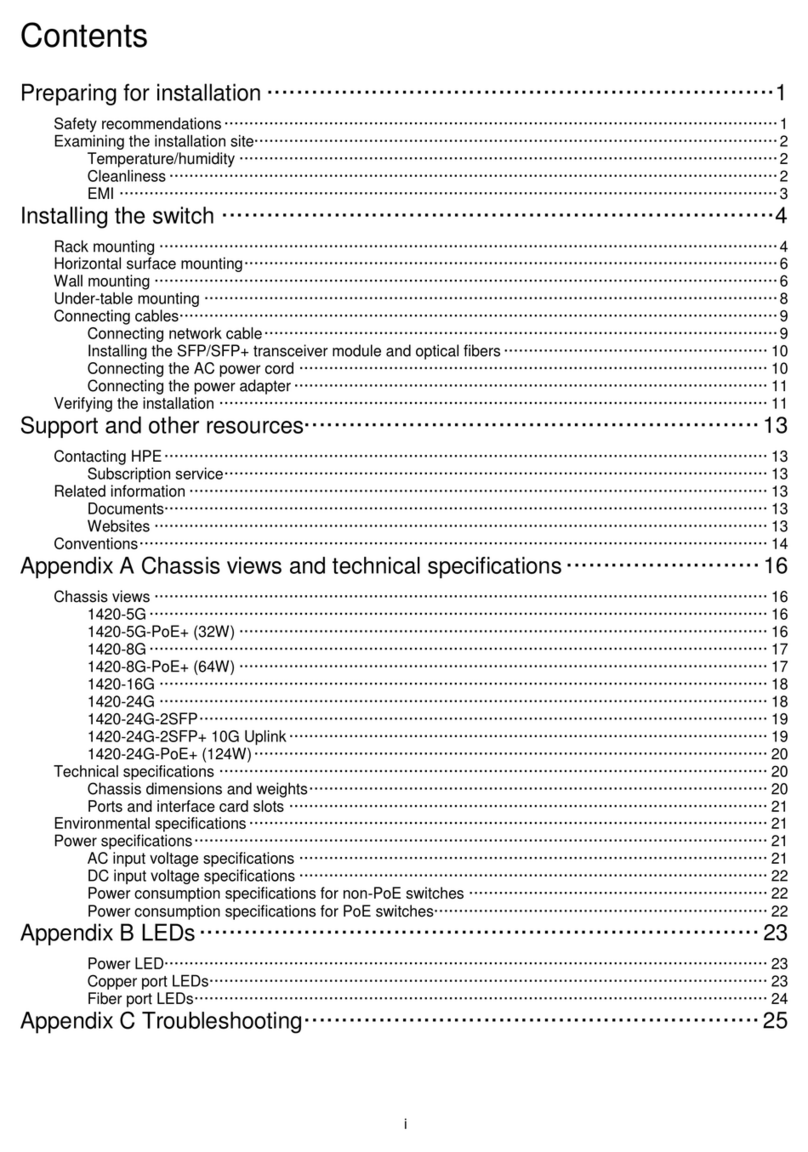
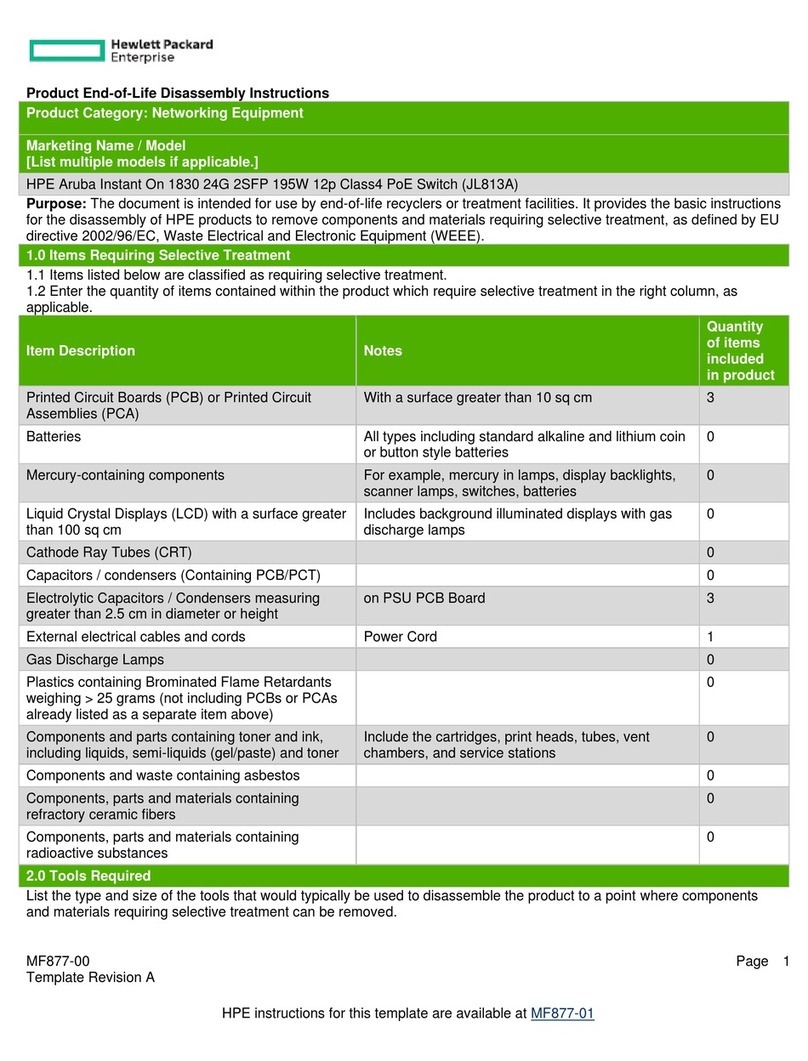
iv
Configuration procedure ··································································································· 112
Configuring path costs of ports·································································································· 112
Specifying a standard for the device to use when it calculates the default path cost ······················· 113
Configuring path costs of ports ··························································································· 115
Configuration example······································································································ 115
Configuring the port priority ······································································································ 116
Configuring the port link type ···································································································· 116
Configuration restrictions and guidelines ·············································································· 116
Configuration procedure ··································································································· 117
Configuring the mode a port uses to recognize and send MSTP frames············································· 117
Enabling outputting port state transition information······································································· 118
Enabling the spanning tree feature ···························································································· 118
Enabling the spanning tree feature in STP/RSTP/MSTP mode·················································· 118
Enabling the spanning tree feature in PVST mode·································································· 119
Performing mCheck················································································································ 119
Configuration restrictions and guidelines ·············································································· 119
Performing mCheck globally ······························································································ 119
Performing mCheck in interface view ··················································································· 120
Disabling inconsistent PVID protection ······················································································· 120
Configuring Digest Snooping ···································································································· 120
Configuration restrictions and guidelines ·············································································· 121
Configuration procedure ··································································································· 121
Digest Snooping configuration example ··············································································· 121
Configuring No Agreement Check ····························································································· 122
Configuration prerequisites································································································ 123
Configuration procedure ··································································································· 124
No Agreement Check configuration example ········································································· 124
Configuring TC Snooping········································································································· 124
Configuration restrictions and guidelines ·············································································· 125
Configuration procedure ··································································································· 125
