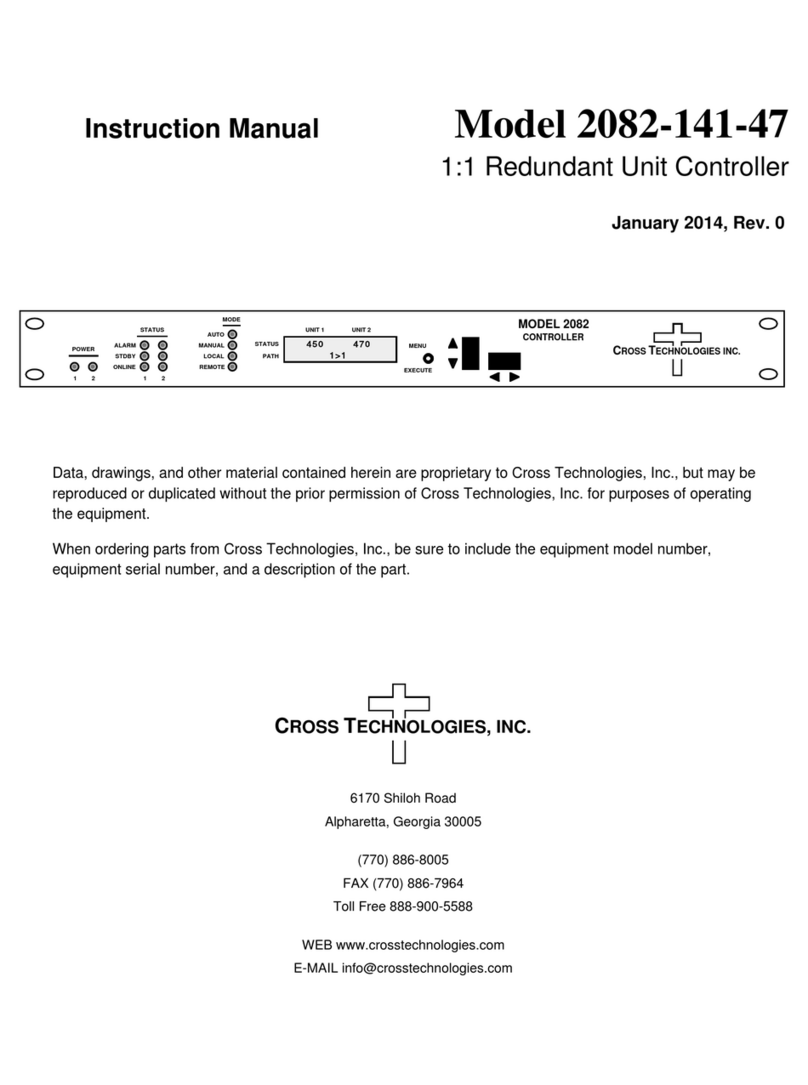
Fiery X3eTY 35C-KM User manual

Image Controller
Fiery X3eTY 35C-KM
NetworkScanner Operations
Copier NetworkFunctions
User's
Guid
4037-7163-01

Introduction
Introduction
Thank you for choosing this machine.
This User's Guide contains descriptions
of
the network scanning functions
and operations that can be used from optional image controller Fiery X3eTY
35C-KM and the networkfunctions that can be used from the copier when
the Fiery X3eTY 35C-KM
is
installed. To ensure the best possible perform-
ance and mosteffective use
of
the machine, read this manual thoroughly. Af-
ter reading this User's Guide, store it in the designated holderfor quick
reference when problems
or
questions arise during operation.
Views
of
the actual equipment may be slightly differentfrom the illustrations
used in this manual.
Fiery X3eTY 35C-KM x-1

