Tosibox Central Lock User manual

Tosibox Central Lock Instruction Manual
EASY QUICK SECURE v1.4 English

The benets of Tosibox
Take in use only in 5 minutes
High sophisticated information
security
Flexible and scaling architecture
Operates trustworthy in all internet
interfaces
1. Introduction 2. Setup
The purpose of this document is to illustrate the
deployment of Tosibox Central Lock and its most
important properties. The creation and administration
of Keys for Central Lock and the user interface are also
presented here.
Please note that this document concentrates only on the
properties of Central Lock. The basics of Key and Lock
products are explained in the Key and Lock user manual.
1.1 Central Lock in brief
The Central Lock operates on the same basic properties as
the Lock, but has better throughput and encryption capacity.
This allows the building of large-scale systems that provide
simultaneous access to as many as 4000 Locks and Keys and
the devices behind them.
The Central Lock also has three additional features not found
in the Lock, but are usually needed in more complex network
systems. These are:
Concurrent usage of sites with overlapping IP addresses
»
Collecting audit log data»
Monitoring and alert services to detect and notify the user»
about connection problems
Basic requirements
The deployment of Central Lock has a few basic requirements
to operate. It needs:
A wired network1.
One non-rewalled public IP-address2.
An Internet connection with speed of at least 10/10 Mbit/s.3.
Physical installation
After the basic requirements of deployment are met, you can
start the physical installation of the Central Lock. Please check
that the following items are included in the sales package:
Ethernet cable – RJ45, 1 m1.
Power cord2.
Extension power cord3.
The steps of physical installation:
Proper mechanical mounting of device1.
Plugging in the power cord2.
Connecting the network cable to the WAN port of the3.
Central Lock
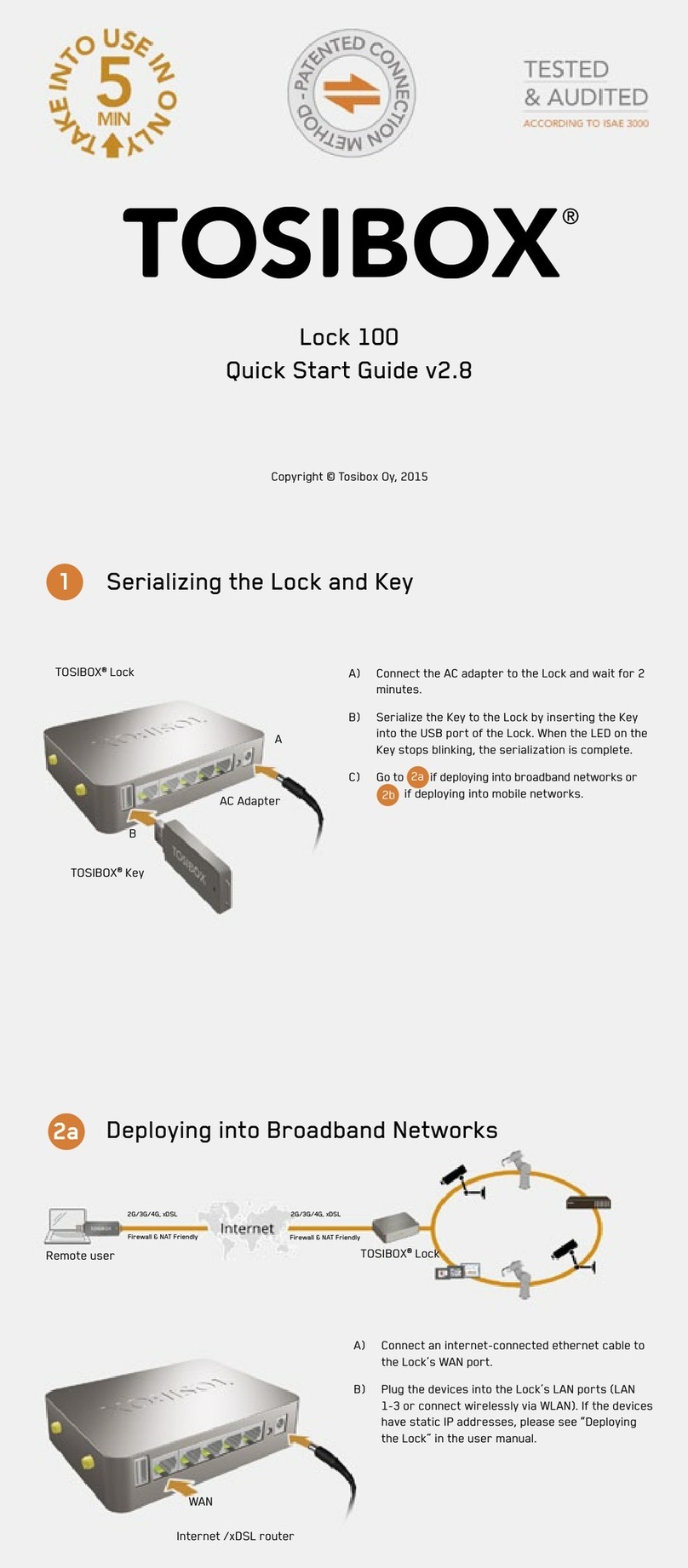
Serialization
Powering on the Central Lock starts the deployment. After 2
minutes, the Key can be inserted to the Central Lock’s USB port.
Once the LED light in the Key stops blinking, the serialization is
completed and the Key can be removed from the Central Lock.
Conguration
Conguring the Central Lock is done from the Web user
interface (see chapter Web User Interface). The Internet
connections for the Central Lock are congured in the WAN
settings of the Network tab. The protocol can be set to a
xed IP-address or a DHCP-client, in which case the address is
fetched from a DHCP server. By assigning the protocol to the
static address, the IP-address and subnet mask are written to
the elds below. When a static address is used, it is important
to set the address of the domain name server.
Deployment
After the serialization and conguration are done, the
deployment of Central Lock is completed and Locks, Keys and
network devices can be added to the system.

