IBM System/360 User guide
Other IBM Desktop manuals
IBM
IBM 610 Instruction Manual

IBM
IBM NetVista A30 User manual

IBM
IBM NetVista X40 Mounting instructions

IBM
IBM HC10 - BladeCenter - 7996 User manual

IBM
IBM 5251 Series Setup guide

IBM
IBM IntelliStation M Pro Owner's manual

IBM
IBM PC 300PL Types 6862 User manual

IBM
IBM ThinkPad T40 Owner's manual

IBM
IBM NetVista A20 User manual
IBM
IBM 360 User manual

IBM
IBM NetVista A30 User manual

IBM
IBM 228350U - NetVista X41 - 2283 User manual
IBM
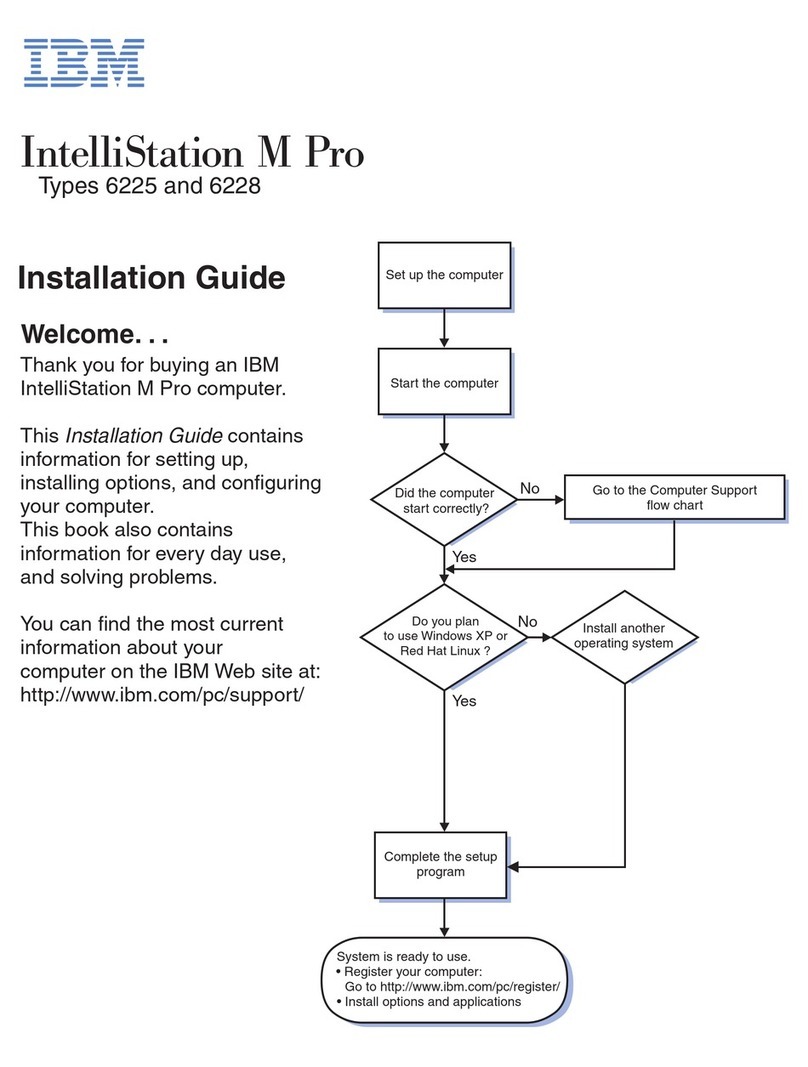
IBM IntelliStation M Pro User manual

IBM
IBM Personal System/2 60 Use and care manual

IBM
IBM NetVista A21 User manual

IBM
IBM PC 300

IBM
IBM 5100 Setup guide

IBM
IBM 8863 - eServer xSeries 366 User manual
IBM
IBM 3179 User manual

IBM
IBM NetVista A30 Troubleshooting guide