Introduction
Trademarks and Registered Trademarks
x-2
Apple and Macintosh are registered trademarks
of
Apple Computer, Inc.
Ethernet
is
a registered trademark
of
Xerox Corporation.
Microsoft, Windowsand Windows NTare registered trademarks
of
Microsoft
Corporation.
Postscript is a registered trademark
of
Adobe Systems, Inc.
EFI,
Fiery and the Fiery logo are registered trademarks
of
Electronics for Im-
aging, Inc. and are legally registered in the United States and othercountries.
The Electronics for Imaging logo, Fiery Remote Scan, Fiery WebScan, and
Fiery WebTools are trademarks
of
Electronics for Imaging, Inc.
OpenSSL Statement
OpenSSL License
Copyright © 1998-2000 The OpenSSL Project. All rights reserved.
Redistribution and use
in
source and binary forms, with
or
without modifica-
tion, are permitted provided that the following conditions are met:
1.
Redistributions of source code must retain the above copyright notice,
this list
of
conditions and the following disclaimer.
2.
Redistributions
in
binary form
must
reproduce the above copyright no-
tice, this list
of
conditions and the following disclaimer in the documen-
tation and/or other materials provided with the distribution.
3.
All advertising materials mentioning features
or
use
of
this software must
display the following acknowledgment:
"This product includes software developed by the OpenSSL Project for
use
in
the OpenSSL Toolkit. (http://www.openssl.org/)"
4.
The names "OpenSSLToolkit" and "OpenSSL Project" must notbe used
to
endorse
or
promote products derived from this software without prior
written permission. For written permission, please contact openssl-
5.
Products derived from this software may not be called "OpenSSL" nor
may "OpenSSL" appear in their names without prior written permission
of
the OpenSSL Project.
Fiery X3eTY 35C-KM

Introduction
6.
Redistributions
of
any form whatsoever must retain the following
ac-
knowledgment:
"This product includes software developed by the OpenSSL Project
for
use in the OpenSSL Toolkit (http://www.openssl.org/)"
THIS SOFTWARE
IS
PROVIDED BY THE OpenSSL PROJECT "AS IS" AND
ANY EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIM-
ITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FIT-
NESS
FOR
A PARTICULAR PURPOSE ARE DISCLAIMED.
IN
NO EVENT
SHALL THE OpenSSL PROJECT OR
ITS
CONTRIBUTORS
BE
LIABLE FOR
ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY,
OR
CON-
SEQENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCURE-
MENT OF SUBSTITUTE GOODS
OR
SERVICES; LOSS OF
USE,
DATA, OR
PROFITS;
OR
BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON
ANYTHEORY
OF
LIABILITY, WHETHER
IN
CONTRACT, STRICT LIABILITY,
OR TORT (INCLUDING NEGLIGENCE
OR
OTHERWISE) ARISING
IN
ANY
WAY OUT
OF
THE USE OF THIS SOFTWARE,
EVEN
IF
ADVISED
OF
THE
POSSIBILITY OF SUCH DAMAGE.
This product includes cryptographic software written
by
Eric Young
by
Tim
Hud-
son ([email protected]).
OriginalSSLeayLicense
Copyright©
1995-1998 Eric Young ([email protected]) All rights reserved.
This package is an SSL implementation written
by
Eric Young (eay@crypt-
soft.com).
The implementation was written so as
to
conform with Netscapes SSL.
This library is free
for
commercial and non-commercial useas long
as
the
fol-
lowing conditions are aheared to. The following conditions apply
to
all
code
found in this distribution, be itthe RC4,
RSA,
Ihash, DES, etc., code; notjust
the SSL code.
The SSL documentation included with this distribution is covered by
the
same copyright terms except that the holder is Tim Hudson (tjh@crypt-
soft.com).
Copyright remains Eric Young's, and
as
such any Copyright notices
in
the
code are not
to
be removed. Ifthis package is used in a product, Eric Young
should be given attribution as the author
of
the parts
of
the
library used. This
can be in the form
of
a textual message
at
program startup
or
in
documen-
tation (online ortextual) provided with the package.
Redistribution and use
in
source and binary forms, with
or
without modifica-
tion, are permitted provided that the following conditions are met:
1.
Redistributions
of
source code must retain the copyright notice, this list
of
conditions and the following disclaimer.
2.
Redistributions
in
binary form must reproduce the above copyright
no-
tice, this list
of
conditions and the following disclaimer in the documen-
tation and/or other materials provided with the distribution.
Fiery X3eTY 35C-KM
x-3

