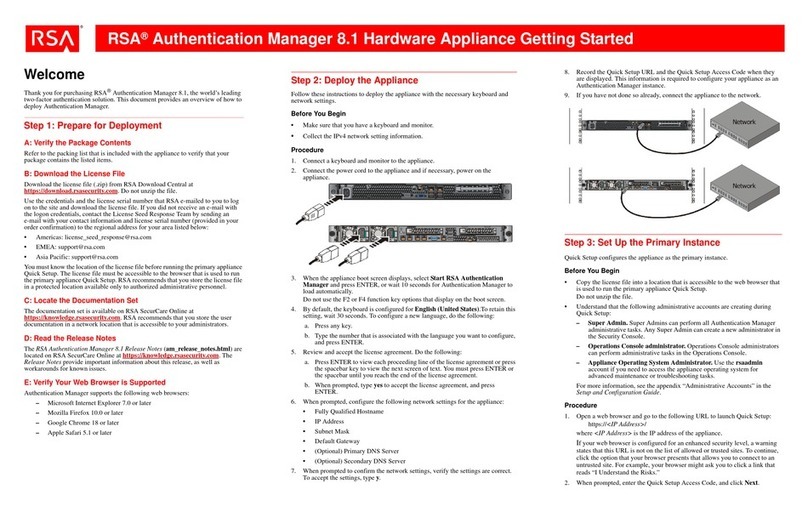
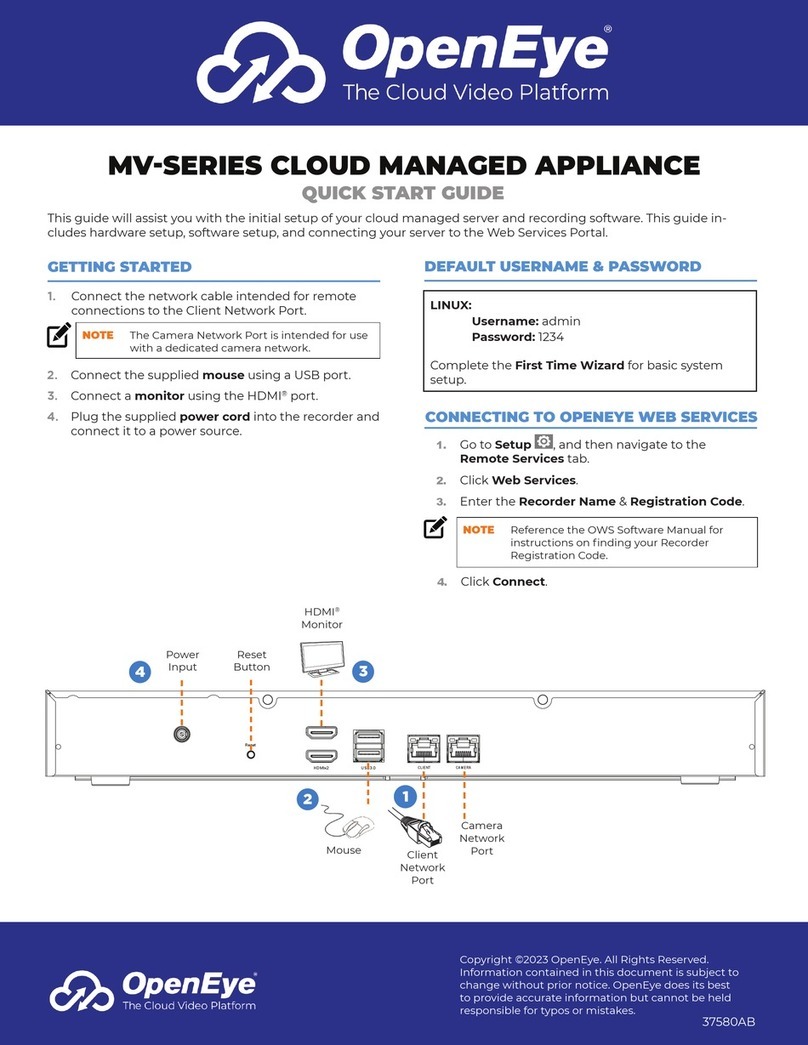
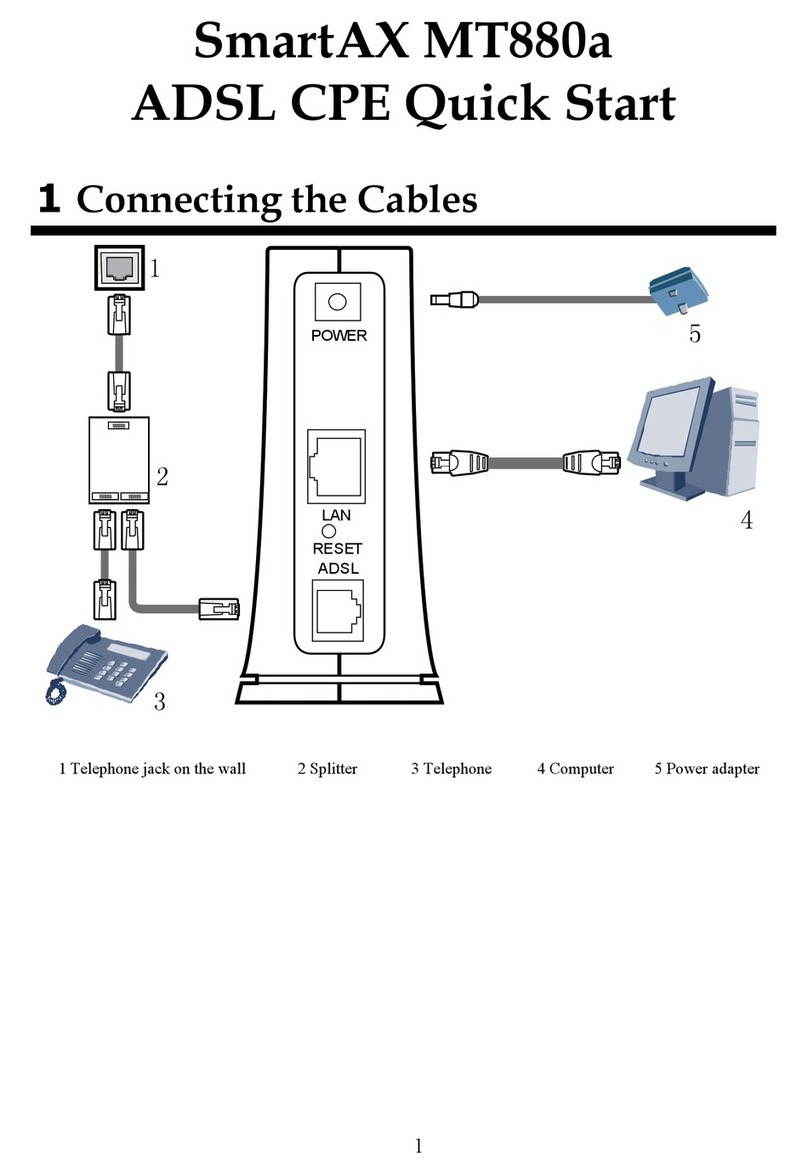
RSA®Authentication Manager 8.2 Hardware Appliance Getting Started
Procedure
1. Open a web browser and go to the following URL to launch Quick Setup:
https://<IP Address>/
where <IP Address> is the IP address of the appliance.
If your web browser is configured for an enhanced security level, a warning
states that this URL is not on the list of allowed or trusted sites. To continue,
click the option that your browser presents that allows you to connect to an
untrusted site. For example, your browser might ask you to click a link that
reads “I Understand the Risks.”
2. When prompted, enter the Quick Setup Access Code, and click Next.
3. Click Start Primary Quick Setup. Follow the instructions on each screen to
complete Quick Setup.
Record all of the passwords to the administrative accounts that you create
during Quick Setup.
The operating system password is required to access the appliance for
advanced maintenance or troubleshooting tasks. For security reasons, RSA
does not provide a utility for recovering the operating system password.
4. After the instance is configured, you can click the Security Console or
Operations Console URL links to open those consoles. The Security Console
or Operations Console URL links require a fully qualified domain name
(FQDN).
Note: The fully qualified domain name must resolve to your appliance. If you
are having trouble connecting to the Consoles, verify the DNS configuration.
The first time you access the Security Console or the Operations Console, a
warning appears because the default self-signed certificate created after Quick
Setup is not trusted by your browser.
5. Accept the certificate to access the console and prevent the warning from
appearing again. For more information, see the chapter “Deploying a Primary
Appliance” in the Setup and Configuration Guide.
Logging On to the Consoles
After you have completed Quick Setup, you can use the following links to access a
console.
To view a complete list of URLs that are available for the consoles, see the Setup
and Configuration Guide.