3. System Description
3.4 Connecting Central Lock to LAN
The Central Lock can be connected to an existing LAN network
in two ways. It can be used as a router or it can be connected
alongside an existing router. ** If the Central Lock is used as a
router, a DHCP server must be assigned to the specic LAN. In
this situation the remote sites can be accessed from the LAN
network of the Central Client. In the other situation, when the
Central Lock is not acting as a router, the DHCP server is usually
disabled. In this case, accessing remote sites requires opening
a Key connection to the Central Lock or static routes must be
congured to the user’s computer.
3.5 Administration of Keys
It is possible to create a backup from a Key serialized to the
Central Lock (see Lock and Key manual). Serializing new Sub
keys also works in the same way as other Tosibox products. The
Backup and Sub Keys of the Central Lock can be administrated
from the Key user interface through the Manage Keys menu.
The Master Key has full privileges and it can be used to
serialized additional Keys to Locks for deployment. An empty
Key that is rst serialized with a Lock becomes the Master Key
for that Lock, and additional Master Keys can be created with
the Key backup function.
A sub Key has restricted rights and it cannot be used to serialize
additional Keys nor take new Locks into use. Key grouping can
be used to help manage a large number of Keys. The groups
are visible only in the Key user interface. A single Key can
belong to only one group and it is currently not possible to
create nested groups. **’/
3.1 Overview
The Central Lock makes it possible to build a system consisting
of large number of Tosibox Locks and Keys.
3.2 Additional features
Features specic to the Central Lock can be found here.
Translation of networks with identical addresses. Using1.
this feature it is possible to translate real IP addresses of
the Lock and its LAN devices to different, congurable IP
addresses. This feature enables using the same IP address
range for several Locks so that the Locks and their devices
can be used simultaneously with the Central Lock or a Key.
Audit log data collection and connection monitoring. The2.
Central Lock collects log data about the events of serialized
Locks. This feature logs the events of the Central Lock
itself and also the events of any serialized Locks and sub
Locks. Log collection and monitoring can be enabled from
the Settings -> Industry settings view of both the Central
Lock and the Locks that are expected to report events.
Only Locks from which log data is desired should have the
logging enabled.
Connection monitoring and alerts. The Central Lock can be3.
set to send email alerts for connections being established
and closed. The alerts can be set for any or all serialized
Locks. Activating alerts does not require any additional
services and can be done from the Settings -> Alerts view.
In other respects the functionality and usage of the Central
Lock is identical with other Lock devices in the Tosibox product
family. Please see Lock documentation for more detail.
3.3 System
Central Lock allows using up to 4000 serialized Locks and
Keys simultaneously. First the Key is serialized with all Locks
to be connected. The serialization process is presented in the
Key and Lock User Manual. Serializing a Key to the Central
Lock is carried out in the same way, but during the process
the connection type is dened as L2 or L3. In the case of a L2
connection, a Lock to Sub Lock relationship is created, which
means that both Locks are in the same network. Selecting L3
creates a routed connection where the Lock and the Central
Lock have their own IP sub networks. If the L3 connection
is chosen, the Key connection type must also be L3. Every
serialized Key uses a bridged (L2) or routed (L3) connection.
The bridged Key connection allows access to a specic LAN
network only. The routed L3 Key connection allows the selection
of multiple LAN networks that are bound and routed.
The desired connection type is selected in the Web user
interface by clicking the Edit Tosibox Devices button. The
default connection type for Keys serialized to a Central Lock is
L3. More Keys to the Central Lock can be serialized in the same
way as they are to a Lock.