x-4
Introduction
3.
All advertising materials mentioning features
or
use
of
this software must
display the following acknowledgement:
"This product includes cryptographic software written
by
Eric Young
The word 'cryptographic' can be leftout ifthe rouines from the library be-
ing used are not cryptographic related :-).
4.
If you include any Windows specific code (or a derivative thereof) from
the
apps
directory (application code) you must include an acknowledge-
ment:
"This product includes software written
by
Tin Hudson (tjh@crypt-
soft.com)"
THIS SOFTWARE IS PROVIDED BY ERIC YOUNG "AS IS" AND ANY
EX-
PRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED
TO,
THE IMPLIED WARRANTIES OF MERCHANTABILITYAND FITNESS
FOR
A
PARTICULAR PURPOSE ARE DISCLAIMED.
IN
NO EVENT SHALLTHE AU-
THOR OR CONTRIBUTORS BE LIABLE
FOR
ANY DIRECT, INDIRECT, INCI-
DENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
(INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE
GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILI-
TY,
WHETHER
IN
CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE OR OTHERWISE) ARISING
IN
ANY WAY OUT OF THE
USE
OF THIS SOFTWARE,
EVEN
IF
ADVISED
OF
THE POSSIBILITY OF SUCH
DAMAGE.
The licence and distribution terms
for
any publically available version or
de-
rivative
of
this
code
cannot be changed. i.e. this code cannot simply be
cop-
ied and
put
under another distribution licence [including the GNU Public
Licence.]
All other
product
names are either trademarks
or
registered trademarks of
their respective companies.
In
order
to
incorporate improvements in the product, the content
of
this man-
ual is subject
to
change without notice.
Fiery X3eTY 35C-KM

Introduction
Contents
Trademarks
and
Registered
Trademarks
......................................
x-2
Contents ............................................................................................
x-5
About This Manual ..........................................................................x-12
Structure
of
the Manual ................................................................x-12
Notation .........................................................................................x-12
Explanation
of
Manual
Conventions
.............................................
x-14
1.1
Environment
Required
for
Using
the
Scan
Functions
...................
1-2
1.2 Available
Scanning
Functions
.........................................................
1-3
Sending the Scanned Data in
an
E-Mail Message ......................... 1-3
Sending the Scanned Data
as
Files
(FTP)
......................................
1-4
Sending the Scanned Data
to
a Computer on the Network
(SMB) .............................................................................................
1-5
Saving Scanned Data in Boxes on the Hard Disk
(Save
in
Mailbox) ............................................................................ 1-6
1.3
Settings
for
Using
Network/Scanning
Functions
..........................
1-
7
Specifying Network Settings .......................................................... 1-7
Registering Destinations and Specifying Their Settings ................ 1-7
Registering Mailboxes (for Save in Mailbox Operations) ...............
1-8
1.4 Settings for Scanning .......................................................................
1-9
Specifying the Scan Settings ......................................................... 1-9
Specifying the Destination ............................................................. 1-9
1.5
Connecting
to
the
Network
...........................................................
1-10
Network Connection .................................................................... 1-1
O
Turning On the System ................................................................ 1-1
O
1.6
Flow
Chart
of
Setup
and
Scanning
Operations
........................... 1-11
1.7 Frequently
Used
Screens
............................................................... 1-12
To display the Scan screen .......................................................... 1-12
To display the User Setting screen .............................................. 1-14
To displaythe Administrator Setting screen ................................ 1-15
Fiery X3eTY 35C-KM x-5

