MorphoAccess® SIGMA Series –Administration Guide
MORPHO DOCUMENT –REPRODUCTION AND DISCLOSURE FORBIDDEN
Terminal Firmware Upgrade ...........................................................................................67
How to get last version of firmware.................................................................................... 67
How to upgrade the firmware............................................................................................. 67
Firmware upgrade using a USB Mass Storage Key ............................................................. 67
Firmware upgrade tool for expert users.............................................................................. 67
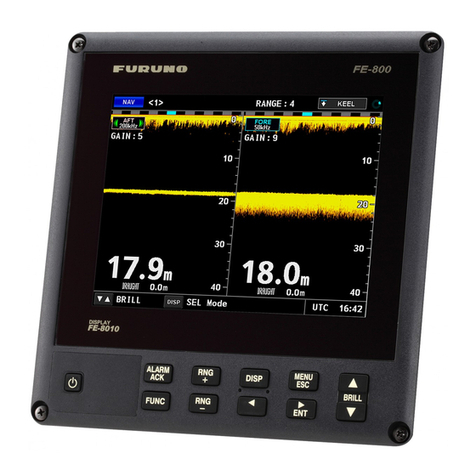
MorphoAccess® SIGMA Series Modes..............................................................................69
MorphoAccess® 500 or J Series legacy mode ...................................................................... 69
L-1 Bioscrypt 4G Series legacy mode ................................................................................... 69
MorphoAccess® SIGMA Series native mode........................................................................ 70
SECTION 5 : FIRST BOOT ASSISTANT ...................................................................................71
Assistant Initialization ....................................................................................................72
Date & Time Configuration .............................................................................................73
Trigger Event ..................................................................................................................77
Language Configuration .................................................................................................78
Show/Hide Language Icon ..............................................................................................80
Ethernet Interface Settings .............................................................................................81
Wi-Fi™ Configuration......................................................................................................83
Protocol Configuration....................................................................................................89
Password Configuration..................................................................................................91
First Boot Assistance At Next Boot Configuration ............................................................93
Recover Corrupted Components ......................................................................................94
SECTION 6 : ADMINISTRATION MENU.................................................................................95
Access to Administration Menu.......................................................................................96
User Menu......................................................................................................................98
User Enrollment in Database............................................................................................... 99
User Enrolment in Card...................................................................................................... 114
User Enrolment in Card & Database ................................................................................. 116
Update User Information................................................................................................... 118
Authenticate User.............................................................................................................. 121
Delete User ........................................................................................................................ 123
Card Manager.................................................................................................................... 126
Multimedia menu .........................................................................................................157
Audio Settings.................................................................................................................... 158
Video Settings.................................................................................................................... 161
Images Settings ................................................................................................................. 164
System Menu................................................................................................................167
Terminal Configurations .................................................................................................... 168