4. Web User Interface
You can login to the Central Lock Web user interface
with an Internet browser using any LAN port address
that your computer belongs to or by using address
http://172.17.17.17 when directly plugged in to the service
port. There is a single access level, admin, and the default
password has been delivered along with the installation of
the Central Lock.
4.1 Status view
The Status view presents basic information about the
network conguration and all serialized Locks, Keys and
network devices.
Clicking Show/hide IP ranges either shows or hides
information about static and dynamic IP address ranges of
the LAN network. New devices are added either manually
by clicking the New network device button or automatically
by clicking the Scan for LAN devices button, which searches
for all the devices inside the LAN networks of the Central
Lock. The network device list can be cleared by clicking
Remove all devices.
The Edit Tosibox devices button (located near the bottom)
opens a view where you can rename items, prevents access
to key connected devices that are connected to a Lock’s
network, select an L2 or L3 connection type, dene a static
IP address for the Key and select LAN(s) accessible by the
Key. **
4.2 Settings view
The Settings tab makes it possible to change the password
of the admin account, restart the Central Lock, remove all
the serializations of the Central Lock, change the industrial
settings, set email alarms and update the software.
The industrial setting makes it possible to:
Change automatic discovery of the LAN devices
»
Allow remote support from Tosibox Ltd.»
Enable logging»
Prevent network device access to the Internet»
Prevent VPN access from Tosibox to the Mobile Client»
Prevent trafc between the Sub Locks serialized to the »
Central Lock
Limit LAN device trafc to certain MAC or IP addresses
»
Force computers using the Key to route all Internet»
trafc through the Central Lock