Introduction
2.1
Control Panel .....................................................................................
2-2
2.2 Displaying the Scan Screen ..............................................................
2-5
2.3 Sending Data in an E-Mail
Message
(Scan
to
E-Mail) ....................
2-6
Scan to E-Mail ................................................................................2-6
Using Programs ..............................................................................2-6
Selecting Group Addresses ............................................................2-9
Selecting Destinations From the Address Book ...........................2-12
Performing
an
LDAP Search .........................................................2-15
Entering the Addresses Directly ...................................................2-16
2.4 Sending Data
to
a Server (Scan
to
FTP) ........................................2-19
Scan to
FTP
..................................................................................2-19
Using Programs ............................................................................2-19
Selecting Group Addresses ..........................................................2-21
Selecting Destinations From the Address Book ...........................2-24
Entering the Addresses Directly ...................................................2-27
2.5
Sending
Data
to
a PC on
the
Network
(Scan
to
SMB) .................2-31
Scan to SMB .................................................................................2-31
Using Programs ............................................................................2-31
Selecting Group Addresses ..........................................................2-33
Selecting Destinations From the Address Book ...........................2-35
Entering the Addresses Directly ...................................................2-38
2.6 Saving Data
on
the
Hard
Disk
(Save in Mailbox) ..........................2-41
Save
in
Mailbox .............................................................................2-41
Types of Mailboxes .......................................................................2-41
Using Programs ............................................................................2-42
Selecting Group Addresses ..........................................................2-44
Selecting Destinations From the Address Book ...........................2-46
To save data
to
the specified mailbox ..........................................2-49
2.7 Specifying
the
Scan
Settings
..........................................................2-52
Available Settings .........................................................................2-52
File Type ........................................................................................2-53
To specify the File Type settings ..................................................2-55
Resolution .....................................................................................2-56
Simplex/Duplex .............................................................................2-57
To specify the Simplex/Duplex setting .........................................2-57
Color .............................................................................................2-58
To specify the Color setting ..........................................................2-59
Scan Size ......................................................................................2-60
To specify the Scan Size setting ...................................................2-60
Brightness .....................................................................................2-62
Background Removal ...................................................................2-63
Original Setting .............................................................................2-64
x-6 Fiery X3eTY 35C-KM

Introduction
To specify the Original Settings ................................................... 2-64
Book Scanning (Application) ........................................................ 2-66
To use the "Book Scan" function ................................................. 2-67
Frame Erase (Application) ............................................................ 2-68
Separate Scan .............................................................................. 2-70
2.8 Checking the Settings ....................................................................2-71
Checking the Settings .................................................................. 2-71
To check a job .............................................................................. 2-72
Deleting Unneeded Destinations ................................................. 2-76
Changing the File Name and Other Settings ............................... 2-78
To change the e-mail settings ...................................................... 2-79
2.9
Checking
the
Scan
Job
List
...........................................................
2-80
Displaying the
Job
List for Scan to E-mail, Scan
to
FTP
and
Scan to SMB Operations ............................................................. 2-80
Checking the Box
Job
List ........................................................... 2-81
Displayed Information .................................................................. 2-82
3.1
Registering
Abbreviated
Destinations
............................................
3-2
E-Mail Destinations ........................................................................ 3-2
FTP
Destinations ............................................................................ 3-5
SMB Destinations .......................................................................... 3-9
Mailbox Destinations .................................................................... 3-13
3.2 Registering
Group
Destinations
....................................................
3-16
To register a group destination .................................................... 3-16
3.3 Registering
Program
Destinations
................................................ 3-18
To register a program destination ................................................ 3-18
4.1
Specifying E-Mail
Settings
...............................................................
4-2
Subject ........................................................................................... 4-2
Text ................................................................................................ 4-4
4.2 Setting
the
Main Scan
Mode
Screen ..............................................
4-6
Default Tab ..................................................................................... 4-6
Program Default ............................................................................. 4-7
4.3 Setting
the
Save
Format
of
the
Data
to
Be
Scanned
....................
4-8
JPEG Compression Level .............................................................. 4-8
To specify the compression level ................................................... 4-8
Fiery X3eTY 35C-KM x-7

