecurity.com,
Aug 11 13:34:33 localhost Subject =
/C=US/ST=MD/L=Bethesda/O=Fidelis
Cybersecurity/OU=Research and D
evelpoment/CN=VF-RCA1-
Server1/emailAddress=VF-RCA1-
Server1@fidelissecurity.com
Aug 11 13:34:33 localhost TLS ERROR:
Local: ::ffff:10.89.184.31, Remote:
::ffff:10.89.184.32, error:
140890B2:SSL
routines:SSL3_GET_CLIENT_CERTIFI
CATE:no certificate returned
FIA_AFL.1
Unsuccessful login
attempts limit is met
or exceeded.
Administrator
identity and
the origin of
the login
attempt (e.g.,
IP address).
Sep 8 11:26:18 localhost FSS
audit[106367]: k2admin failed attempt to
login from 10.89.184.30 (calling: login)
Sep 8 11:26:28 localhost FSS
audit[106480]: k2admin failed attempt 1
to login from 10.89.184.30 (calling: login)
Sep 8 11:26:35 localhost FSS
audit[106529]: k2admin failed attempt 2
to login from 10.89.184.30 (calling: login)
Sep 8 11:26:39 localhost FSS
audit[106560]: k2admin failed attempt 3
to login from 10.89.184.30 (calling: login,
3 unsuccessful login attempts detected)
Sep 8 11:53:58 localhost FSS
audit[116873]: k2admin failed attempt 4
to login from 10.89.184.30 (calling: login,
account disabled)
FIA_UIA_EX
T.1
All use of the
identification and
authentication
mechanism
Provided user
identity, origin
of the attempt
Remote:
Feb 18 13:03:14 10.42.209.241 FSS
audit: admin logged on from
192.168.42.5
Local:
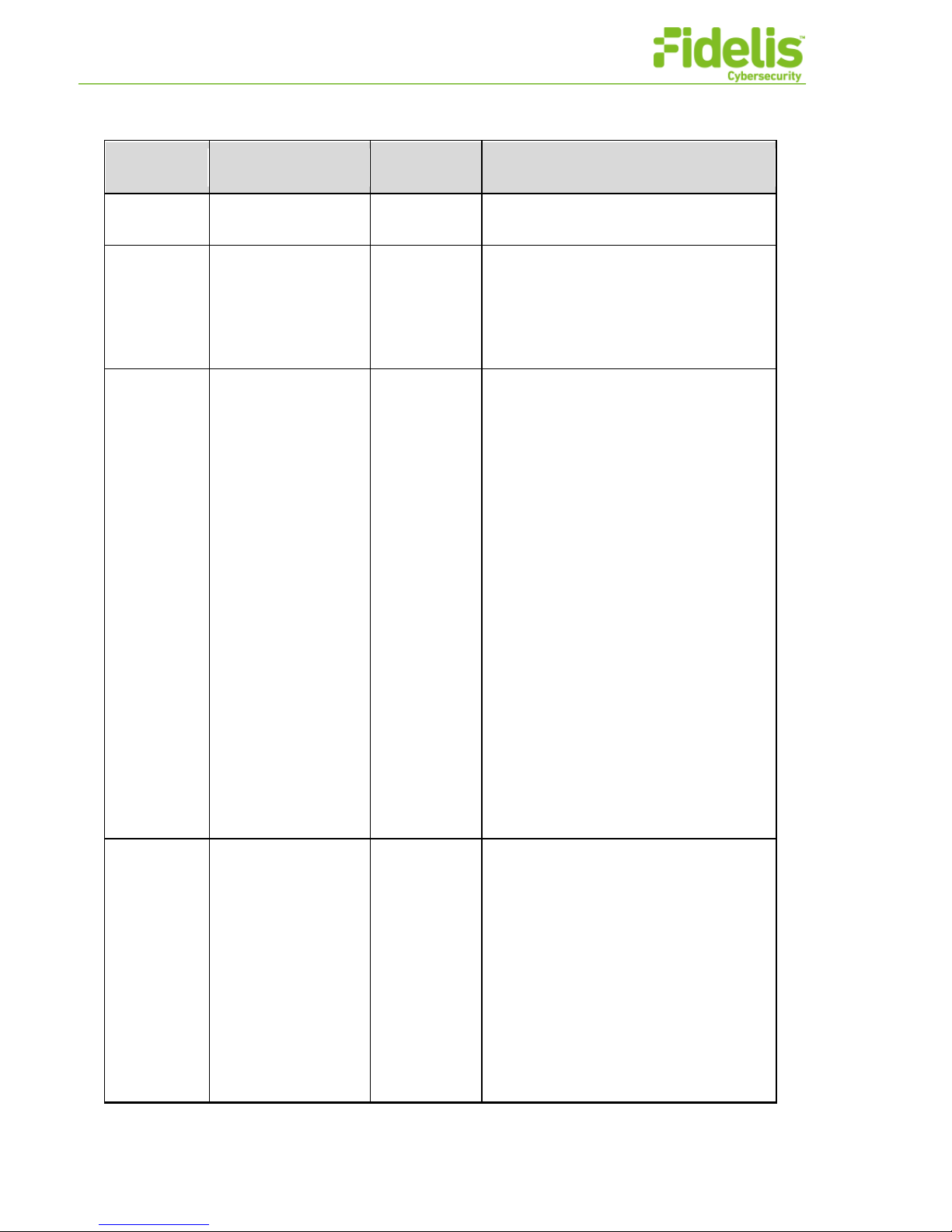
Fidelis Network Common Criteria Configuration Guide Version 9.0.3 13 www.fidelissecurity.com
SFR
Event
Additional
Information
Sample Log
Feb 19 13:16:28 10.42.209.241
localhost login: ROOT LOGIN ON tty1
FIA_UAU_E
XT.2
All use of the
authentication
mechanism.
Administrator
identity and
the origin of
the attempt
(i.e. IP
address).
