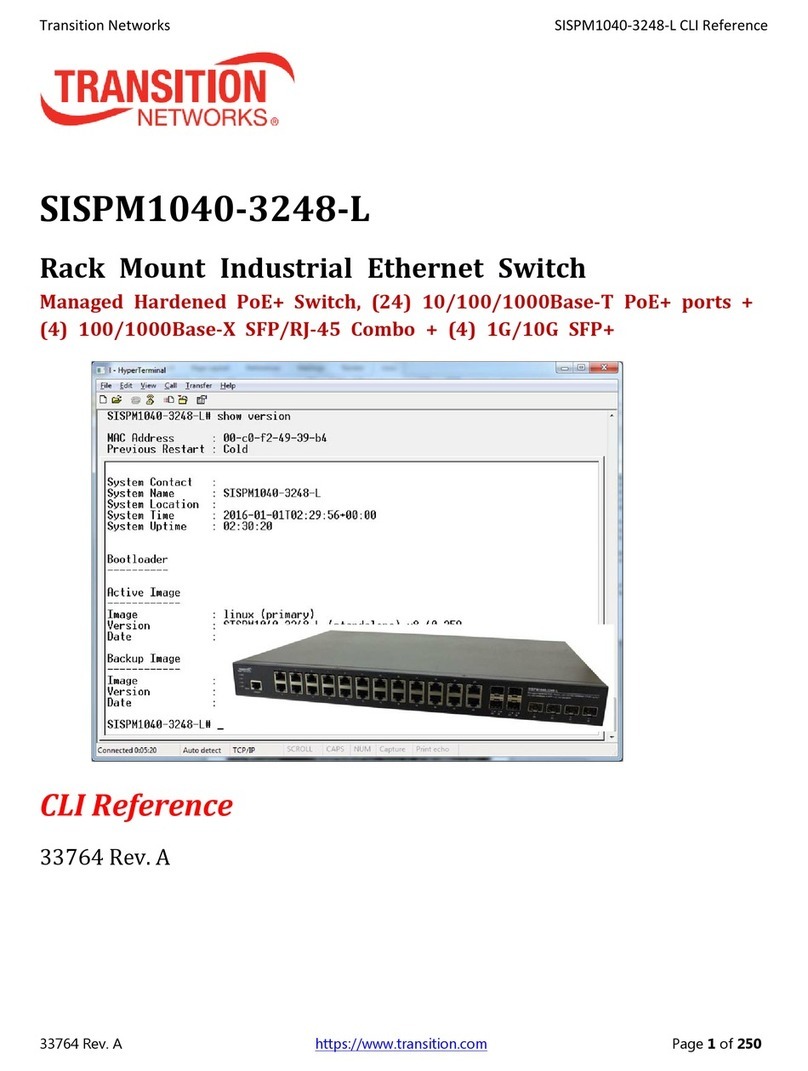
TransitionNetworks SISPM1040‐3248‐LWebUserGuide
33763 Rev. A https://www.transition.com Page 6of 413
11‐1.2SnoopingTable.....................................................................................................................................215
11‐1.3DetailedStatistics................................................................................................................................216
11‐2Relay............................................................................................................................................................218
11‐2.1Configuration.......................................................................................................................................218
11‐2.2Statistics...............................................................................................................................................220
11‐3Server..........................................................................................................................................................222
11‐3.1Configuration.......................................................................................................................................222
11‐3.2Status...................................................................................................................................................224
Chapter12–Security.....................................................................................................................................225
12‐1Management...............................................................................................................................................225
12‐1.1Account................................................................................................................................................225
12‐1.2PrivilegeLevels.....................................................................................................................................227
12‐1.3AuthMethod........................................................................................................................................229
12‐1.4AccessMethod.....................................................................................................................................231
12‐1.5HTTPS...................................................................................................................................................233
12‐2802.1X.........................................................................................................................................................235
12‐2.1Configuration.......................................................................................................................................235
12‐2.2Status...................................................................................................................................................243
12‐3IPSourceGuard..........................................................................................................................................245
12‐3.1Configuration.......................................................................................................................................245
12‐3.2StaticTable...........................................................................................................................................247
12‐3.3DynamicTable......................................................................................................................................248
12‐4ARPInspection............................................................................................................................................250
12‐4.1Configuration.......................................................................................................................................250
12‐4.2VLANConfiguration.............................................................................................................................252
12‐4.3StaticTable...........................................................................................................................................254
12‐4.4DynamicTable......................................................................................................................................255
12‐5PortSecurity................................................................................................................................................257
12‐5.1Configuration.......................................................................................................................................257
12‐5.2Status...................................................................................................................................................260
12‐6RADIUS........................................................................................................................................................263
12‐6.1Configuration.......................................................................................................................................263
12‐6.2Status...................................................................................................................................................265
12‐7TACACS+......................................................................................................................................................270
Chapter13–AccessControl..........................................................................................................................272
13‐1PortsConfiguration.....................................................................................................................................272
13‐2RateLimiters...............................................................................................................................................274
13‐3AccessControlList......................................................................................................................................276
13‐4ACLStatus...................................................................................................................................................287
Chapter14–SNMP........................................................................................................................................289
14‐1Configuration..............................................................................................................................................289
14‐2SNMPv3.......................................................................................................................................................291