Introduction
4.4 Prefix/Suffix Settings ......................................................................4-1 0
Prefix/Suffix Parameters ...............................................................4-1 O
To specify the prefix/suffix settings ..............................................4-1 0
Prefix/Suffix Setting ......................................................................4-12
4.5
Authentication
Function
..................................................................4-15
UserAuthentication/Account Track and Scan Functions .............4-15
Authentication Method and Fiery Remote Scan Software ...........4-15
5.1
Available Settings ..............................................................................
5-2
5.2 Entering
the
Image
Controller
Setup
Screen ..................................
5-4
Displaying the Setup Screen ..........................................................5-4
5.3
Specifying
Settings
for
E-Mail
Transmissions
................................
5-5
Checking Copier E-Mail Transmission Settings .............................5-5
To check the e-mail transmission setting .......................................5-5
Checking TCP/IP Settings ..............................................................5-5
E-Mail Transmission Settings .........................................................5-5
URL Notification E-Mail Messages .................................................5-6
5.4
Specifying
Settings
for
Save in
Mailbox
Operations
......................
5-
7
Checking TCP/IP Settings ..............................................................5-7
Allowing Mailbox Passwords ..........................................................5-7
Creating a Mailbox ..........................................................................5-7
Downloading the Image Data
to
the Computer ..............................5-9
5.5
Specifying
Settings
for
FTP File
Transmissions
...........................
5-10
Checking TCP/IP Settings ............................................................5-10
Enabling the
FTP
Transfer Function .............................................
5-1
O
Proxy Settings ...............................................................................5-10
5.6
Specifying
Settings
for
SMB
Server
Transmissions
.....................5-12
Checking Copier SMB Settings ....................................................5-12
To check the SMB setting ............................................................5-12
Checking TCP/IP Settings ............................................................5-12
5.7
Setting
the
Error
Notification
Destination
.....................................5-13
To set the error notification destination ........................................5-13
5.8
Setting
the
Sender
(From)
Address
...............................................
5-14
To set the sender (from) address ..................................................5-14
5.9
Hold
Period
of
the
Image
Data .......................................................
5-15
To specify the hold period
of
the image data ...............................5-15
x-8 Fiery X3eTY 35C-KM

Introduction
6.1
Copier
Network
Settings ..................................................................
6-2
6.2 TCP/IP Settings .................................................................................
6-5
Items To Be Specified .................................................................... 6-5
To specify TCP/IP settings ............................................................. 6-6
6.3 NetWare Settings ..............................................................................
6-8
NetWare Parameters ...................................................................... 6-8
To specify NetWare settings .......................................................... 6-8
6.4 FTP Settings ......................................................................................
6-9
FTP
Parameters ............................................................................. 6-9
To specify
FTP
settings .................................................................. 6-9
6.5 SMB Settings ...................................................................................
6-10
SMB Parameters ..........................................................................
6-1
O
To specify SMB settings .............................................................. 6-11
6.6 Enabling LDAP
Settings
................................................................. 6-12
Enabling LDAP Parameters .......................................................... 6-12
To specify Enabling LDAP settings .............................................. 6-12
Initial Setting for Search Details ................................................... 6-14
6.7· Setting Up LDAP
Settings
.............................................................. 6-16
LDAP Server Registration Parameters ......................................... 6-16
To specify Setting Up LDAP settings ........................................... 6-18
General Settings ........................................................................... 6-20
To specify the authentication method ......................................... 6-20
6.8 E-Mail TX (SMTP) Settings .............................................................6-21
E-Mail TX (SMTP) Parameters ...................................................... 6-21
To specify E-Mail
TX
(SMTP) settings .......................................... 6-22
SMTP Server Address .................................................................. 6-25
SMTP Authentication ................................................................... 6-26
6.9 E-Mail RX (POP)
Settings
...............................................................6-28
E-Mail
RX
(POP)
Parameters ........................................................ 6-28
To specify E-Mail
RX
(POP)
settings ............................................ 6-29
POP
Server Address .................................................................... 6-30
6.10 MAC Address ..................................................................................6-31
Device Parameters ....................................................................... 6-31
To check the MAC address ......................................................... 6-31
6.11
Time
Adjustment
Settings ............................................................. 6-32
Time Adjustment Parameters ....................................................... 6-32
To specify time adjustment settings ............................................ 6-32
NTP
Server Address ..................................................................... 6-33
Fiery X3eTY 35C-KM
x-9