Sep 7 18:05:24 localhost FSS
audit[104071]: admin logged on from
10.89.184.30
FIA_X509_E
XT.1/Rev
Unsuccessful
attempt to validate a
certificate
TLS
endpoints
identification
(if applicable),
certificate
depth, Issuer,
Subject (if
applicable),
and reason
for failure.
Aug 11 13:34:33 localhost FSS
audit[42996]: TLS ERROR: Local:
::ffff:10.89.184.31, Remote: ::ffff:10
.89.184.32, Certificate verification error
26 : unsupported certificate purpose,
Aug 11 13:34:33 localhost Depth = 0,
Aug 11 13:34:33 localhost Issuer =
/C=US/ST=MD/L=Bethesda/O=Fidelis
Cybersecurity/OU=Research and De
velpoment/CN=Vadim-Fidelis-
RootCA1/emailAddress=VF-
RootCA1@fidelissecurity.com,
Aug 11 13:34:33 localhost Subject =
/C=US/ST=MD/L=Bethesda/O=Fidelis
Cybersecurity/OU=Research and D
evelpoment/CN=VF-RCA1-
Server1/emailAddress=VF-RCA1-
Server1@fidelissecurity.com
Aug 11 13:34:33 localhost TLS ERROR:
Local: ::ffff:10.89.184.31, Remote:
::ffff:10.89.184.32, error:
140890B2:SSL
routines:SSL3_GET_CLIENT_CERTIFI
CATE:no certificate returned
FIA_X509_E
XT.1 /ITT
Unsuccessful
attempt to validate a
certificate
TLS
endpoints
identification
(if applicable),
certificate
depth, Issuer,
Subject (if
applicable),
and reason
for failure.
Aug 11 13:34:33 localhost FSS
audit[42996]: TLS ERROR: Local:
::ffff:10.89.184.31, Remote: ::ffff:10
.89.184.32, Certificate verification error
26 : unsupported certificate purpose,
Aug 11 13:34:33 localhost Depth = 0,
Aug 11 13:34:33 localhost Issuer =
/C=US/ST=MD/L=Bethesda/O=Fidelis
Cybersecurity/OU=Research and De
velpoment/CN=Vadim-Fidelis-
RootCA1/emailAddress=VF-
RootCA1@fidelissecurity.com,
Aug 11 13:34:33 localhost Subject =
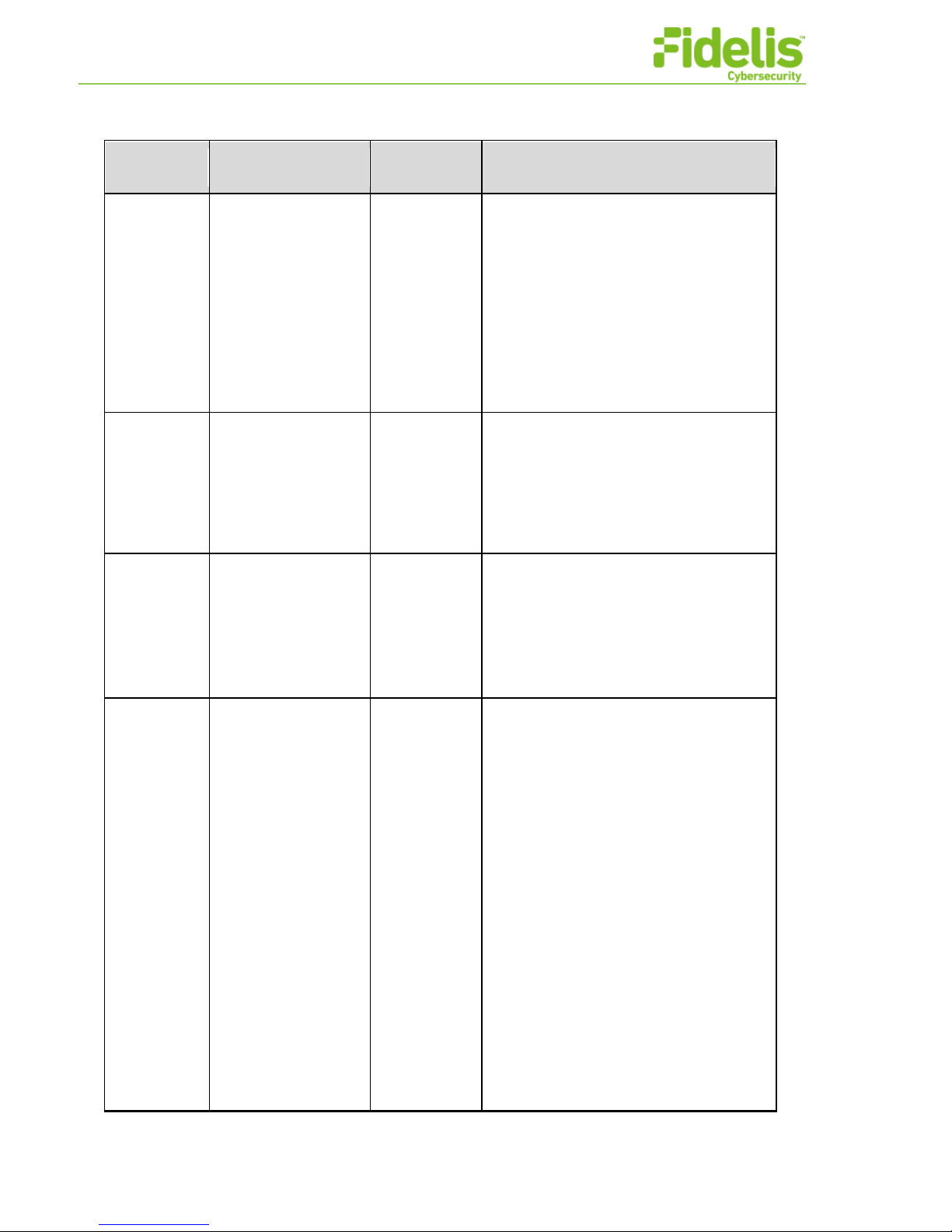