4.3 Network view
The Central Lock network settings can be edited in the
Network tab. The Interfaces view shows the settings for
LAN and Internet connections. A section inside the LAN
interface allows for DCHP server conguration. The
Static routes view displays all congured static routes.
In the Routes and MACs view there are all the routes
and MAC addresses known by the Central Lock. The
DHCP view lists active DCHP leases of the Central Lock
and IP addresses bound to the MAC address.
4.4 Logs view
The Logs tab contains the log events from the Central
Lock and its serialized locks. Log events can be
ltered by event type, text match and date. Logging
is congured via Central Lock’s Settings -> Industry
settings view and from the same view of the serialized
Locks.
5. Maintenance Instructions
5.1 Checklist for different situations
The Key’s connection window does not show the
connections:
The computer is not connected to the Internet.
»
The Key is not serialized to the Lock.
»
The Lock does not have an Internet connection or is not
»
connected to the Tosibox AC adapter
The Lock connection in the window remains yellow:
The Key has found a Lock, but a VPN connection has not
»
yet been established.
The Internet browser opened by the Key does not show the
device connections or the Lock connection in the window
remains red:
Make sure the controlled devices are connected to the
»
Lock.
In case the controlled device is connected to the Lock
»
wirelessly, use the Ethernet Service Port to
Log in to the Lock. Check that the wireless connection is
»
enabled and that the Lock and the Controlled device has
the same password and encryption settings.
Make sure the controlled device has a DHCP-service. If not,
»
add the device in the device list of the Lock and specify the
IP-address of the device.

6. Central Lock Use Case examples
Infoscreens
Car washing machine
Customer
(Mobile Client)
Customer
(Sub key)
Tosibox
Central Lock
Service person
(Master Key)
Tosibox
Lock #3
Tosibox
Lock #2
Tosibox
Lock #1
Internet
Infoscreen #1
Infoscreen #2
Infoscreen #3
Tosibox
Central Lock
Tosibox
Lock #3
Tosibox
Lock #2
Tosibox
Lock #1
Internet
Car washing
machine #1
Car washing
machine #1
Car washing
machine #1
Control room
Production line
Service people worldwide
Remote users
Tosibox Key
Lock serializing and
naming in production
Tosibox
Mobile Client
Remote user
(customer)

Central Locks on multiple sites
Offi ce HQ
Tosibox
Central Lock
Sweden
Service co #1
Tosibox
Lock #5
Tosibox
Lock #6
Tosibox
Lock #4
Tosibox
Lock #3
Tosibox
Lock #2
Tosibox
Lock #1
Internet
Service co #2
Service co #3
Remote users worldwide
Tosibox
Central Lock
Finland
Multiple customer croups
Internet Sub Key
Sub Key
Customer
Group 2
Customer
Group 1
Offi ce/HQ
Sub Key
Sub Key
Master backup
Key Sub Key
Company X
Layer 3

7. Technical Data 8. Glossary
Properties
One 1 Gbit/s WAN ports
»
Four 1 Gbit/s LAN ports
»
Over 700 Mbit/s encryption throughput
»
1000 concurrent remote connections per LAN network
»
Encryption and authentication PKI, 1024/2048 bit RSA
»
Data encryption TLS, Blowsh-128-CBC/AES-256-CBC
»
Physical properties:
1U (rack unit) for19” rack cabinet (rack rails included)
»
Length 430 mm / width 483 mm / height 43 mm
»
Environmental conditions:
Operational temperature +10... +30
»
Humidity 20% ... 80% non-condensing
»
Power consumption max 250 W
»
Input voltage 90 ... 264 V AC
»
Input frequency 47 --- 63 Hz
»
DHCP
Dynamic Host Conguration Protocol
Gbit/s
Gigabits per second
Hz
Hertz
IP
Internet Protocol
LAN
Local Area Network
LED
Light-Emitting Diode
Mbit/s
Megabits per second
mm
Millimetre
PKI
Public Key Infrastructure
TLS
Transport Layer Security
USB
Universal Serial Bus
V
Voltage
VPN
Virtual Private Network
W
Watt
WAN
Wide Area Network
L2
Layer 2, bridged connection type
L3
Layer 3, routed connection type
This manual suits for next models
1
Table of contents
Other Tosibox Network Hardware manuals
Popular Network Hardware manuals by other brands
Ruckus Wireless
Ruckus Wireless Fiber Node Quick setup guide

Mako Networks
Mako Networks Mako 8875 Product handbook

Huawei
Huawei FusionModule1000A40 ICT Solution Maintenance Guide

Barracuda
Barracuda Secure Connector quick start guide
Elvaco
Elvaco CMe3100 Quick manual

Ceragon
Ceragon FibeAir IP-20C installation guide