IDTECH SREDKey User manual
Other IDTECH Card Reader manuals

IDTECH
IDTECH OMNI Instruction manual

IDTECH
IDTECH VP3300 OEM User manual

IDTECH
IDTECH MINIMAG Instruction manual

IDTECH
IDTECH 80140502-001 User manual

IDTECH
IDTECH ViVOpay VP5200 User manual

IDTECH
IDTECH MINIMAG User manual

IDTECH
IDTECH Spectrum IIa User manual

IDTECH
IDTECH EzWriter User manual

IDTECH
IDTECH SREDKey Instruction manual
IDTECH
IDTECH MiniSmart II User manual

IDTECH
IDTECH MINIMAG User manual

IDTECH
IDTECH VP3300 User manual

IDTECH
IDTECH SecureMag User manual

IDTECH
IDTECH BT Mag User manual

IDTECH
IDTECH iMag User manual

IDTECH
IDTECH Xpress CM100 Instruction Manual

IDTECH
IDTECH MiniSmart II Installation manual

IDTECH
IDTECH Kiosk V User manual

IDTECH
IDTECH MiniMag RS232 User manual

IDTECH
IDTECH SmartPIN L80 User manual
Popular Card Reader manuals by other brands
Logic Controls
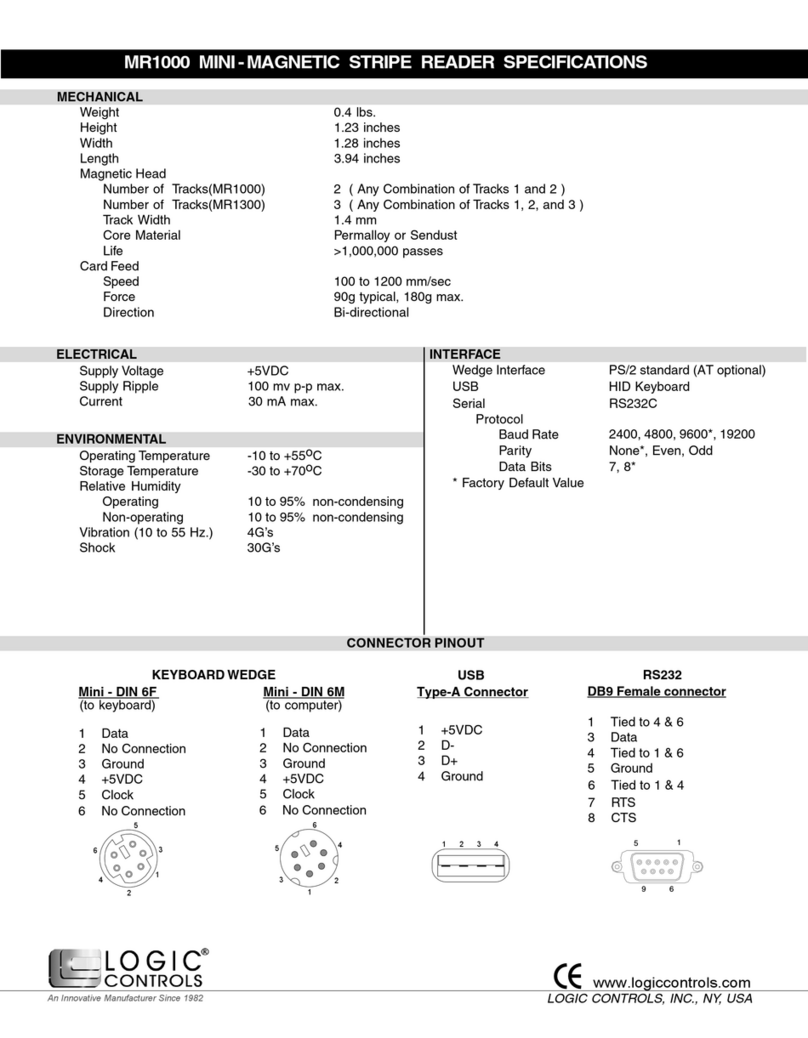
Logic Controls MR1000 Specifications
Addonics Technologies
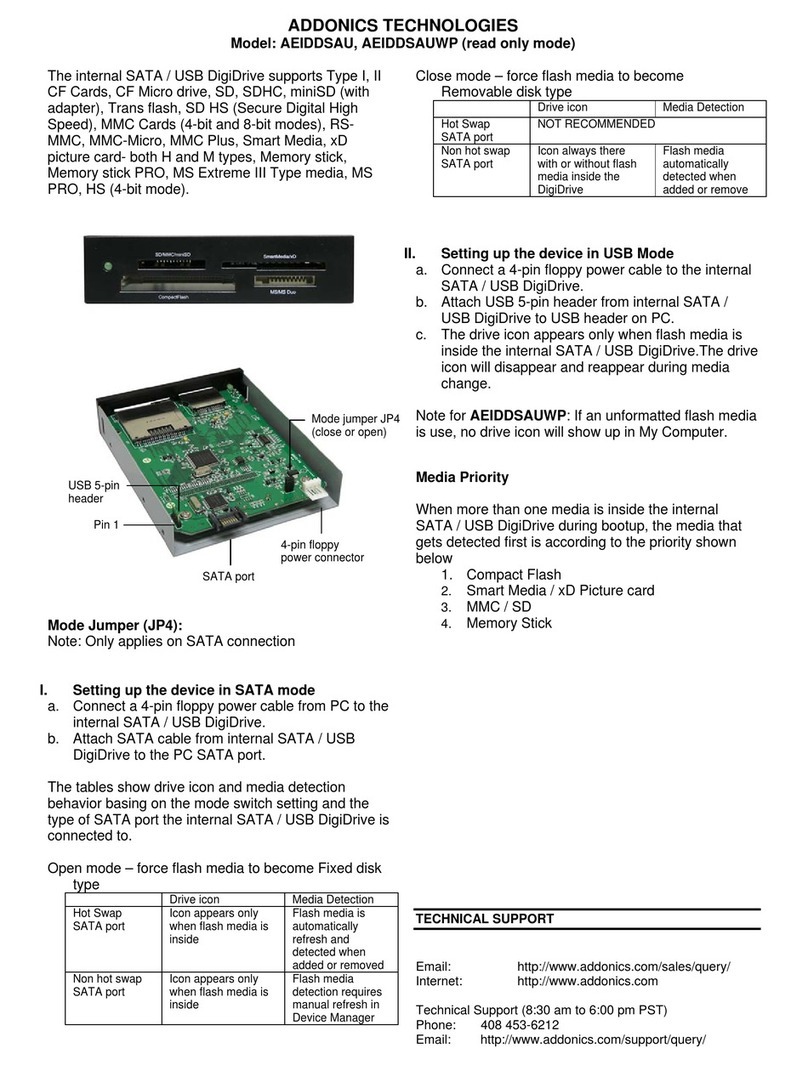
Addonics Technologies AEIDDSAU manual

Molecular Devices
Molecular Devices FlexStation 3 user guide

Apotop
Apotop Wi-Copy DW21 manual

SCM Microsystems
SCM Microsystems Microtech CameraMate CompactFlash Quick-Start Installation and Operating Instructions

ACS
ACS ACR122U user manual