Fidelis Network Common Criteria Configuration Guide Version 9.0.3 14 www.fidelissecurity.com
SFR
Event
Additional
Information
Sample Log
/C=US/ST=MD/L=Bethesda/O=Fidelis
Cybersecurity/OU=Research and D
evelpoment/CN=VF-RCA1-
Server1/emailAddress=VF-RCA1-
Server1@fidelissecurity.com
Aug 11 13:34:33 localhost TLS ERROR:
Local: ::ffff:10.89.184.31, Remote:
::ffff:10.89.184.32, error:
140890B2:SSL
routines:SSL3_GET_CLIENT_CERTIFI
CATE:no certificate returned
FMT_MOF.1
/Manual
Update
Initiation of update.
Identification
of the initiator,
software
update
version and
target(s) of
update.
Feb 21 10:47:03 localhost FSS
audit[32671]: admin started install of
version 9.0.3-20180221 for components:
linux90col
FMT_MTD.1
/CoreData
All management
activities of TSF
data.
TSF data
affected by
the change.
Sep 8 15:07:43 localhost FSS
audit[21670]: /FSS/etc/login.cf: changed
"pw_minlen" from "0" to "10"
Sep 8 15:12:58 localhost FSS
audit[24675]: New file
/FSS/jail/FPDATA/k2admin/contentfinger
print/big.txt created
FMT_MTD.1
/CryptoKeys
Management of
cryptographic keys.
Key
Management
action
(generation,
destruction,
import) and
Critical
Security
Parameter
(CSP)
identification
Sep 8 23:36:50 localhost FSS
audit[22494]: Generated certificate
signing request (CSR) newcsr.pem.
Sep 8 23:36:50 localhost subject:
/O=Fidelis
Cybersecurity/CN=commandpost.fideliss
ecurity.com/
emailAddress=root@commandpost.fideli
ssecurity.com
Sep 8 23:36:50 localhost SHA-256 hash
of the corresponding public key in DER
format:
002bf89ebb085e8bd0b61d466d2d34972
3
ca8c8e9d1574ec40
ac7d032af9b13c
Sep 8 23:35:57 localhost FSS
audit[21861]: Destroyed the certificate
revocation list (CRL).
Sep 8 23:35:57 localhost issuer:
/C=US/ST=Maryland/L=Bethesda/O=Fid
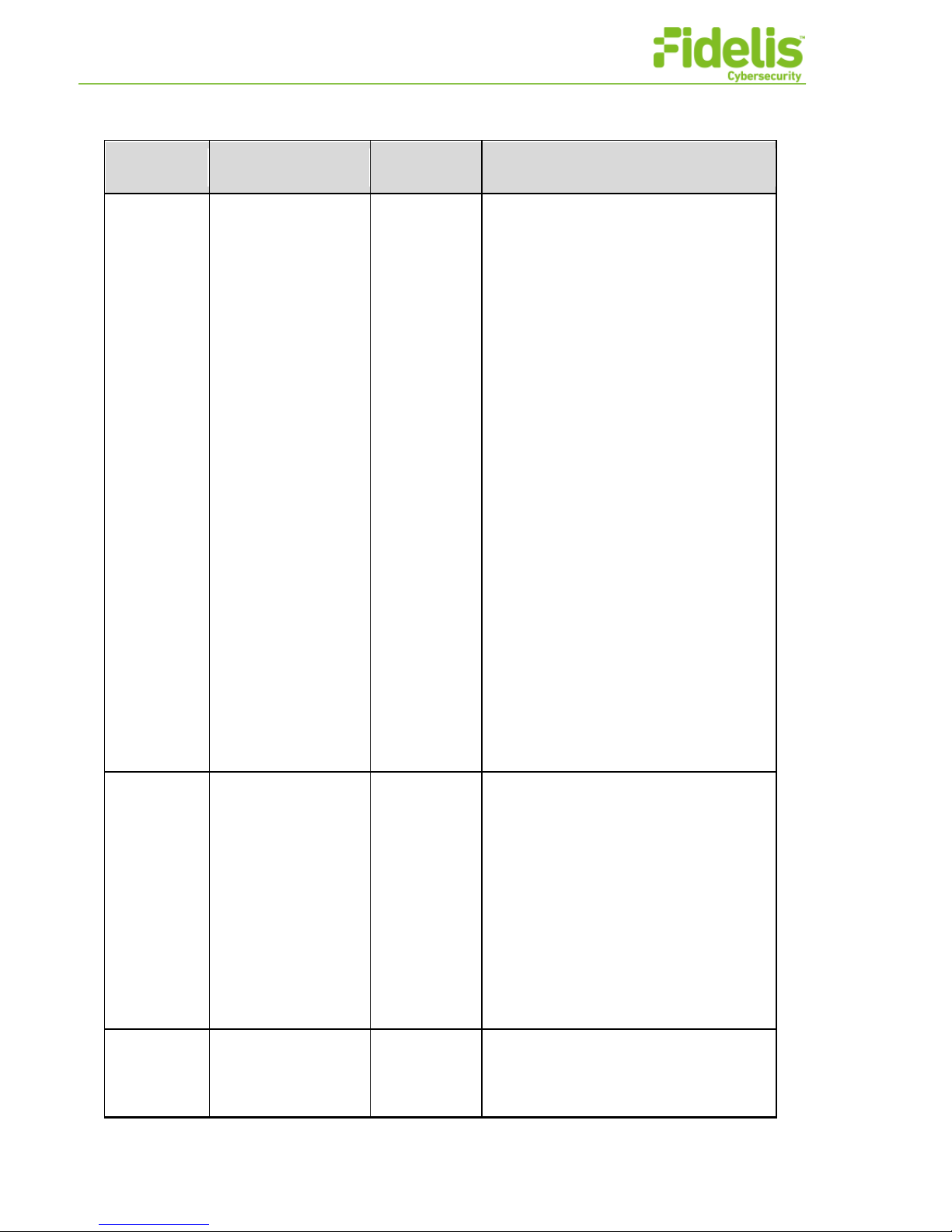
