Contents 3
Contents
Overview .................................................................. 4
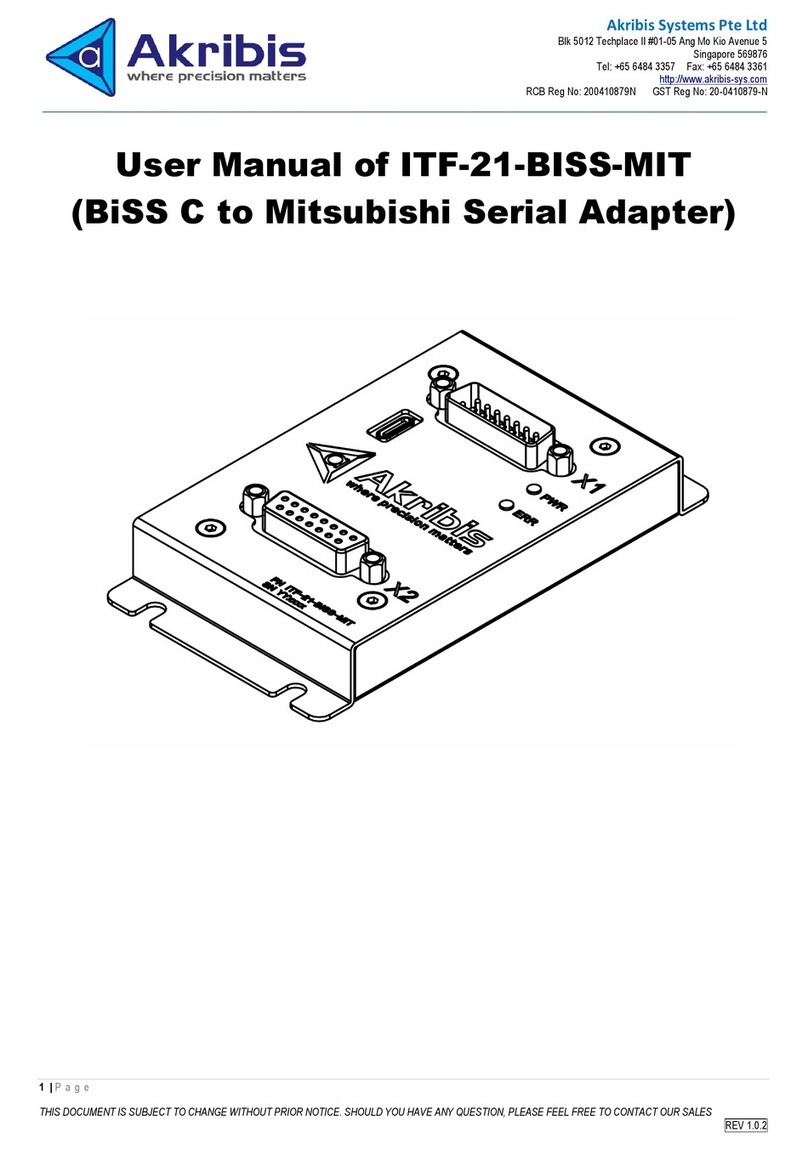
1. Installation Instructions ...................................... 5
Installing and Connecting the Adapter.................... 6
The Adapter LED.................................................... 9
2. Setting Security ................................................. 10
Accessing the Security Screen............................. 11
WPA2-PSK (Pre-Shared Key) .............................. 14
WPA-PSK (Pre-Shared Key) ................................ 15
WEP (Wired Equivalent Privacy) .......................... 16
WPA2 ................................................................... 18
WPA ..................................................................... 20
Certificate (WPA2 and WPA)................................ 23
WiFi™ Protected Setup (WPS) ............................ 24
Changing your Security Setting ............................ 26
3. Advanced Options............................................. 27
Creating Profiles................................................... 27
Monitoring Link Status.......................................... 30
Using Site Survey and Rescan............................. 31
Advanced Configuration ....................................... 33
Appendix A. TCP/IP Settings................................ 34
Appendix B. Troubleshooting .............................. 41
Appendix C. Technical Support ........................... 43
Appendix D. Regulatory Information ................... 47