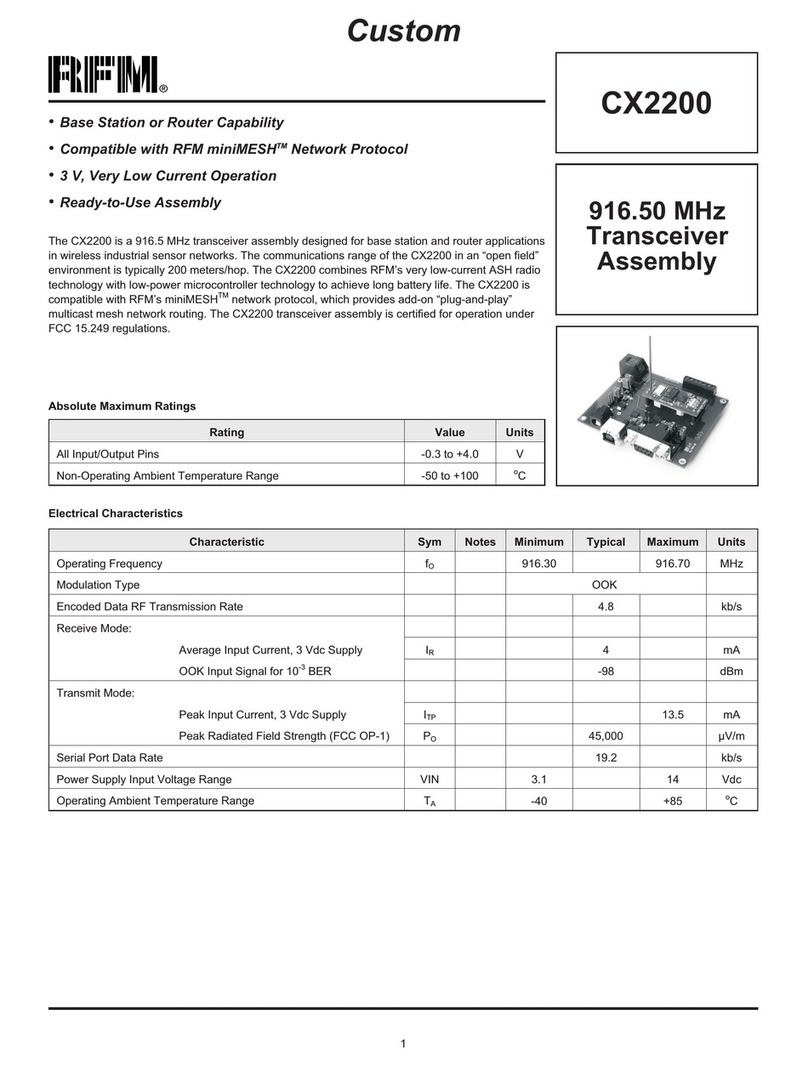
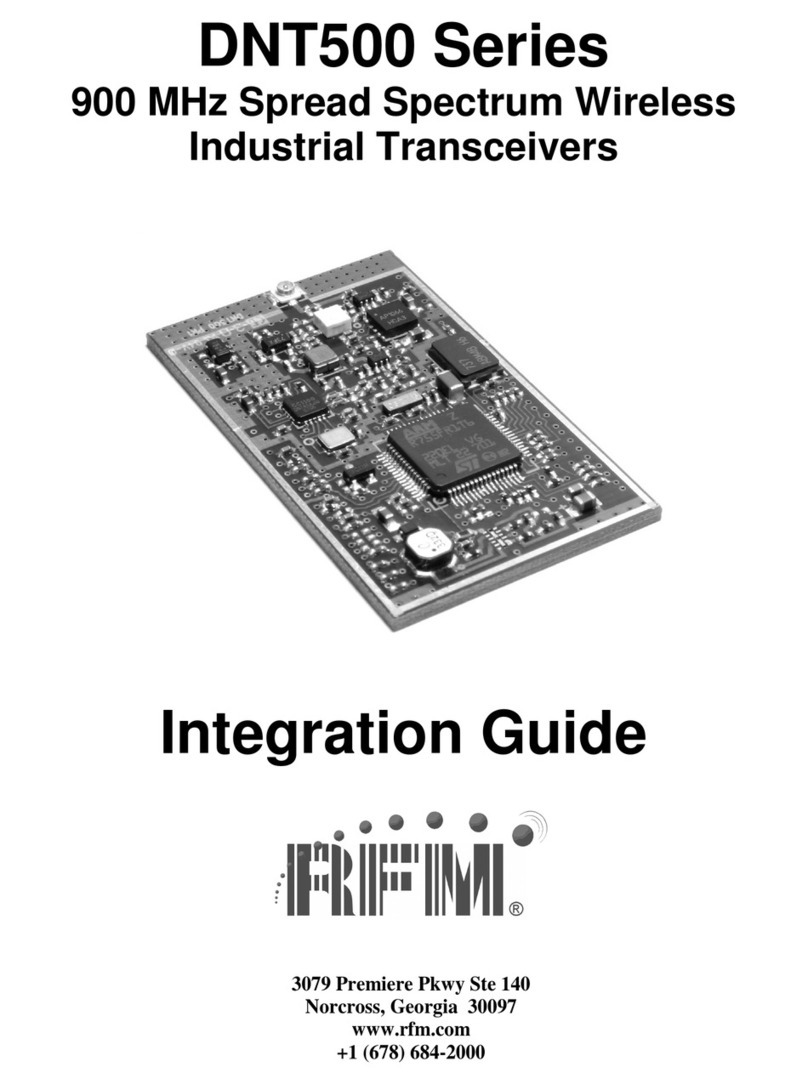
www.RFM.com Technical support +1.678.684.2000 Page 3 of 96
©2009-2010 by RF Monolithics, Inc. E-mail: tech_sup@rfm.com DNT900 - 08/16/10
Table of Contents
1.0 Introduction ...................................................................................................................................... 5
1.1 Why Spread Spectrum? ............................................................................................................... 5
1.2 Frequency Hopping versus Direct Sequence............................................................................... 6
2.0 DNT900 Radio Operation................................................................................................................ 7
2.1 Network Synchronization and Registration .................................................................................. 7
2.2 Authentication............................................................................................................................... 8
2.3 Serial Port Modes......................................................................................................................... 9
2.4 SPI Port Modes ............................................................................................................................ 9
2.5 RF Data Communications .......................................................................................................... 10
2.6 RF Transmission Error Control................................................................................................... 10
2.7 Transmitter Power Management................................................................................................ 10
2.8 Network Configurations.............................................................................................................. 11
2.8.1 Point-to-Point Network Operation ........................................................................................... 11
2.8.2 Point-to-Multipoint Network Operation.................................................................................... 11
2.8.3 Multipoint Peer-to-Peer Network Operation............................................................................ 12
2.8.4 Tree-Routing System Operation ............................................................................................. 12
2.9 Full-Duplex Serial Data Communications................................................................................... 12
2.10 Channel Access.......................................................................................................................... 12
2.10.1 Polling Mode ........................................................................................................................... 13
2.10.2 CSMA Mode............................................................................................................................ 14
2.10.3 TDMA Modes .......................................................................................................................... 15
2.11 Point-to-Point and Point-to-Multipoint Networks......................................................................... 15
2.11.1 TDMA Throughput................................................................................................................... 16