Fidelis Network Common Criteria Configuration Guide Version 9.0.3 15 www.fidelissecurity.com
SFR
Event
Additional
Information
Sample Log
elis Cybersecurity/OU=QA/CN=testca
Sep 8 23:35:57 localhost lastUpdate:
Sep 2 03:06:31 2017 GMT
Sep 8 23:35:57 localhost SHA-256 hash
of the certificate revocation list (CRL) in
DER format:
e3b0c44298fc1c149afbf4c8996fb92427
ae41e4649b934
ca495991b7852b855
Sep 8 23:40:11 localhost FSS
audit[24023]:
Imported the root CA certificate(s).
Sep 8 23:40:11 localhost subject:
/C=US/ST=Maryland/L=Bethesda/O=Fid
elis Cybersecurity/OU=QA/CN=testca
Sep 8 23:40:11 localhost serial:
C749882616318EC3
Sep 8 23:40:11 localhost notBefore: May
24 23:32:06 2017 GMT
Sep 8 23:40:11 localhost notAfter: May
22 23:32:06 2027 GMT
Sep 8 23:40:11 localhost SHA-256
fingerprint:
AA:20:D3:46:F7:5D:08:58:E5:86:6
C:41:E6:14:7B:A1:E4:6B:
FA:A7:EB:38:A1:2F:D1:4B:F8:A4:70:73:
C
B:4C
FPT_ITT.1
Initiation of the
trusted channel.
Termination of the
trusted channel.
Failure of the trusted
channel functions.
Identification
of the initiator
and target of
failed trusted
channels
establishment
attempt.
Mar 29 16:18:37 localhost FSS
audit[77497]: admin unregistered Sensor
linux90col
Mar 29 16:19:35 localhost FSS
audit[77883]: Sensor <linux90col> TLS
SUCCESS: Local: localhost, Remote:
10.89.184.31
Mar 29 16:19:35 localhost FSS
audit[77884]: Sensor <linux90col>
sensor registered successfully
Mar 29 16:19:38 localhost FSS
audit[77917]: admin registered Sensor
linux90col Type: metadatav
FPT_ITT.1/J
oin
Initiation of the
trusted channel.
Termination of the
Identification
of the initiator
and target of
failed trusted
Mar 29 16:18:37 localhost FSS
audit[77497]: admin unregistered Sensor
linux90col