Console URL
Security Console https://<fully qualified domain name>/sc
Operations Console https://<fully qualified domain name>/oc
Self-Service Console If there is no web tier, enter:
https://<fully qualified domain name>/ssc
After installing a web tier, enter:
https://<fully qualified virtual host name>/ssc
If you change the default load balancer port, enter:
https://<fully qualified virtual host name>:<virtual host
port>/ssc
Next Steps
After setting up the appliance, consider which of the following tasks you want to
perform for the Authentication Manager deployment. You must perform all post-
setup tasks on the primary instance.
Support and Service
RSA Link offers a knowledgebase that contains answers to common questions and solutions to known
problems. It also offers information on new releases, important technical news, and software
downloads.
The RSA Ready Partner Program website provides information about third-party hardware and
software products that have been certified to work with RSA products. The website includes
Implementation Guides with step-by-step instructions and other information on how RSA products
work with third-party products.
RSA, the RSA Logo and EMC are either registered trademarks or trademarks of EMC Corporation in
the United States and/or other countries. All other trademarks used herein are the property of their
respective owners. For a list of RSA trademarks, go to www.emc.com/legal/emc-corporation-
trademarks.htm#rsa.
Copyright © 2016 EMC Corporation. All Rights Reserved.
June 2016
P/N 300-000-233_01
Task More Information
Add Authentication Manager users To add users to the internal database, see
Chapter 6, “Administering Users” in the
Administrator’s Guide.
To link to an external identity source, see
Chapter 5, “Integrating LDAP Directories”
in the Administrator’s Guide.
Assign authentication policies See Chapter 4, “Configuring Authentication
Policies” in the Administrator’s Guide.
Import tokens and assign users See Chapter 8, “Deploying and
Administering RSA SecurID Tokens” in the
Administrator’s Guide.
Set up risk-based authentication
(RBA)
See the Security Console Help topic
“Risk-Based Authentication.”
Set up on-demand authentication
(ODA)
See the Security Console Help topic
“On-Demand Authentication.”
Configure end-user Self-Service for
maintenance and troubleshooting.
See the Security Console Help topic
“RSA Self-Service Overview.”
RSA Link –
RSA SecurID Space
https://community.rsa.com/community/products/securid
Customer Support https://community.rsa.com/community/rsa-customer-support
RSA Ready Partner
Program
www.rsaready.com
If your web browser is configured for an enhanced security level, add the URL for
each console to the list of allowed or trusted sites, including any additional URLs that
you intend to use. See your browser documentation for instructions.
To access the Security Console, enter the Super Admin User ID and password that
you specified during Quick Setup. To access the Operations Console, enter the
Operations Console user ID and password that were entered during Quick Setup.
Step 4: Set Up a Replica Instance
After you configure the primary instance, you can deploy another appliance and set
up a replica instance.
Keep the appliance on a trusted network until Quick Setup is complete. The client
computer and browser used to run Quick Setup should also be on a trusted network.
Before You Begin
A primary instance must be deployed on the network.
Procedure
1. On the primary instance, log on to the Operations Console, and click
Deployment Configuration > Instances > Generate Replica Package. For
instructions, see the Operations Console Help topic “Generate a Replica
Package.”
2. Deploy the appliance. For instructions, see Step 2: Deploy the Appliance.
3. Open a browser and go to the following URL to launch Quick Setup:
https://<IP Address>/
where <IP Address> is the IP address of the replica appliance.
If your web browser is configured for an enhanced security level, a warning
states that this URL is not on the list of allowed or trusted sites. To continue, click
the option that allows your browser to connect to an untrusted site.
4. When prompted, enter the Quick Setup Access Code, and click Next.
5. Click Start Replica Quick Setup. Follow the instructions on each screen to
complete Quick Setup.
Record the operating system password that is created during Quick Setup.
The operating system password is required to access the appliance for advanced
maintenance and troubleshooting tasks. For security reasons, RSA does not
provide a utility for recovering the operating system password.
6. After the instance is configured, do one of the following:
•Click Begin Attach to attach the replica instance to the primary instance.
•Click Defer Attach to attach the replica instance at another time. When
prompted, confirm your choice. The replica instance powers off. You can
attach the replica instance the next time you power on the replica instance.
For instructions, see the Operations Console Help topic “Attach the Replica
Instance to the Primary Instance.”
Web Tier Installation
Web tiers are not required, but your deployment might need them to satisfy your
network configuration and requirements. Authentication Manager includes services,
such as risk-based authentication, dynamic seed provisioning, and the Self-Service
Console, that may be required by users outside of your corporate network. If your
network includes a DMZ, you can use a web tier to deploy these services inside the
DMZ. For more information, see the chapter “Planning Your Deployment” in the
Planning Guide.