Introduction
6.12 Status Notification Settings ............................................................6-35
Status Notification Parameters .....................................................6-35
To specify status notification settings ..........................................6-35
Notification Item Setting ...............................................................6-36
6.13 PlNG Confirmation ..........................................................................6-37
PING Confirmation Parameters ....................................................6-37
To specify PING confirmation settings .........................................6-37
PING
TX
Address ..........................................................................6-39
6.14 IS OpenAPI Settings ........................................................................6-40
Access Setting ..............................................................................6-40
Port No..........................................................................................6-41
SSL ...............................................................................................6-41
Authentication ...............................................................................6-43
7
.1
System Requirements .......................................................................
7-2
Computer ........................................................................................7-2
7.2 Accessing Web Connection .............................................................7-3
To access Web Connection ............................................................7-3
Page Structure ................................................................................7-4
Administrator Modes ......................................................................7-5
Logging
On
to
Administrator Mode ................................................7-6
Logging
On
to
the Image Controller's Administrator Mode ............7-6
Logging
On
to
the Copier's Administrator Mode ............................7-7
Changing the Administrator Password ...........................................7-8
Changing the Image Controller's Administrator Password ............7-8
Changing the Copier's Administrator Password ............................7-8
7
.3
User Mode .........................................................................................7-9
System tab ......................................................................................7-9
Job
tab ..........................................................................................7
-1
O
User Box tab .................................................................................7-11
Print tab ........................................................................................7-12
Scan Tab .......................................................................................7-13
"Address Book" Menu ..................................................................7-13
To register new destinations
in
the address book ........................7-15
"Group" Menu ...............................................................................7-16
To register new "Group" ...............................................................7-16
"Program" Menu ...........................................................................7-18
To register new destinations .........................................................7-24
"Temporary One-Touch" Menu ....................................................7-26
"Subject" Menu .............................................................................7-28
"Text" Menu ..................................................................................7-29
x-10 Fiery
X3e
TY 35C-KM

Introduction
7.4 Image
Controller
Administrator
Mode
.......................................... 7-31
System Tab .................................................................................. 7-31
"Device Information" Menu .......................................................... 7-31
"Online Assistance" Menu ........................................................... 7-32
User Box Tab ............................................................................... 7-33
"Mailbox" Menu ........................................................................... 7-33
7.5 Copier Administrator Mode ........................................................... 7-35
System
tab
................................................................................... 7-35
User Box
tab
................................................................................ 7-36
Scan Tab ...................................................................................... 7-37
"Prefix/Suffix" Menu ..................................................................... 7-37
"Import/Export" Menu .................................................................. 7-38
Importing ...................................................................................... 7-38
Exporting ...................................................................................... 7-38
"Other" Menu ............................................................................... 7-39
Network Tab ................................................................................. 7-39
"TCP/IP" Menu ............................................................................. 7-40
"NetWare" Menu .......................................................................... 7-41
"FTP" -"Server" Menu ............................................................... 7-42
"SMB"
-"Scan" Menu ............................................................... 7-43
"LDAP" Menu ............................................................................... 7-44
"E-Mail" -"E-Mail Receive" Menu ............................................. 7-46
"E-Mail" -"E-Mail Transmission" Menu ..................................... 7-47
"SSL/TLS" Menu .......................................................................... 7-49
SSL/TLS Setting ........................................................................... 7-51
To create a certificate .................................................................. 7-52
SSL/TLS Setting -Install a Certificate ....................................... 7-54
"Authentication" -"Auto Logout" Menu .................................... 7-55
"IS OpenAPI" Menu ..................................................................... 7-56
8.1
Entering Text .....................................................................................
8-2
To
type
text
.................................................................................... 8-5
List
of
Available Characters ........................................................... 8-5
Number
of
Characters That Can Be Entered ................................. 8-6
8.2 Glossary .............................................................................................
8-
7
8.3 Index ·················································································"'··············8-11
Fiery X3eTY 35C-KM x-11