Fidelis Network Common Criteria Configuration Guide Version 9.0.3 16 www.fidelissecurity.com
SFR
Event
Additional
Information
Sample Log
trusted channel.
Failure of the trusted
channel functions.
channels
establishment
attempt.
Mar 29 16:19:35 localhost FSS
audit[77883]: Sensor <linux90col> TLS
SUCCESS: Local: localhost, Remote:
10.89.184.31
Mar 29 16:19:35 localhost FSS
audit[77884]: Sensor <linux90col>
sensor registered successfully
Mar 29 16:19:38 localhost FSS
audit[77917]: admin registered Sensor
linux90col Type: metadatav
FPT_STM_E
XT.1
Discontinuous
changes to time –
either administrator
actuated or changed
via an automated
process.
Distributed
TOE
component
identification
affected by
the time
change, old
time, new
time.
Sep 8 12:19:55 localhost FSS
audit[127431]: Sensor <linux90s-
sensor> Old time: Fri Sep 8 16:19:55
UTC 2017 America/New York. New
time: Fri Sep 8 17:46:40 UTC 2017
EST5EDT. Set by localhost.
FPT_TUD_E
XT.1
Initiation of update
Identification
of the initiator,
software
update
version and
target(s) of
update.
.
Feb 21 10:47:03 localhost FSS
audit[32671]: admin started install of
version 9.0.3-20180221 for components:
linux90col
Result of the update
attempt (success or
failure)
Target of
update
(distributed
TOE
component
identification)
Feb 21 10:49:54 localhost FSS
audit[34208]: Sensor <linux90col>
linux90col:installation success
FTA_SSL_E
XT.1 (if
“terminate
the session”
is selected)
The termination of a
local session by the
session locking
mechanism
Identity of
administrator.
Feb 18 09:48:53 10.42.209.241 FSS
audit: admin’s session has timed out
FTA_SSL.3
The termination of a
remote session by
the session locking
mechanism
Identity of
administrator
Feb 18 09:48:53 10.42.209.241 FSS
audit: admin’s session has timed out
FTA_SSL.4
The termination of an
interactive session
Identity of
administrator
Feb 18 10:31:57 10.42.209.241 FSS
audit: admin logged out from

