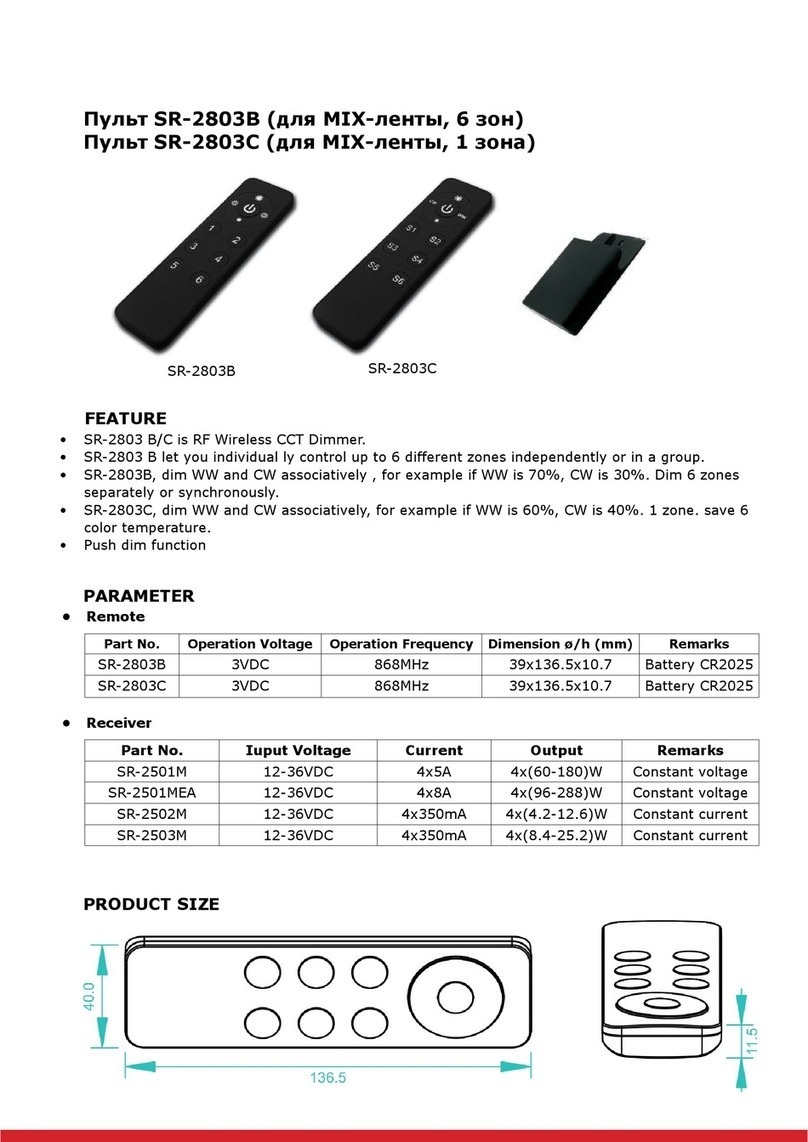
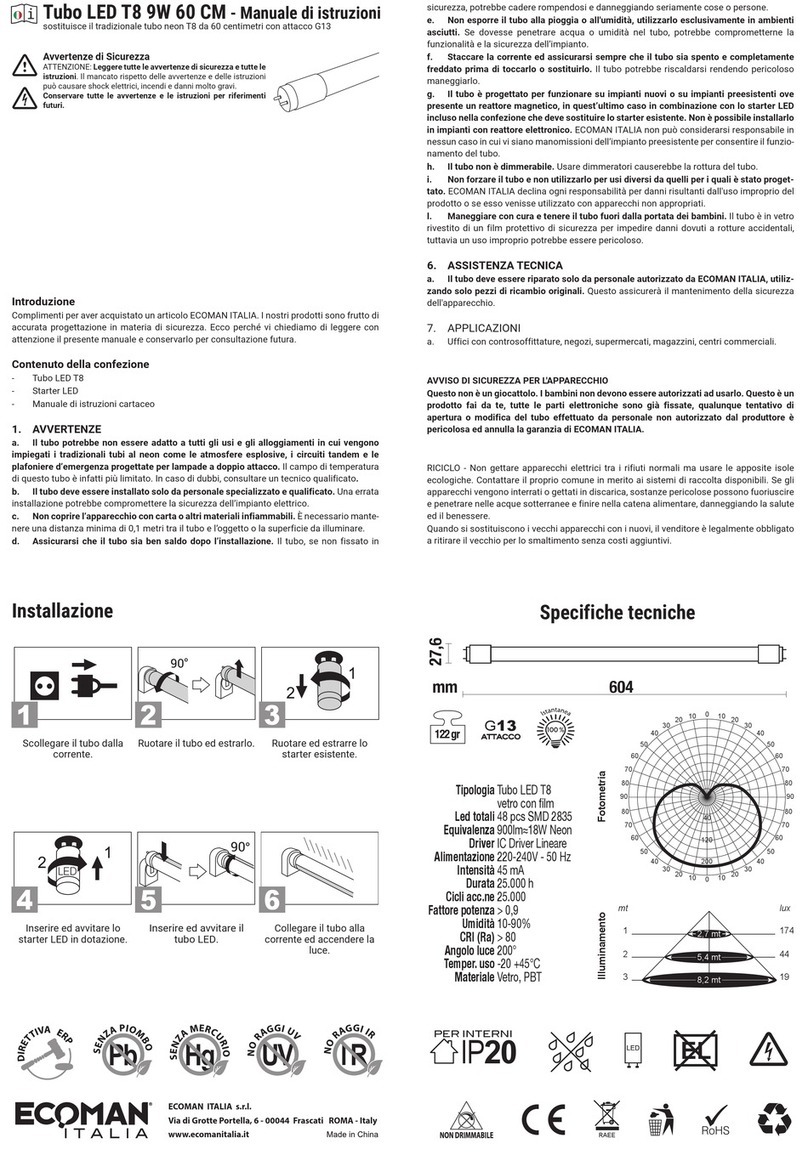
Figure 18 – AES128 Nonce structure
The AES128 Nonce and the 128 bit device-unique security key are then used to calculate a 32 bit signature of
the authenticated telegram payload shown in Figure 19 below.
Figure 19 – Authenticated payload
The calculated 32 bit signature is then appended to the data telegram payload as shown in Figure 14 in chapter
4.6.
In addition to the RFC3610 standard itself, please consult also Appendix C for a step by step description of the
authentication process.
5. Commissioning
Commissioning is the process by which SR-SBP2801-BLE-E is learned into a receiver (actuator, controller,
gateway, etc.).
The following two tasks are required in this process:
1.Device identification
The receiver needs to know how to uniquely identify this specific SR-SBP2801-BLE-E device. This is achieved
by using a unique 48 Bit ID (Source Address) for each SR-SBP2801-BLE-E
device as described in chapter 4.4. In addition, up to 4 byte of Optional Data can be
configured as described in chapter 6.7.8
2.Security parameter exchange
The receiver needs to be able to authenticate radio telegrams from SR-SBP2801-BLE-E in order to ensure that
they originate from this specific device and have not been modified as described in chapter 4.6.3. This is
achieved by exchanging a 128 Bit random security key used by SR-SBP2801-BLE-E to authenticate its radio
telegrams.
SR-SBP2801-BLE-E provides the following options for these tasks:
1.NFC-based commissioning
The SR-SBP2801-BLE-E parameters are read by a suitable commissioning tool (e.g. NFC
smartphone with suitable software) which is already part of the network into which
SR-SBP2801-BLE-E will be commissioned. The commissioning tool then communicates these parameters to
the intended receiver of SR-SBP2801-BLE-E radio telegrams. NFC-based commissioning is described in
chapter 6
2.Camera-based commissioning
Each SR-SBP2801-BLE-E module contains an optically readable QR Code which identifies its
ID and its security key. This QR code can be read by a by a suitable commissioning tool (e.g. smart phone)
which is already part of the network into which SR-SBP2801-BLE-E will be commissioned. The commissioning
tool then communicates these parameters to the intended receiver of SR-SBP2801-BLE-E radio telegrams.
The QR code structure is described in chapter 7.2.
