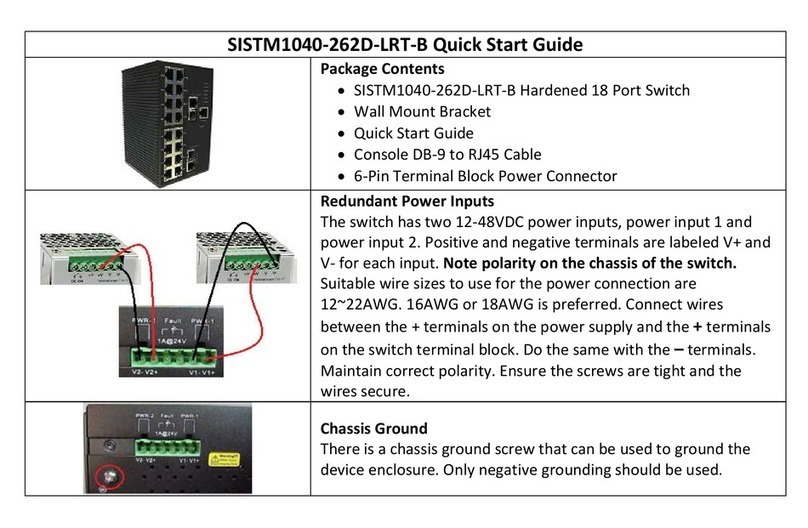
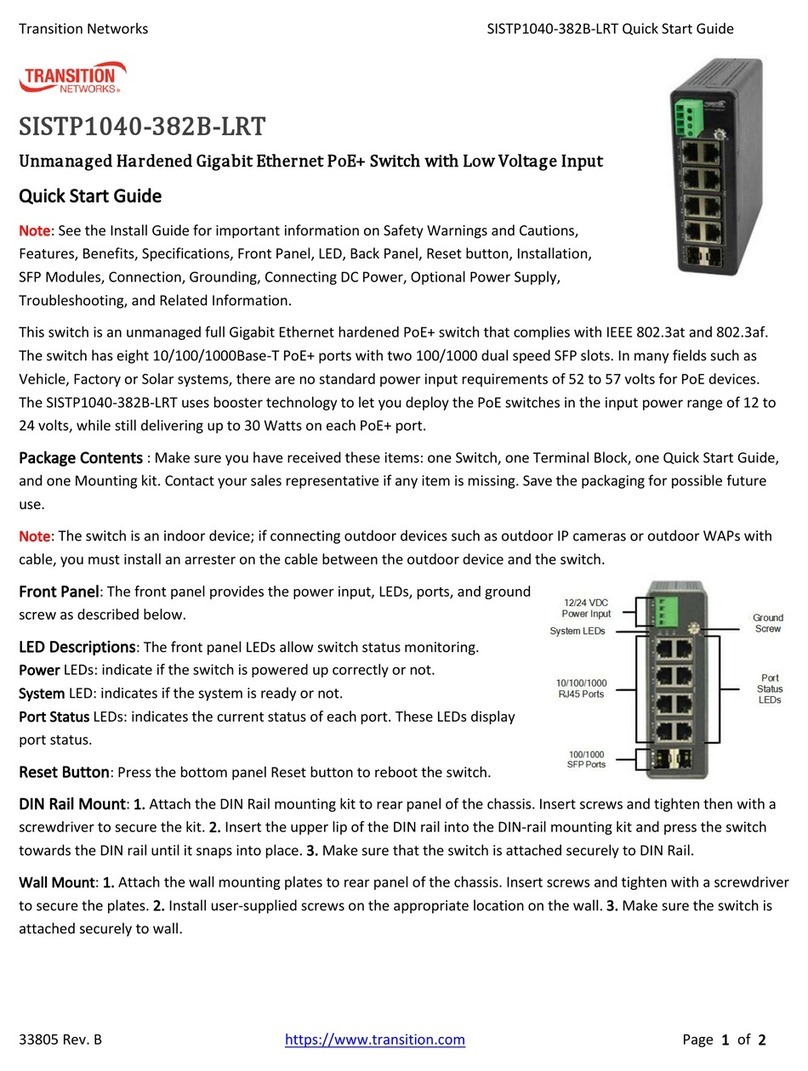
Rev.A1
18-May-11
iii
3-4-1. Mac Address Table...............................................................................................69
3-4-2. Static Filter ..........................................................................................................71
3-4-3. Static Forward.....................................................................................................72
3-4-4. MAC Alias............................................................................................................73
3-4-5. MAC Table...........................................................................................................74
3-5. GVRP ...........................................................................................................................75
3-5-1. Config...................................................................................................................75
3-5-2. Counter ................................................................................................................78
3-5-3. Group...................................................................................................................80
3-6. QOS(QUALITY OF SERVICE)CONFIGURATION..............................................................81
3-6-1. Ports.....................................................................................................................81
3-6-2. Qos Control List ..................................................................................................83
3-6-3.Rate Limiters.........................................................................................................88
3-6-4.Storm Control........................................................................................................89
3-6-5.Wizard ...................................................................................................................90
3-7. SNMPCONFIGURATION .............................................................................................100
3-8.ACL............................................................................................................................108
3-8-1.Ports....................................................................................................................108
3-8-2.Rate Limiters.......................................................................................................110
3-8-3.Access Control List.............................................................................................111
3-8-4.Wizard .................................................................................................................140
3-9. IPMAC BINDING .......................................................................................................146
3-10. 802.1X CONFIGURATION ..........................................................................................148
3-10-1.Server................................................................................................................152
3-10-2.Port Configuration ...........................................................................................154
3-10-3.Status.................................................................................................................157
3-10-4. Statistics...........................................................................................................158
3-11. TACACS+ ................................................................................................................159
3-11-1. State..................................................................................................................159
3-11-2. Authentication..................................................................................................160
3-11-3.AUTHORIZATION ....................................................................................................161
3-11-4.ACCOUNTING.........................................................................................................162
3-12.TRUNKING CONFIGURATION.....................................................................................163
3-12-1.Port ...................................................................................................................164
3-12-2 Aggregator View ...............................................................................................166
3-12-3 Aggregation Hash Mode...................................................................................167
3-12-4 LACP System Priority.......................................................................................168
3-13 STPCONFIGURATION.................................................................................................169
3-13-1. Status................................................................................................................169
3-13-2. Configuration...................................................................................................171
3-13-3. STP Port Configuration...................................................................................173
3-14 MSTP ........................................................................................................................176
3-14-1 Status.................................................................................................................176
3-14-2 Region Config...................................................................................................177
3-14-3 Instance View....................................................................................................178
3-15. MIRROR.....................................................................................................................186
3-16. MULTICAST ...............................................................................................................188
3-16-1 IGMP mode.......................................................................................................188
3-16-2 IGMP Proxy......................................................................................................189
3-16-3 IGMP Snooping................................................................................................191
3-16-4 IGMP Group Allow...........................................................................................192
3-16-5 IGMP Group Membership................................................................................193
3-16-6 MVR ..................................................................................................................194
3-16-7 MVID ................................................................................................................195