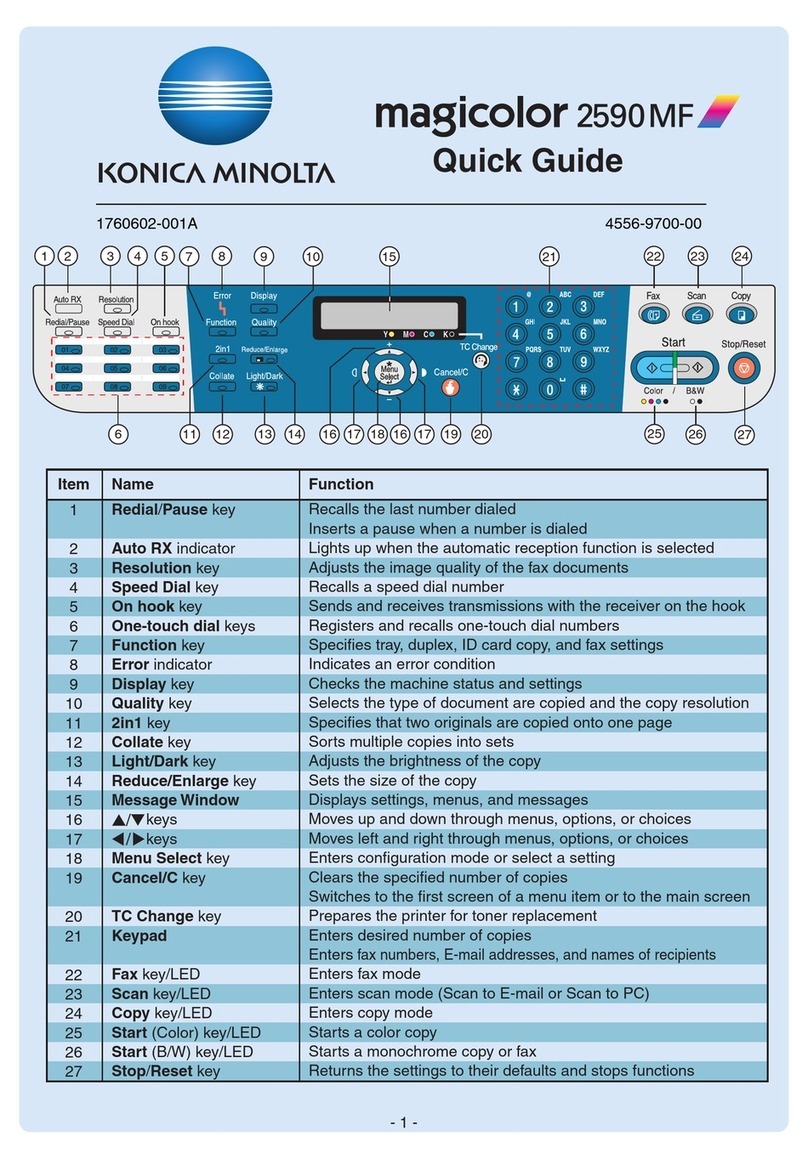
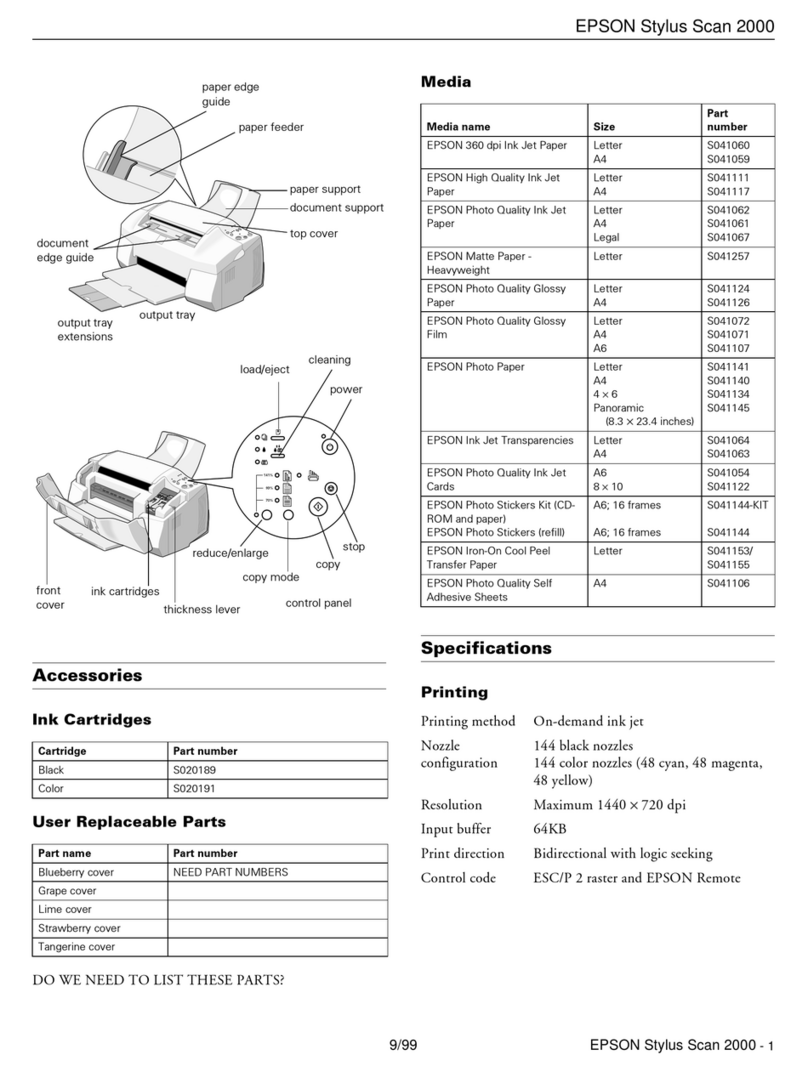
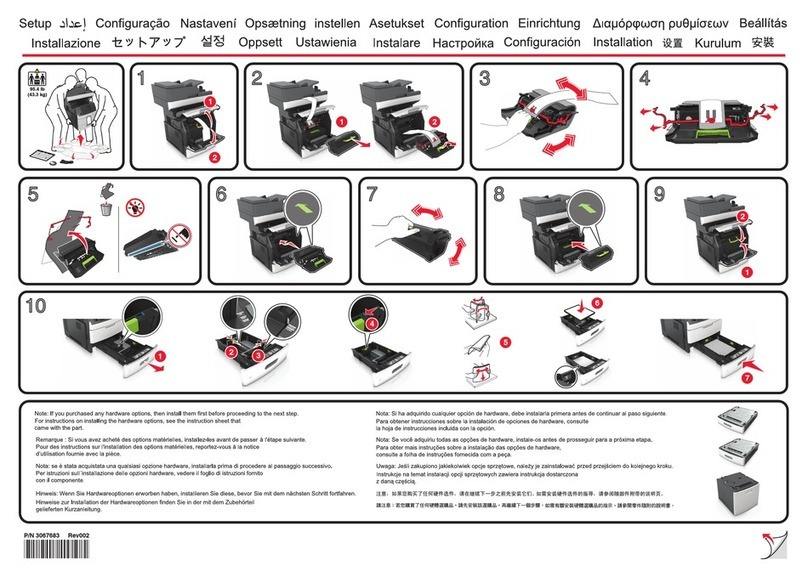
C253/C203 x-1
Contents
Contents
1 Security
1.1 Introduction........................................................................................................................................... 1-2
Compliance with the ISO15408 Standard ................................................................................................1-2
Operating Precautions..............................................................................................................................1-2
INSTALLATION CHECKLIST ....................................................................................................................1-3
1.2 Security Functions................................................................................................................................ 1-4
1.2.1 Check Count Clear Conditions.................................................................................................................1-4
1.3 Data to be Protected ............................................................................................................................ 1-5
1.4 Precautions for Operation Control...................................................................................................... 1-6
Roles and Requirements of the Administrator..........................................................................................1-6
Password Usage Requirements ...............................................................................................................1-6
Operation and control of the machine......................................................................................................1-6
Network Connection Requirements for the Machine ...............................................................................1-7
Machine Maintenance Control..................................................................................................................1-7
Implementing digital signature properly ...................................................................................................1-7
Operating conditions for the IC card and IC card reader .........................................................................1-7
IC card owner requirements .....................................................................................................................1-7
1.5 Miscellaneous ....................................................................................................................................... 1-8
Password Rules........................................................................................................................................1-8
Precautions for Use of Various Types of Applications .............................................................................1-8
Types of Data Cleared by Overwrite All Data Function ............................................................................1-8
Items cleared by HDD Format ..................................................................................................................1-8
2 Administrator Operations
2.1 Accessing the Administrator Settings ................................................................................................ 2-2
2.1.1 Accessing the Administrator Settings ......................................................................................................2-2
<Setting can be made only from the control panel> ................................................................................2-3
