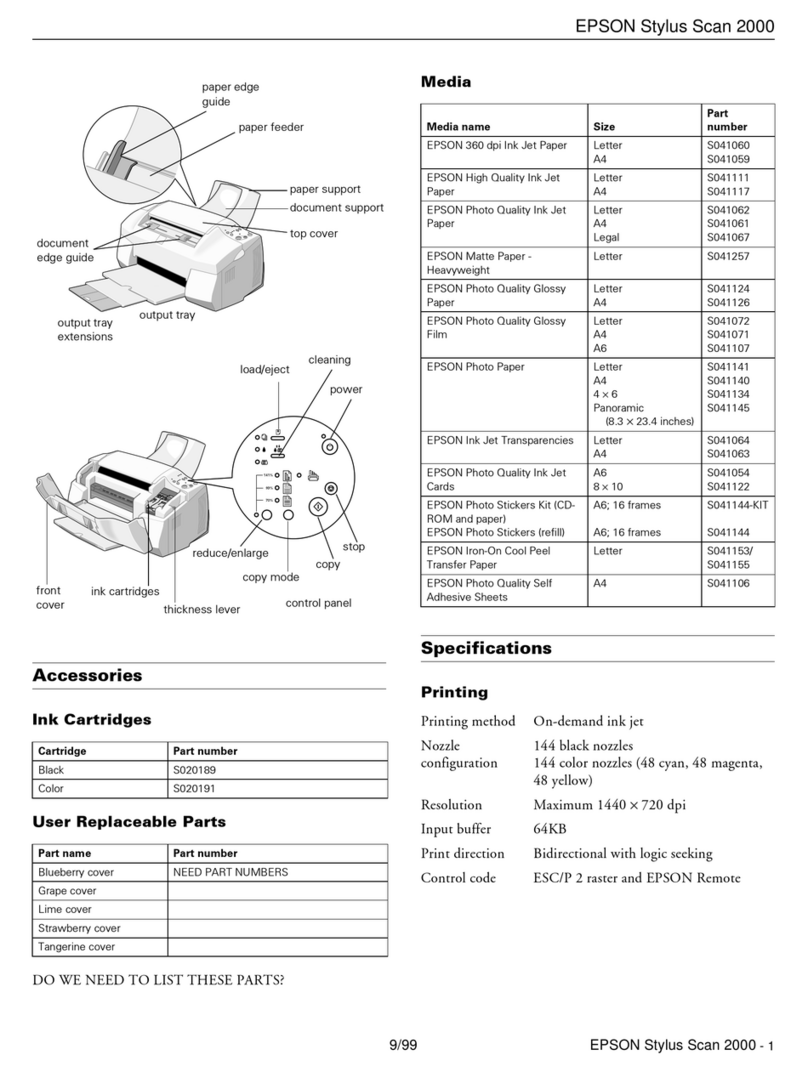
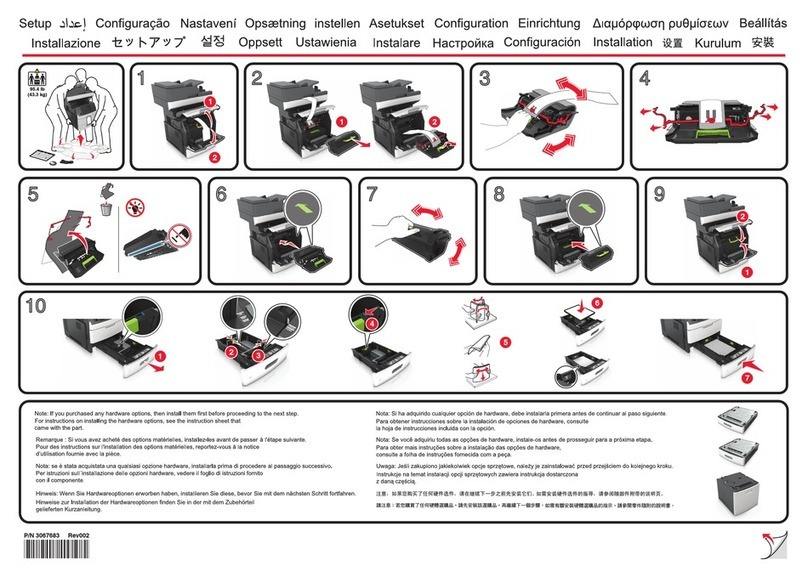
Preventing Unauthorized Access..................................................................................................................181
Access Control...........................................................................................................................................181
Enabling/Disabling Protocols..................................................................................................................182
Specifying Network Security Level..........................................................................................................190
Encrypting Transmitted Passwords...............................................................................................................194
Driver Encryption Key...............................................................................................................................194
Group Password for PDF files...................................................................................................................196
IPP Authentication Password.....................................................................................................................197
Protection Using Encryption..........................................................................................................................199
SSL (Secure Sockets Layer) Encryption....................................................................................................199
User Settings for SSL (Secure Sockets Layer)..........................................................................................204
Setting the SSL / TLS Encryption Mode...................................................................................................204
SNMPv3 Encryption.................................................................................................................................206
Transmission Using IPsec...............................................................................................................................209
Encryption and Authentication by IPsec..................................................................................................209
Encryption Key Auto Exchange Settings and Encryption Key Manual Settings...................................210
IPsec Settings.............................................................................................................................................211
Encryption Key Auto Exchange Settings Configuration Flow................................................................218
Encryption Key Manual Settings Configuration Flow.............................................................................223
telnet Setting Commands..........................................................................................................................224
Authentication by telnet.................................................................................................................................232
"authfree" Command.................................................................................................................................232
6. Specifying the Extended Security Functions
Specifying the Extended Security Functions................................................................................................233
Changing the Extended Security Functions.............................................................................................233
Procedure for Changing the Extended Security Functions.....................................................................233
Settings.......................................................................................................................................................235
Other Security Functions...............................................................................................................................240
Fax Function...............................................................................................................................................240
Scanner Function.......................................................................................................................................240
Weekly Timer Code..................................................................................................................................241
Limiting Machine Operation to Customers Only.........................................................................................244
Settings.......................................................................................................................................................244
6