2.11.2 Polling Throughput.................................................................................................................. 16
2.11.3 CSMA Throughput................................................................................................................... 17
2.11.4 Latency.................................................................................................................................... 18
2.11.5 Configuration Validation.......................................................................................................... 18
2.12 Tree-Routing Systems................................................................................................................ 20
2.12.1 Example Tree-Routing System............................................................................................... 20
2.12.2 Tree-Routing System Networks.............................................................................................. 22
2.12.3 Tree-Routing System Addressing........................................................................................... 23
2.12.4 Tree-Routing System Implementation Options....................................................................... 24
2.13 Serial Port Operation.................................................................................................................. 25
2.14 SPI Port Operation ..................................................................................................................... 26
2.15 Sleep Modes............................................................................................................................... 29
2.16 Encryption................................................................................................................................... 31
2.17 Synchronizing Co-located Bases ............................................................................................... 31
3.0 DNT900 Hardware......................................................................................................................... 32
3.1 Specifications ............................................................................................................................. 33
3.2 Module Interface......................................................................................................................... 34
3.3 DNT900 Antenna Connector...................................................................................................... 35
3.4 Input Voltages............................................................................................................................. 36
3.5 ESD and Transient Protection.................................................................................................... 36
3.6 Interfacing to 5 V Logic Systems................................................................................................ 36
3.7 Power-On Reset Requirements ................................................................................................. 37
3.8 Mounting and Enclosures........................................................................................................... 37
3.9 Labeling and Notices.................................................................................................................. 37