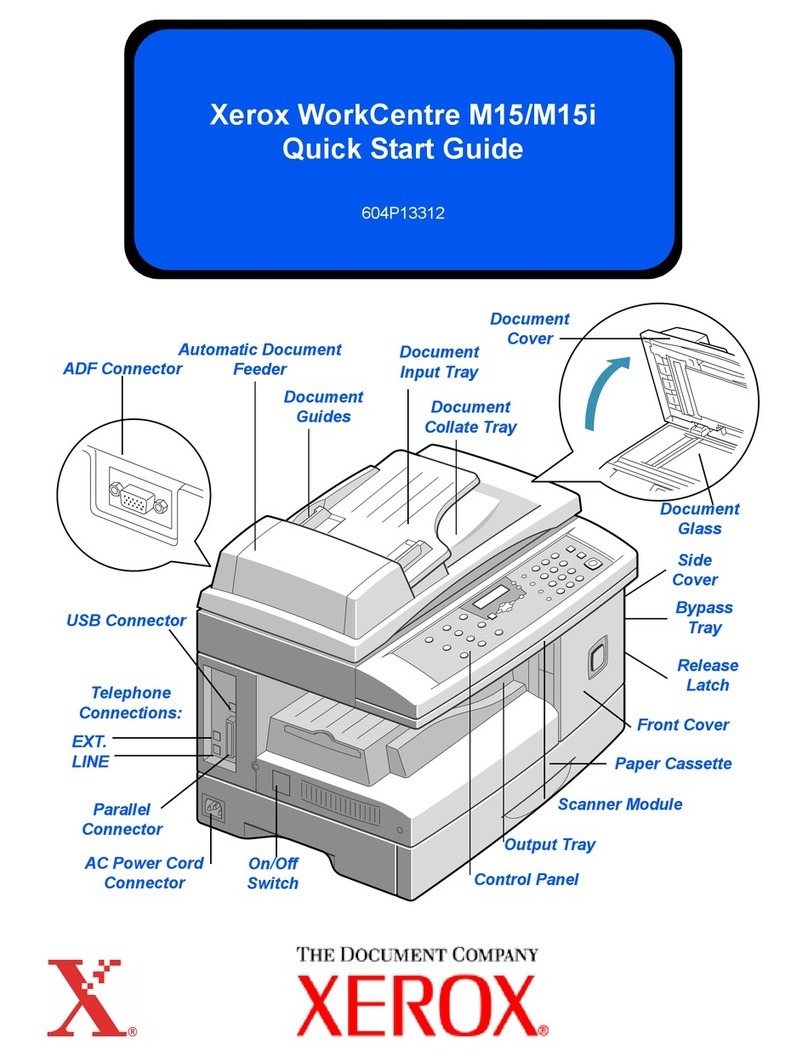
Extraneous process termination events (Event 50) may be recorded in the Audit Log when the device is rebooted or
upon a Power Down / Power Up. Extraneous security certificate completion status
(Created/Uploaded/Downloaded) events (Event 38) may also be recorded.
Download and review the Audit Log on a daily basis. In downloading the Audit Log ensure that Audit Log records are
protected after they have been exported to an external trusted IT product and that the exported records are only
accessible by authorized individuals.
If a system interruption such as power loss occurs a job in process may not be fully written to the hard disk drive(s). In
that case any temporary data created will be overwritten during job recovery but a corresponding record for the job
may not be recorded in the completed job log or audit log.
j. Be careful not to create an IP Filtering rule that rejects incoming TCP traffic from all addresses with source port set to 80;
this will disable the Web UI. Also, configure IP filtering so that traffic to open ports from external users (specified by subnet
mask) is dropped and so that following ports for web services are closed: tcp ports 53202, 53303, 53404 and tcp/udp port
3702.
l. Users should be aware that correct remote repository document pathnames for the receipt of workflow scanning jobs
should start with one ‘\’ as opposed to the two ‘\’s.
m. Users should be provided with appropriate training on how to use the device in a secure manner before being assigned user
accounts to access the device.
k. Before upgrading software on the device via the Manual/Automatic Customer Software Upgrade, please check for the latest
certified software versions. Otherwise, the machine may not remain in its certified configuration.
l. The device should be installed in a standard office environment. Office personnel should be made aware of authorized
service calls (for example through appropriate signage) in order to discourage unauthorized physical attacks such as
attempts to remove the internal hard disk drive(s). Ensure that office personnel are made aware to pick up the outputs of
print and copy jobs in a timely manner.
m. Caution: The device allows an authenticated System Administrator to disable functions like Image Overwrite Security that
are necessary for secure operation. Periodically review the configuration of all installed machines in your environment to
verify that the proper evaluated configuration is maintained.
n. System Administrators should avoid opening emails and attachments from unknown sources unless the emails and
attachments have been properly scanned for viruses, malware, etc.
o. System Administrators and users should logoff immediately after using the Web UI. They should also not allow their
browser to either save their username/password or “remember” their login.
IV. Secure Operation of Device Services/Functions Not Part of the Evaluated Configuration
a. Change the SNMPv1/v2c public/private community strings from their default string names to random un-guessable string
names of at least 8 characters in length.
b. To enable SNMPv3 follow the instructions for “Configuring SNMPv3” in Chapter 3 of the SAG.
c. Customers should sign up for the RSS
subscription service available via the Xerox Security Web Site (Security@Xerox) at
www.xerox.com/security that permits customers to view the latest Xerox Product Security Information and receive timely
reporting of security information about Xerox products, including the latest security patches.
d. Customers who encounter or suspect software problems should immediately contact the Xerox Customer Support Center to
report the suspected problem and initiate the SPAR (Software Problem Action Request)
process for addressing problems
found by Xerox customers.
e. Depending upon the configuration of the device, two IPv4 addresses, a primary IPv4 address and a secondary IPv4 address,
may be utilized. The System Administrator selects whether the primary IPv4 address will be obtained statically or
dynamically via DHCP from the TCP/IP page on the Web UI. The second IPv4 address is assigned via APIPA when the
System Administrator enables the ‘Self Assigned Address’ option from the IP (Internet Protocol) page on the Web UI. If
the ‘Self Assigned Address’ option is enabled (which is the default case), this secondary IPv4 address will not be visible to the
SA
. The ‘Self Assigned Address’ option from the Web UI TCP/IP page should be disabled unless either APIPA is used or
Apple Rendezvous/Bonjour support is required.
Really Simple Syndication –A lightweight XML format for distributing news headlines and other content on the Web. Details for signing up for this
RSS Service are provided in the Security@Xerox RSS Subscription Service guide posted on the Security@Xerox site at
http://www.xerox.com/go/xrx/template/009.jsp?view=Feature&ed_name=RSS_Security_at_Xerox&Xcntry=USA&Xlang=en_US.
A SPAR is the software problem report form used internally within Xerox to document customer-reported software problems found in products in
the field.
The primary IPv4 address will always be displayed on the Configuration Report that can be printed for the device.