Fidelis Network Common Criteria Configuration Guide Version 9.0.3 17 www.fidelissecurity.com
SFR
Event
Additional
Information
Sample Log
192.168.42.5
FTP_ITC.1
Initiation of the
trusted channel.
Identification
of the initiator
Mar 17 09:50:25 10.42.209.241 syslog-
ng[26996] : Syslog connection
established; fd=’10’,
server=’AF_INET(10.42.213.205:6514)’ ,
local=’ AF_INET(0.0.0.0:0)’
Termination of the
trusted channel.
None
Mar 17 10:17:37 10.42.209.241 syslog-
ng[28959] syslog-ng shutting down;
version=’3.7.3’
Failure of the trusted
channel functions.
Target of
failed trusted
channels
establishment
attempt
Mar 17 09:50:15 10.42.209.241 syslog-
ng[26996] : Syslog connection failed;
fd=’10’,
server=’AF_INET(10.42.213.205:6514)’ ,
error=’Connection refused (111)’,
time_reopen=’10’
FTP_TRP.1/
Admin
Initiation of the
trusted channel.
Identification
of the claimed
user identity.
Mar 17 09:52:00 10.42.209.241 FSS:
audit: admin logged on from
10.42.29.155
Termination of the
trusted channel.
Identification
of the claimed
user identity.
Mar 17 10:00:07 10.42.209.241 FSS:
audit: admin logged out from
10.42.209.241
Failure of the trusted
channel functions.
Identification
of the claimed
user identity.
Mar 17 10:01:51 10.42.209.241 FSS:
audit: admin failed attempt to login from
10.42.209.155 (calling: login)
Component Processes and Descriptions
The table below lists all Fidelis Network processes that handle network traffic.
Table 3. Traffic Handling Processes and Descriptions
Component
Process Name
Privilege
Description
All
sshd
Runs as root
Secure shell daemon for remote
access
All
rconfigd
Runs as root
Serves as the Remote
Configuration Daemon that is
required for communication
between components
Table of contents
Other Fidelis Network Hardware manuals

Fidelis
Fidelis Collector Controller 10G User manual

Fidelis
Fidelis FDH-3000 User manual

Fidelis
Fidelis Deception Decoy Server FDH-1000-C User manual

Fidelis
Fidelis Network Collector SA User manual

Fidelis
Fidelis Network Collector SA Rev-1 Series User manual

Fidelis
Fidelis Network CommandPost User manual

Fidelis
Fidelis CommandPost+ User manual
Popular Network Hardware manuals by other brands

Matrix Switch Corporation
Matrix Switch Corporation MSC-CP32X32E product manual
INNOSILICON
INNOSILICON T2TS-26T BTC user manual

Alcatel-Lucent
Alcatel-Lucent 7310 installation manual

WESTERSTRAND
WESTERSTRAND 123383-01 manual

Firetide
Firetide HotPort 5020-LNK installation guide

Thecus
Thecus N5200B PRO user manual