OVERVIEW
This document presents a summary of security measures, factors, and configurations that users are
recommended to consider when configuring and deploying our FAP series of IP Phones.
Note: We recommend using the latest firmware for latest security patches.
The following sections are covered in this document:
•
Web UI/SSH Access
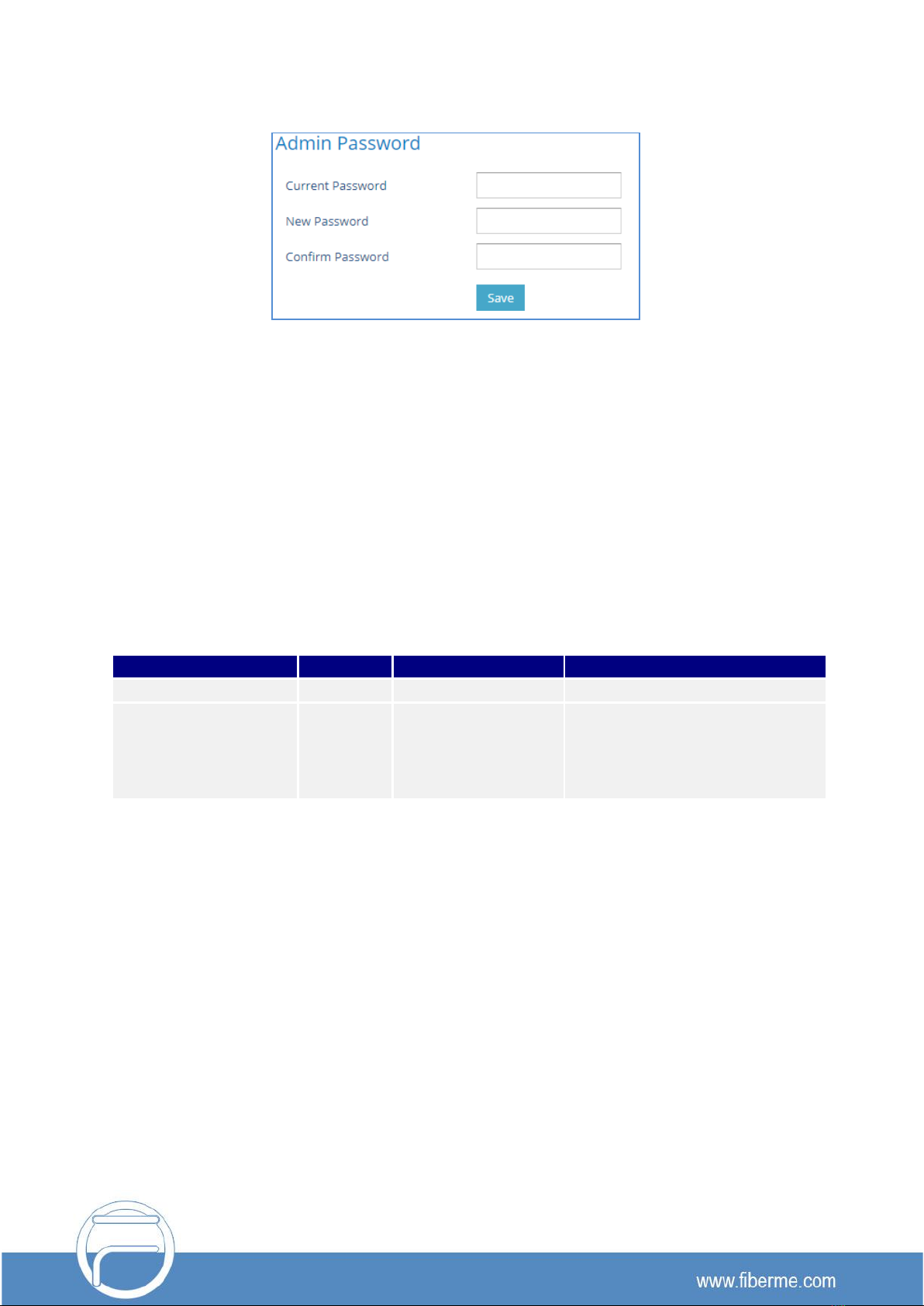
Web UI access is protected by username/password and login timeout. Three-level user management is
configurable. SSH access is supported for mainly troubleshooting purpose and it is recommended to
disable it in normal usage.