Configuring protection features ································································································· 126
Configuring BPDU guard··································································································· 126
Enabling root guard ········································································································· 127
Enabling loop guard ········································································································· 127
Configuring port role restriction··························································································· 128
Configuring TC-BPDU transmission restriction······································································· 128
Enabling TC-BPDU guard ································································································· 129
Enabling BPDU drop ········································································································ 129
Enabling PVST BPDU guard······························································································ 130
About dispute guard········································································································· 130
Enabling the device to log events of detecting or receiving TC BPDUs ·············································· 131
Enabling BPDU transparent transmission on a port ······································································· 131
Enabling SNMP notifications for new-root election and topology change events ·································· 132
Displaying and maintaining the spanning tree ·············································································· 132
Spanning tree configuration example ························································································· 133
MSTP configuration example ····························································································· 133
PVST configuration example······························································································ 137
Configuring loop detection······························································ 141
Overview······························································································································ 141
Loop detection mechanism································································································ 141
Loop detection interval ····································································································· 142
Loop protection actions····································································································· 142
Port status auto recovery ·································································································· 142
Loop detection configuration task list·························································································· 143
Enabling loop detection ··········································································································· 143
Enabling loop detection globally ························································································· 143
Enabling loop detection on a port························································································ 143
Setting the loop protection action······························································································· 144
Setting the global loop protection action ··············································································· 144
Setting the loop protection action on a Layer 2 Ethernet interface ·············································· 144
Setting the loop protection action on a Layer 2 aggregate interface ············································ 144