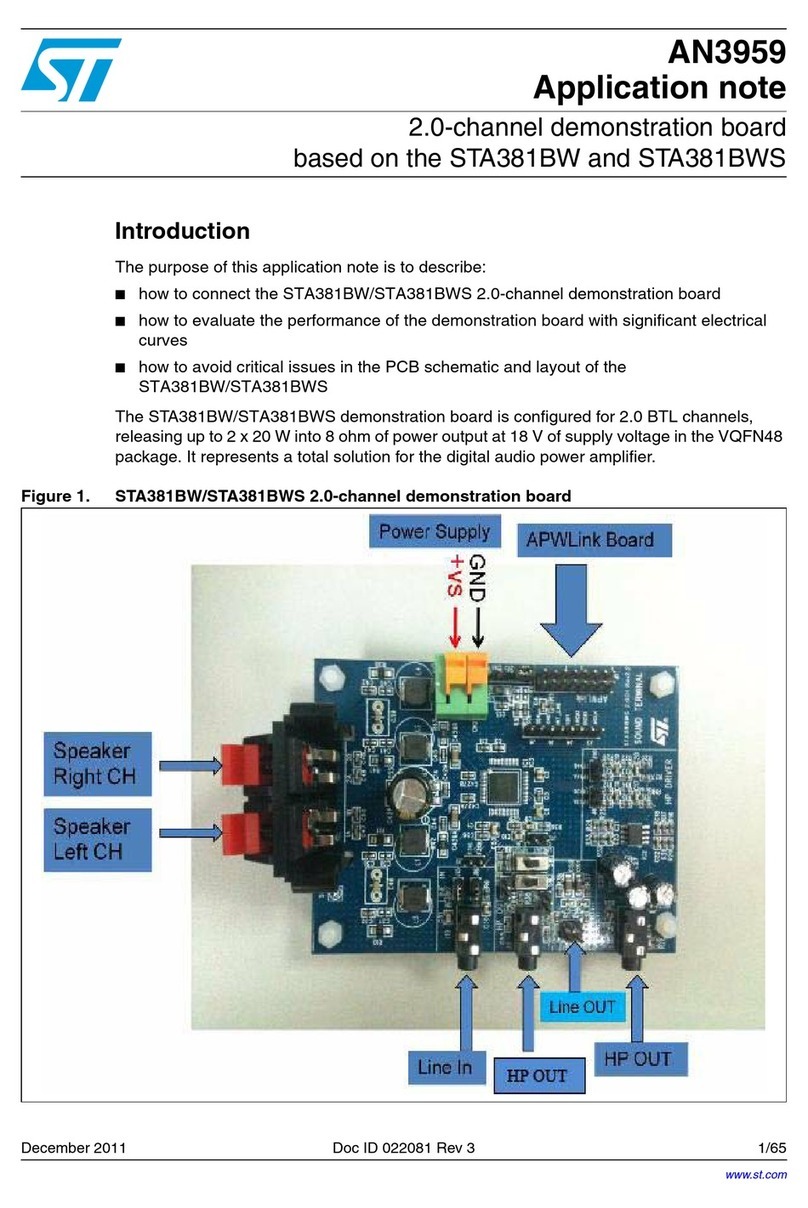
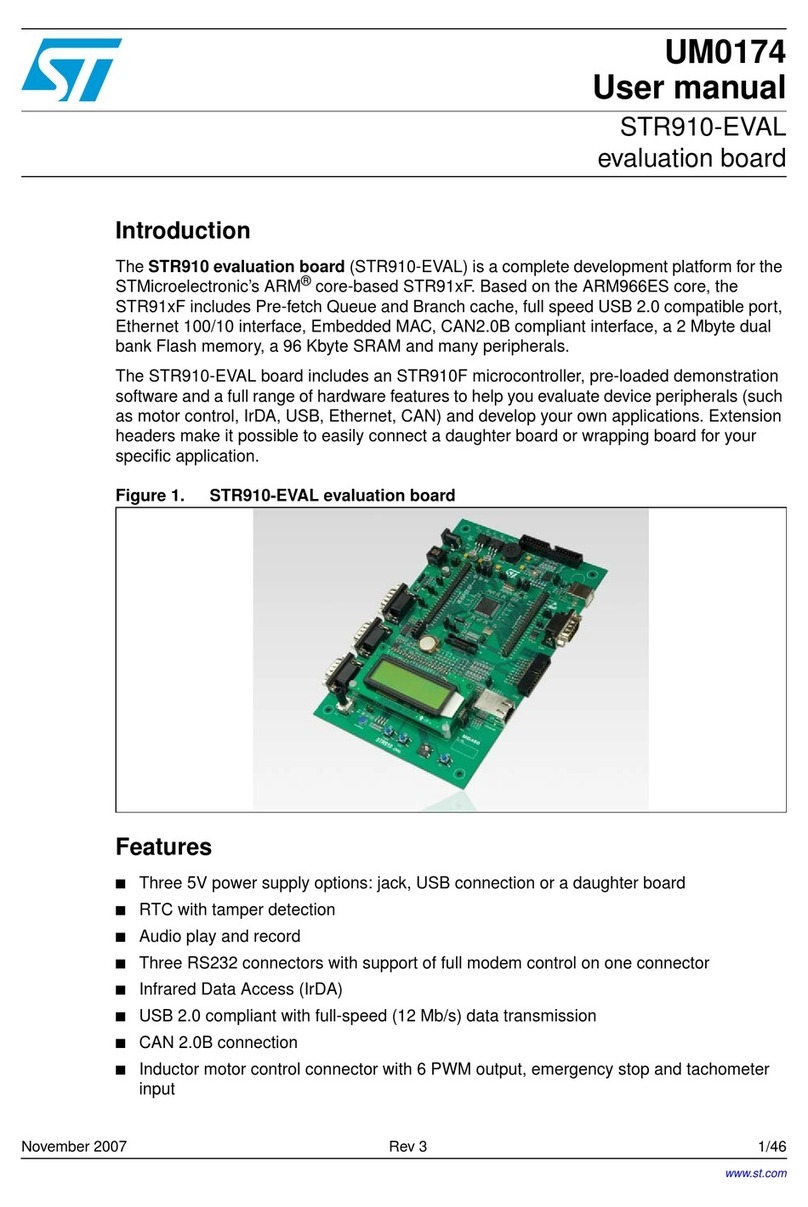
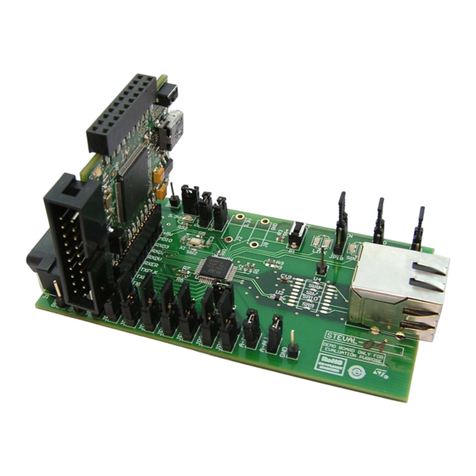
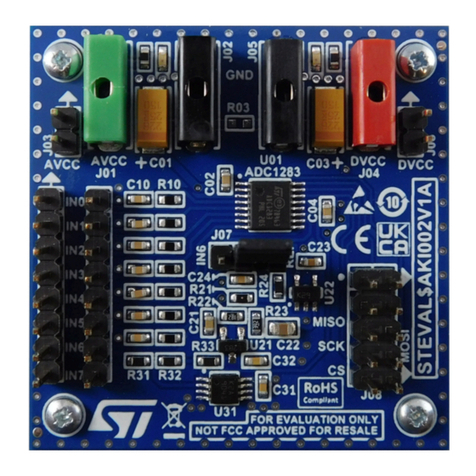
1.2 Acronyms
Table 1. Acronyms
Acronyms Meaning
NFC Near field communication
AES Advanced encryption standard
ECC Elliptic curve cryptography
FTM Fast transfer mode
STC Secure transfer channel
GCM Galois/counter mode
GMAC Galois message authentication code
1.3 Hardware equipment
The following hardware is needed for this demonstration:
• NUCLEO-L476RG board plus X-NUCLEO-NFC04A1 shield
• An iPhone (with iOS™ 13 or later) or an Android™ smartphone with at least the version 6.0 (Android™
Marshmallow)
1.4 Installation
This demonstration requires to download the firmware (STSW-ST25DV005) for the NUCLEO-L476RG board and
the Android™ executable (APK, STSW-ST25003) the iOS™ application (STSW-ST25IOS003) to be used on a
smartphone.
1.4.1 NUCLEO-L476RG and X-NUCLEO-NFC04A1 setup
The "ST25DV-I2C Crypto Demo" binary (“SBSFU_UserApp.bin”, available in STSW-ST25DV005 package) must
be uploaded on the NUCLEO-L476RG board.
To program the NUCLEO-L476RG board, go through the following steps:
1. Install the ST-LINK USB driver, available on www.st.com.
2. Connect the NUCLEO-L476RG board to a PC with the USB-mini port.
3. The NUCLEO-L476RG board icon must appear in the PC directory.
4. Drag-and-drop the "SBSFU_UserApp.bin" binary to the NUCLEO-L476RG board icon.
5. Restart the NUCLEO-L476RG board by pressing the reset (black button).
1.4.2 Android™ APK application installation
The "ST25DV-I2C Crypto Demo" Android application is available at Google Play™ store.
The STSW-ST25DV005 package contains two firmwares in the UserApp Binary directory (UserApp.sfb and
UserApp_NewPicture.sfb) to use for the secure firmware upgrade demonstration. These files have to be
downloaded on the Android™ smartphone.
1.4.3 iOS™ application installation
This application is not available on Apple® store so it must be installed manually.
The user can download the application by the OTA (over the air) programming, a method for wireless distribution
of an application and/or its updates to end-users.
On approval, application is automatically installed or it is updated if it is already installed.
Perform the following steps to install the application:
1. Use Safari® browser on your iPhone
2. Enter URL: http://myst25.com/iOSST25DVCryptoDemo/
3. Click on the blue icon on the right (see Figure 2)
4. Check iOS™ installation on your iPhone.
UM2684
Acronyms
UM2684 - Rev 2 page 3/27