Introduction
About This Manual
x-12
This User's Guide provides descriptions of the network scanning functions
available with Fiery X3eTY 35C-KM (the optional image controller for digital
color copier).
In
addition, supplementary descriptions are provided
in
chap-
ter 6 forthe network functions that can be used from the copier when Fiery
X3eTY 35C-KM
is
installed.
This section introduces the structure
of
the manual and the notations used
for product names, etc.
This manual
is
intended for users who understand the basic operations
of
computers and this machine. For operating procedures
of
the Windows
or
Macintosh operating system and software applications, refer
to
the corre-
sponding manuals.
Structure of the Manual
This manual consists ofthe following chapters.
Chapter 1 Before Using the Scan Functions
Chapter 2 Scanning Documents
Chapter 3 Registering Destinations (Recipients)
for
Network Scanning
Chapter 4 Other Network Scanning Settings
Chapter 5 Specifying Network Scanning Settings
Chapter 6 Copier Network Functions
Chapter 7 Using Web Connection
Chapter 8 Appendix
Lists the characters that can be entered from the control panel.
Notation
Product
Name Notation in
the
Manual
Digital color copier This machine
Fiery X3eTY 35C-KM Image Controller Image Controller
Microsoft Windows 98 Windows 98
Microsoft Windows Me Windows Me
Microsoft Windows NT 4.0 Windows NT 4.0
Microsoft Windows 2000 Windows 2000
Microsoft Windows
XP
Windows
XP
Fiery X3eTY 35C-KM

Introduction
Product Name
Microsoft Windows Server 2003
When the operating systems above are written
together
Fiery X3eTY 35C-KM
Notation
in the Manual
Windows Server 2003
Windows 95/98/Me
Windows
NT
4.0/2000/XP/Server 2003
Windows 95/98/Me/NT 4.0/2000/XP/Server
2003
x-13

Introduction
Explanation
of
Manual Conventions
~
...
--------,
Note
Text highlighted
in
this manner
contains references
and
supplemental
information concerning operating
procedures and other descriptions.
We
recommend that this information
be read carefully.
[ l
----------+--.
Names highlighted
as
shown above
indicate keys on the control panel
and buttons
in
the touch panel.
Touch panel screens are shown to
check the actual display.
Titles indicate the contents of the section.
Basic Copy Operations
3.6 Selecting a Paper Setting
The papersize can
be
selected automatically according to the document
size or it can be specified manually. Specifythe paper size according
to
the
corresponding procedure, depending on
the
desired copy settings.
~--·
Note
The
defaultsetting
is
"Auto
Paper
Select".
Automatically
Selecting
the
Paper
Size
("Auto
Paper
Select'' Setting)
The size
of
the
loaded
document
is
detected, and copiesare producedusing
a er ofthe same size.
In
the Basic screen, touch [Paper].
The Paperscreen appears.
~
-------------
~
...
• • •
Reminder
Reminder
Text highlighted
in
this manner
indicatesoperation precautions.
Carefully read and observe this
type
of
information.
Be
careful
that
your
fingers
are
not
pinched
when the
front
door
is
closed
Detail
For
details
on
the
positions
of
paper
misfeeds, referto "Paper
Misfeed
In-
dications"
on
page
5-1.
& CAUTION
Metallic
parts
on
the
inside
of
the upper
cover
are
very
hot
q--------+--'
Detail
A,.
,Touching
any part otherthan the paper may result
in
~
bums.
Text highlighted
in
this manner
provides more detailed information
concerning operating procedures or
references to sections containing
additional information. If necessary,
refer to the indicated sections.
& WARNING , CAUTION
3-31
Text highlighted
in
this manner indicates precautions to ensure safe use of this machine.
"Warning" indicates instructions that, when not observed, may result
in
fatal
or
critical injuries.
"Caution" indicates instructions that, when not observed, may result in serious injuries
or
property damage.
(The page shown above is an example only.)
x-14 Fiery X3eTY
35C-KM

