5
Copyright © 2000 - 2005 KEMP Technologies, Inc. All Rights Reserved.
1. API for Agent Based Adaptive Balancing .....................................................................................32
2. Http Server Configuration for Cookie Support..............................................................................33
3. MIB-tree................................................................................................................................34
II. INSTALLATION AND CONFIGURATION GUIDE ..........................................................................34
A. Before Getting Started...............................................................................................................34
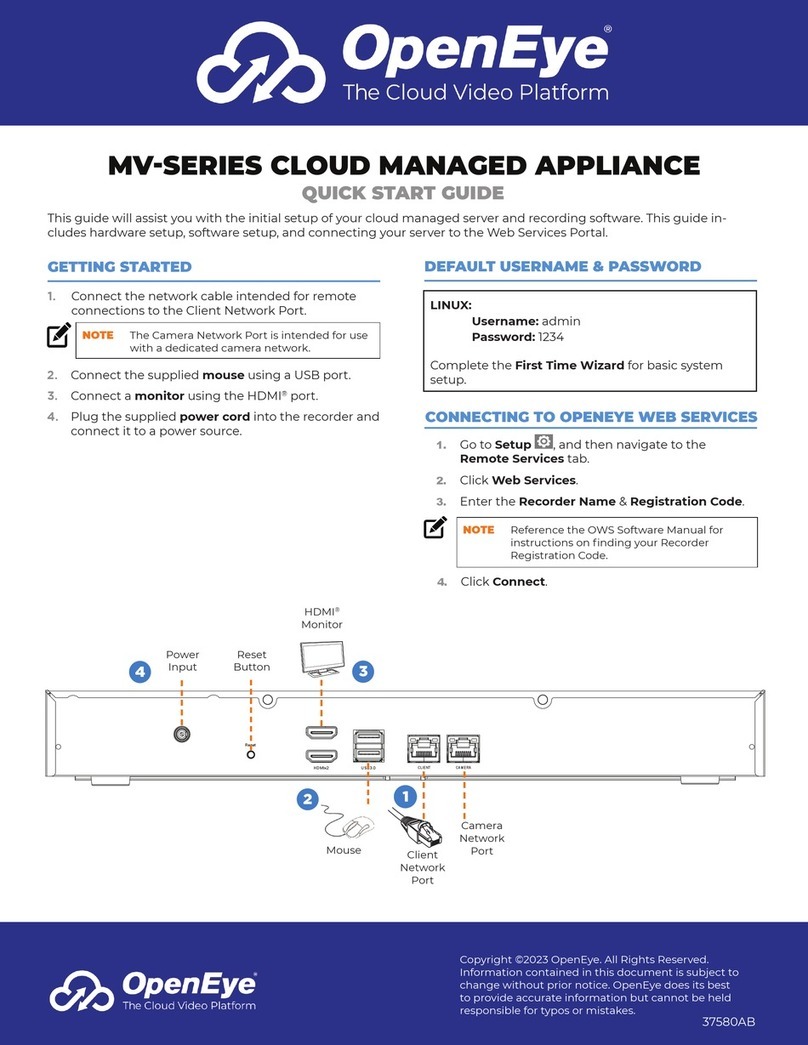
1. The LoadMaster Appliance........................................................................................................35
1.1. Delivery Content ..................................................................................................................35
1.2. LoadMaster 1500 Hardware ...................................................................................................35
2. Connecting the Hardware.........................................................................................................35
B. Initial Setup of your LoadMaster Single Unit (non-HA)..............................................................35
1. Login and License Key .............................................................................................................35
C. Initial Setup of a LoadMaster High Availability (HA) Cluster......................................................36
1. Login and License Key .............................................................................................................36
2. Configuring the second LoadMaster............................................................................................36
D. Quick Setup................................................................................................................................37
E. Main Menu ..................................................................................................................................38
1. Configuration Menu basics........................................................................................................38
1.1. Quick Setup.........................................................................................................................39
2. Service Management (CLI) .......................................................................................................39
3. Local Administration................................................................................................................39
3.1. Set Password.......................................................................................................................39
3.2. Set Date/Time .....................................................................................................................39
3.3. Set Keyboard Map.................................................................................................................39
3.4. Backup/Restore ...................................................................................................................40
3.5. Remote Access Control..........................................................................................................40
4. Basic Setup............................................................................................................................40
4.1. Network configuration...........................................................................................................40
4.2. Hostname Configuration........................................................................................................41
4.3. DNS configuration ................................................................................................................41
5. Extended Configuration............................................................................................................41
5.1. Interface Control..................................................................................................................41
5.2. Enable/Disable S-NAT ...........................................................................................................41
5.3. Syslogd Configuration...........................................................................................................42
5.4. SNMP metrics ......................................................................................................................42
5.5. SNMP traps .........................................................................................................................42