3.Radio-based commissioning
SR-SBP2801-BLE-E can communicate its parameters via special radio telegrams (commission- ing telegrams)
to the intended receiver. To do so, SR-SBP2801-BLE-E can be temporarily
placed into radio-based commissioning mode as described in chapter 5.3
5.1 NFC-based commissioning
All required SR-SBP2801-BLE-E parameters can be read via a suitable NFC reader and writer sup- porting the
ISO/IEC 14443 Part 2 and 3 standards. The actual NFC implementation in SBP
2801 uses a Mifare Ultralight tag.
Commissioning via NFC should follow these steps:
1. Unlock SR-SBP2801-BLE-E using the default NFC PIN code 0x0000E215
2. Read the SR-SBP2801-BLE-E Source Address, Security Key and Sequence Counter and configure the
receiver accordingly
3. Important: The pre-programmed random security key used by SR-SBP2801-BLE-E can be obtained both
from the product DMC code as described in chapter 5.2, from received commissioning telegrams as described
in chapter 5.3 and via the NFC interface.
For security-critical applications where unauthorized users could have physical access to the switch it is
therefore strongly recommended to change the security key to a new security key as part of the NFC-based
commissioning process. To do so, follow the procedure outlined in chapter 6.7.5.
For additional security, NFC read-out of the new security key can be disabled by setting the PRIVATE
SECURITY KEY flag in the Configuration register before setting the new security key.
This ensures that even persons knowing the correct PIN code to configure this specific switch cannot read out
the programmed new security key. Please verify that you have properly documented the new security key as
there is no possibility to retrieve this after it has been written.
4. Important: It is strongly recommended to disable radio-based commissioning after programming a new
security key. This ensures that the new security key cannot be read out by triggering a commissioning telegram
as described in chapter 5.3.
To disable radio-based commissioning, set the DISABLE LRN TELEGRAM flag in the Configuration register to
0b1, see chapter 6.7.3.
5. Important: You should always change the NFC PIN code from its default setting to a new NFC PIN code and
lock the NFC configuration interface. This step is mandatory to avoid access to the SR-SBP2801-BLE-E
configuration using the default PIN code.
Should you lose the new NFC PIN code then SR-SBP2801-BLE-E can be reset to factory mode
(with the default NFC PIN code) by means of a factory reset as described in chapter
5.4. For security reasons, this factory reset will always reset the security key to its pre-programmed value.
5.2 Camera-based commissioning
Sequence counter, source address and the remaining telegram data together form the in- put data for the
signature algorithm. This algorithm uses AES128 encryption based on the device-unique random security key
to generate a 32 bit signature which will be transmitted as part of the radio telegram.
The signature is therefore dependent both on the current value of the sequence counter, the device source
address and the telegram payload. Changing any of these three parameters will therefore result in a different
signature.
The receiver performs the same signature calculation based on sequence counter, source address and the
remaining telegram data of the received telegram using the security key it received from SR-SBP2801-BLE-E
during commissioning.
The receiver then compares the signature reported as part of the telegram with the signature it has calculated.
If these two signatures match, then the following statements are true:
1.Transmitter (SR-SBP2801-BLE-E) and receiver use the same security key
2.The message content (address, sequence counter, data) has not been modified
At this point, the receiver has validated that the message originates from a trusted transmitter (as identified by
its security key) and that its content is valid.
In order to avoid message replay (capture and retransmission of a valid message), it is required that the
receiver tracks the value of the sequence counter used by SR-SBP2801-BLE-E and only accepts messages
with higher sequence counter values (i.e. not accepts equal or lower sequence counter values for subsequent
telegrams).
4.7.1 Authentication implementation
SR-SBP2801-BLE-E implements data telegram authentication based on AES128 in CCM (Counter with CBC-
MAC) mode as described in IETF RFC3610. At the time of writing, the RFC3610 standard could be found here:
https://www.ietf.org/rfc/rfc3610.txt
The 13 Byte CCM Nonce (number used once – unique) initialization value is constructed as concatenation of 6
byte Source Address, 4 byte Sequence Counter and 3 bytes of value
0x00 (for padding).
Note that both Source Address and Sequence Counter use little endian format (least significant byte first).
Figure 18 below shows the structure of the AES128 Nonce.