2.1.2 Accessing the User Mode ........................................................................................................................2-5
<Setting can be made only from the control panel> ................................................................................2-5
2.2 Preventing Unauthorized Access........................................................................................................ 2-7
2.2.1 Setting Prohibited Functions When Authentication Error.........................................................................2-7
<Setting can be made only from the control panel> ................................................................................2-8
2.3 Setting the External Server................................................................................................................ 2-10
2.3.1 Setting the External Server.....................................................................................................................2-10
<Setting can be made only from the control panel> ..............................................................................2-10
2.4 System Auto Reset Function ............................................................................................................. 2-13
2.4.1 Setting the System Auto Reset function.................................................................................................2-13
<Setting can be made only from the control panel> ..............................................................................2-13
2.5 Changing the Administrator Password ............................................................................................ 2-15
2.5.1 Changing the Administrator Password...................................................................................................2-15
<Setting can be made only from the control panel> ..............................................................................2-15
2.6 Protecting Data in the HDD ............................................................................................................... 2-18
2.6.1 Setting the HDD Lock Password............................................................................................................2-18
<Setting can be made only from the control panel> ..............................................................................2-19
2.6.2 Changing the HDD Lock Password........................................................................................................2-21
<Setting can be made only from the control panel> ..............................................................................2-21
2.6.3 Setting the Encryption Key (encryption word) ........................................................................................2-24
<Setting can be made only from the control panel> ..............................................................................2-24
2.6.4 Changing the Encryption Key.................................................................................................................2-30
<Setting can be made only from the control panel> ..............................................................................2-30
2.7 Overwrite All Data Function............................................................................................................... 2-33
2.7.1 Setting the Overwrite All Data function ..................................................................................................2-33
<Setting can be made only from the control panel> ..............................................................................2-34