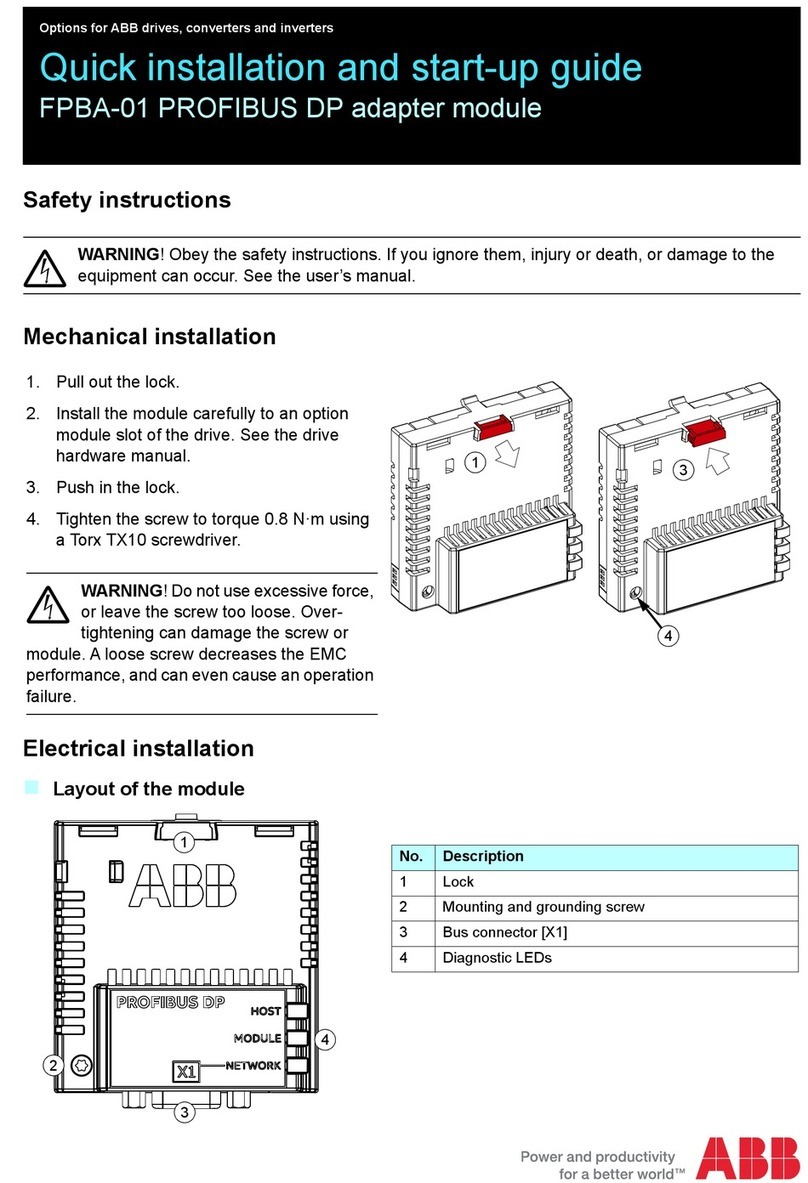
4| XIO USER MANUAL | 2106424MNAB
6Basic troubleshooting .................................................................................................... 104
6.1 RMC unable to detect or communicate with the XIO ........................................................104
6.1.1 Verify RMC-XIO connection (physical connection) ...............................................106
6.1.2 Verify the IP parameter configuration (IP communication) ...................................107
6.2 XIO applications not displaying on the RMC....................................................................110
6.3 RMC failure to receive data from XIO passthrough ..........................................................112
6.3.1 Missing or mismatched TCP port......................................................................113
6.3.2 Missing or incorrect XIO serial port ..................................................................114
6.3.3 Incorrect protocol selection ............................................................................116
6.3.4 Mismatched serial communication parameters ...................................................116
6.4 Fail Safe Watchdog alarm does not clear .......................................................................118
6.5 Network Diagnostic Tools............................................................................................121
7Configure security (recommended) ................................................................................ 121
7.1 Access points............................................................................................................121
7.2 Communication interfaces...........................................................................................121
7.2.1 User-enabled services ...................................................................................122
7.2.2 Open Transmission Control Protocol (TCP) ports.................................................122
7.3 Denial of service (DOS) threshold rates.........................................................................124
7.4 Security guidelines ....................................................................................................124
7.5 Configure bi-level security with security switch ...............................................................125
7.5.1 Configure non-default XIO security code on the RMC ..........................................127
7.6 Configure Role-Based Access Control (RBAC) .................................................................128
7.6.1 Default access roles ......................................................................................128
7.6.2 Set up and create a new RBAC security control file .............................................129
7.6.3 Edit the security file ......................................................................................130
7.6.4 Create a new user account .............................................................................130
7.6.5 Enable RBAC authentication on communication ports ..........................................134
7.7 Secure the SSH/SFTP service ......................................................................................137
7.7.1 Supported SSH/SFTP accounts ........................................................................137
7.7.2 SSH/SFTP authentication ...............................................................................138
7.7.3 Update default SSH/SFTP keys........................................................................138
7.7.4 Enable SSH/SFTP..........................................................................................152
8Service and maintenance ............................................................................................... 152
8.1Preserve data and configuration...................................................................................153
8.1.1 Collect data .................................................................................................153
8.1.2 Save the device configuration .........................................................................156
8.2 Restore the device configuration ..................................................................................161
8.3 Use the configuration from another XIO ........................................................................163
8.4 Update device software ..............................................................................................165
8.4.1 Security requirements before upgrade..............................................................165
8.4.2 When to upgrade ..........................................................................................165