Before
Using
the
Scan
Functions
CJ)
c
0
:.;::::;
(.)
c
::J
LL
c
ro
(.)
(/)
(1.)
..c
.........
0)
c
·u5
:::,
(1.)
I...
0
-
(1.)
co

1
(/)
1.1
c
0
:..::;
(.)
c
~
LL
c
cu
(.)
Cl)
(1)
.c
+-'
0)
c
(/)
::)
(1)
~
0
-
(1)
co
1-2
Before Using the Scan Functions
Before Using the Scan Functions
Environment Required for Using the Scan Functions
The following conditions are required
to
use the network and scanning
func-
tions.
• The machine is connected
to
the network.
The functions can be used over a TCP/IP network.
-For details on connecting the network cable, refer
to
"Connecting
to
the
Network" on page 1-10.
In
order
to
usethis machineon a network, settings such as the
IP
address
of
the image controller must be specified. For details, refer
to
"Settings
for Using Network/Scanning Functions" on page 1-7.
Fiery X3eTY
35C-KM

Before Using the Scan Functions
1.2 Available Scanning Functions
"Scanning" refers
to
the operation
of
reading the image
of
a
document
fed
through
the
automaticdocumentfeeder
or
placed on the original glass
of
the
copier. The scanning functions can be used to send scanned
data
in an e-
mail message over a network
or
upload
the
data
to
a file server.
Sending the Scanned Data
in
an E-Mail Message
The scanned datacan be sent
to
a specified e-mail address. The destination
is specified from thetouch panel
of
this copier, and
the
scanned
data
is sent
as
an
e-mail attachment.
Fordetails, refer
to
"Sending Data
in
an E-Mail Message (Scan
to
E-Mail)" on
page 2-6.
Original
G
~
Copier
E-mail and scan data E-mail reception
SMTP server POP server
Internet
Fiery X3eTY 35C-KM 1-3
Cl)
c
.Q
_.
<.)
c
:::J
LL
c
co
<.)
Cl)
CD
.c
_.
0)
c
·u5
:::,
CD
l,,_
0
-
CD
cc

Cl)
c
0
t5
c
::J
LI..
c
C'CS
(.)
(/)
(])
.c
+-'
O')
c
·u5
::)
(])
~
0
-
(])
co
1-4
Before Using the Scan Functions
Sending the Scanned Data as Files (FTP}
The scanned data is uploaded
to
a specified
FTP
server. The
FTP
server
ad-
dress, login password, and other information are entered from the touch
panel
of
this copier.
The data files uploaded
to
the
FTP
server can be downloaded from a
com-
puter on the network.
For details, refer
to
"Sending Data
to
a Server (Scan
to
FTP)" on page 2-19.
Original
<
~
D
Copier
Scan data Download
FTP
server
Internet
Fiery X3eTY 35C-KM

Before Using the Scan Functions
Sending the Scanned Data to a Computer
on
the Network (SMB)
The scanned data can be sent
to
a shared folder on a specified computer.
The name
of
the destination computer, login password, and other informa-
tion are entered from the touch panel
of
this copier.
For details, refer
to
"Sending Data
to
a
PC
on the Network (Scan
to
SMB)"
on page 2-31.
Original
<
iP
Copier D
Scan data
Save
to
a shared folder
Fiery X3eTY 35C-KM 1-5
Cl)
c
0
:;::::;
(.)
c
::::::i
LL
c
cu
(.)
(./)
CD
.c
......
0)
c
·u5
::::,
CD
:......
0
-
CD
co
Table of contents
Other Fiery Controllers manuals
Popular Controllers manuals by other brands

Agilent Technologies
Agilent Technologies TwisTorr 74 FS user manual

Hydrofarm
Hydrofarm autopilot APC8400 user manual

aquilar
aquilar aquitron AT-MGS-408 Installation & operation instructions
Savant
Savant SmartControl 3 Quick reference guide

ABB
ABB RSD Series operating instructions
Cross Technologies
Cross Technologies 2082-141-47 instruction manual