•
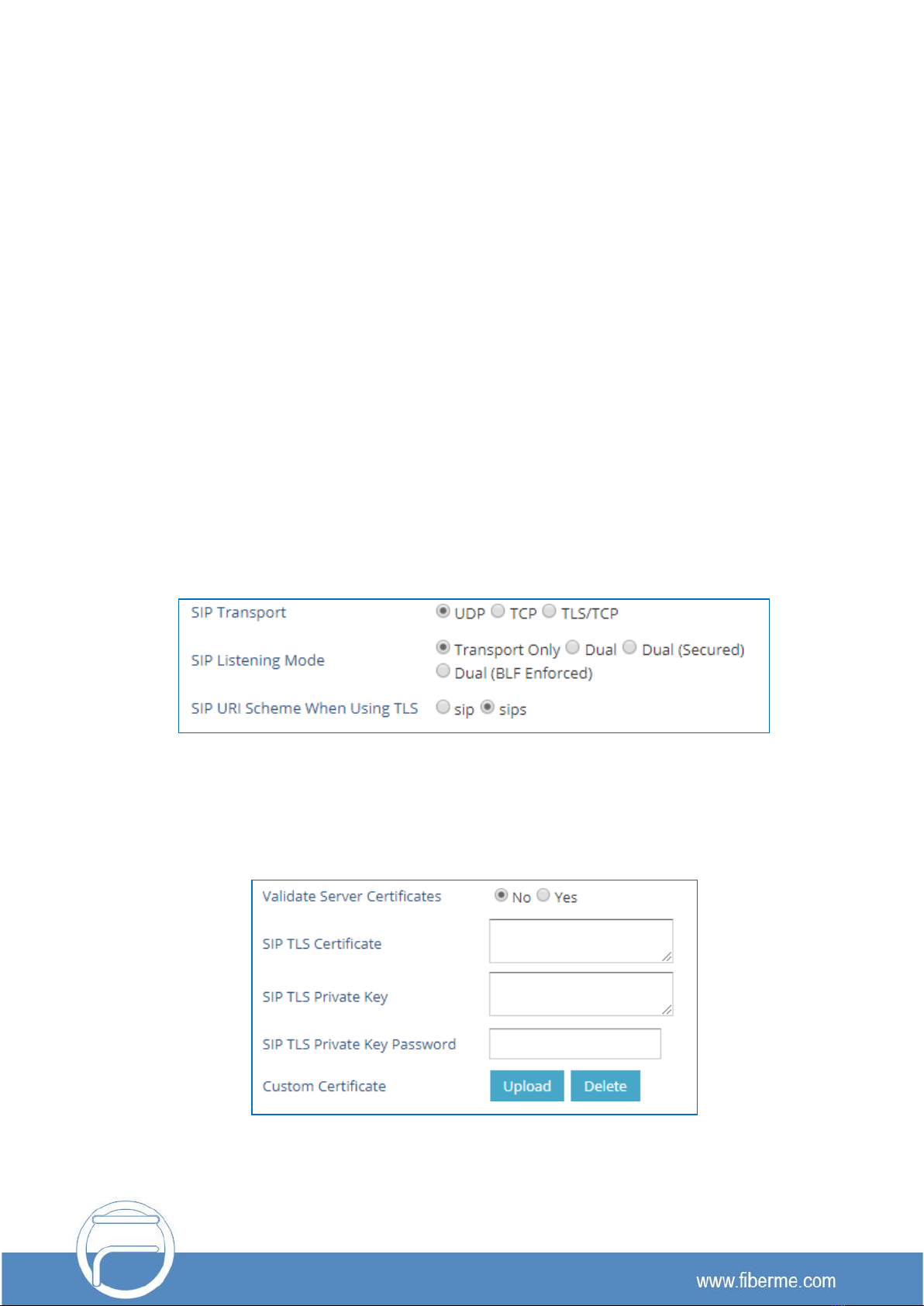
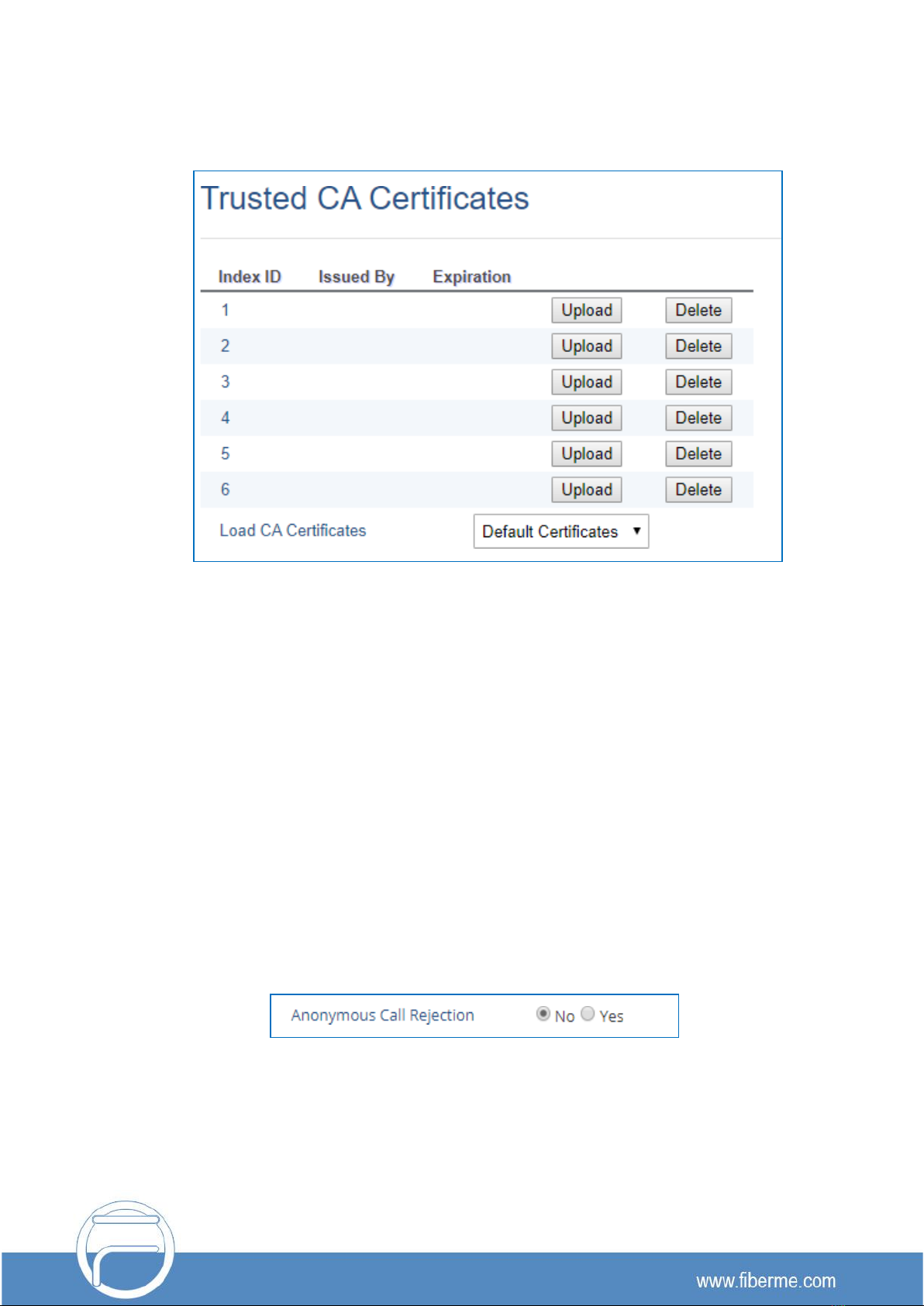
Security for SIP Accounts and Calls
The SIP accounts use specific port for signaling and media stream transmission. It also offers
configurable options to block anonymous calls and unsolicited calls.
•
Security for FAP Services
FAP supports service such as HTTP/HTTPS/TFTP/FTP/FTPS and TR-069 for provisioning. For better
security, we recommend using HTTPS/FTPS with username/password and using password-protected
XML file. We recommend disabling TR-069 (disabled by default) if not used to avoid potential port
exposure.
•
Deployment Guidelines for FAP
This section introduces protocols and ports used on the FAP and recommendations for routers/firewall
settings.
This document is subject to change without notice.
Reproduction or transmittal of the entire or any part, in any form or by any means, electronic or print, for
any purpose without the express written permission of FIBERME Communications LLC. is not permitted.