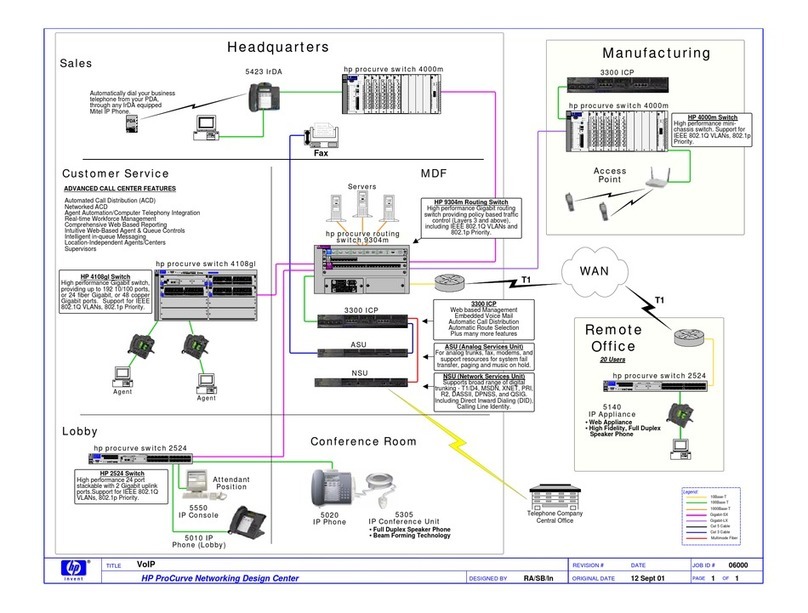
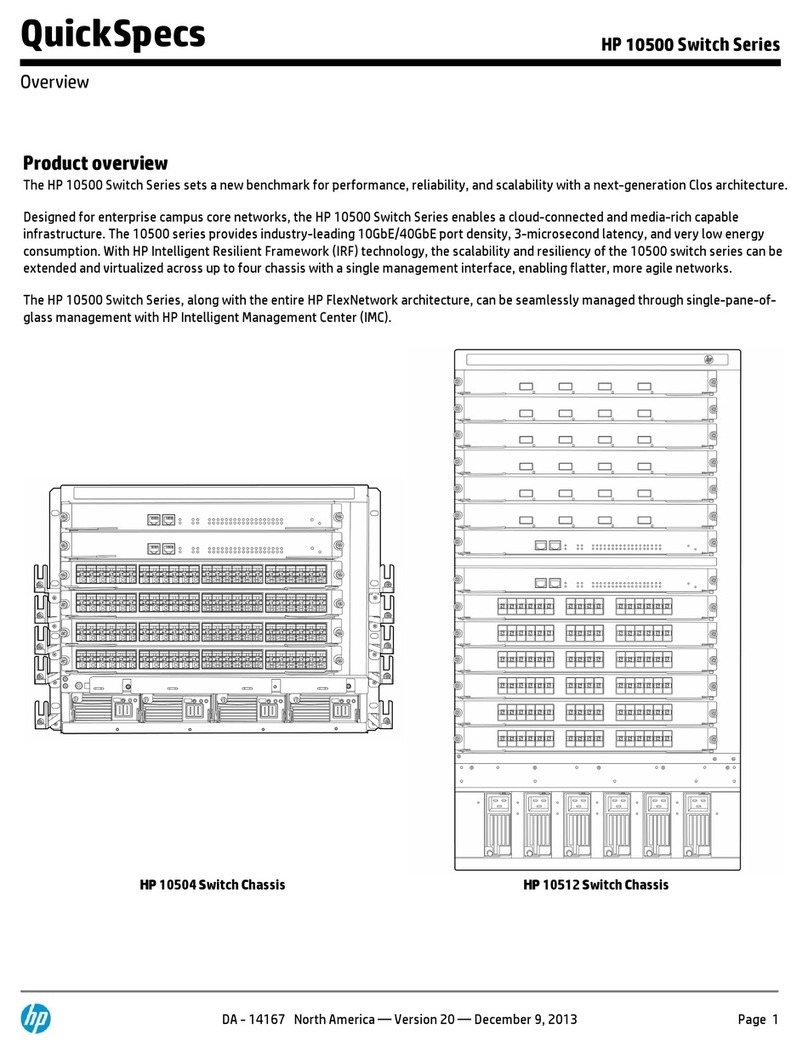
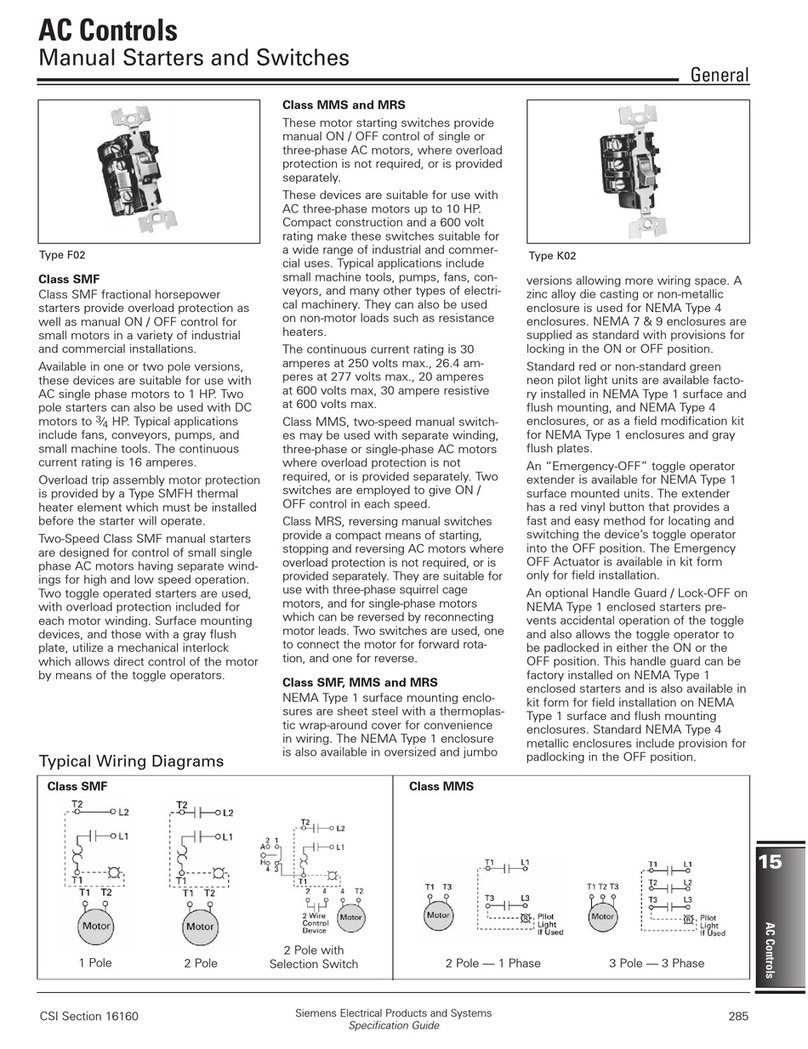
vi
Backing up the startup configuration file···················································································································121
Deleting a startup configuration file to be used at the next startup········································································122
Restoring a startup configuration file ·························································································································122
Displaying and maintaining a configuration file ······································································································123
Configuring software upgrade······························································································································· 124
Overview·······································································································································································124
Software upgrade methods·········································································································································125
Upgrading the boot ROM program through a system reboot·················································································126
Upgrading the boot file through a system reboot·····································································································127
Upgrading IRF member switch boot file ····················································································································128
Software upgrade by installing hotfixes ····················································································································129
Patch and patch file ············································································································································129
Patch types ···························································································································································129
Patch status···························································································································································129
Configuration prerequisites ································································································································132
One-step patch installation·································································································································133
Step-by-step patch installation····························································································································133
Step-by-step patch uninstallation························································································································134
Displaying and maintaining the software upgrade··································································································134
Software upgrade configuration examples···············································································································134
Immediate upgrade configuration example ·····································································································134
Hotfix configuration example·····························································································································136
Configuring ISSU ···················································································································································· 138
Overview·······································································································································································138
ISSU process ························································································································································139
Boot file version rollback ····································································································································140
Configuring ISSU ·························································································································································141
Configuration task list ·········································································································································141
Prerequisites for performing ISSU······················································································································141
Enabling version compatibility check················································································································142
Configuring ISSU·················································································································································143
Configuring the ISSU version rollback timer·····································································································145
Performing manual version rollback··················································································································146
Displaying and maintaining ISSU······················································································································146
ISSU configuration example ·······································································································································146
Current network status and requirements analysis···························································································146
Configuration procedure ····································································································································148
ISSU upgrade preparation ·································································································································150
Performing compatible ISSU upgrade···············································································································154
Performing incompatible ISSU upgrade ···········································································································155
Configuring device management··························································································································· 157
Overview·······································································································································································157
Configuring the device name ·····································································································································157
Configuring the system clock ······································································································································157
Displaying the system clock ·······························································································································158
Enabling the display of copyright information··········································································································161
Configuring banners····················································································································································161
Input modes··························································································································································162
Banner configuration example···························································································································162
Configuring the exception handling method ············································································································163
Rebooting the device ···················································································································································163
Configuring scheduled tasks·······································································································································165
Configuring a scheduled task—Approach 1 ···································································································165