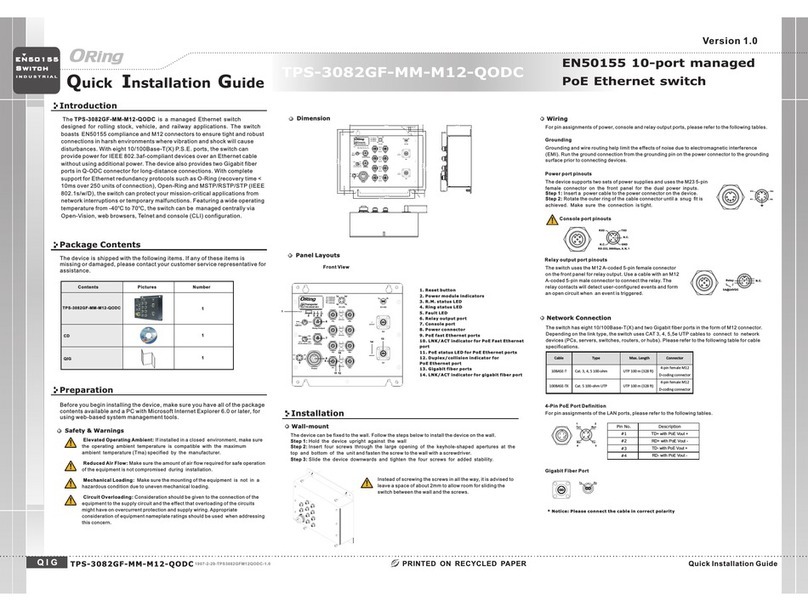
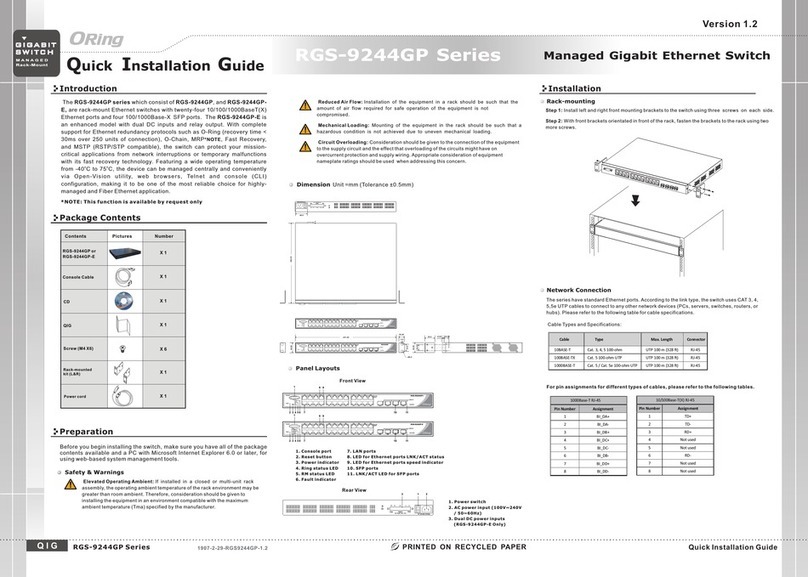
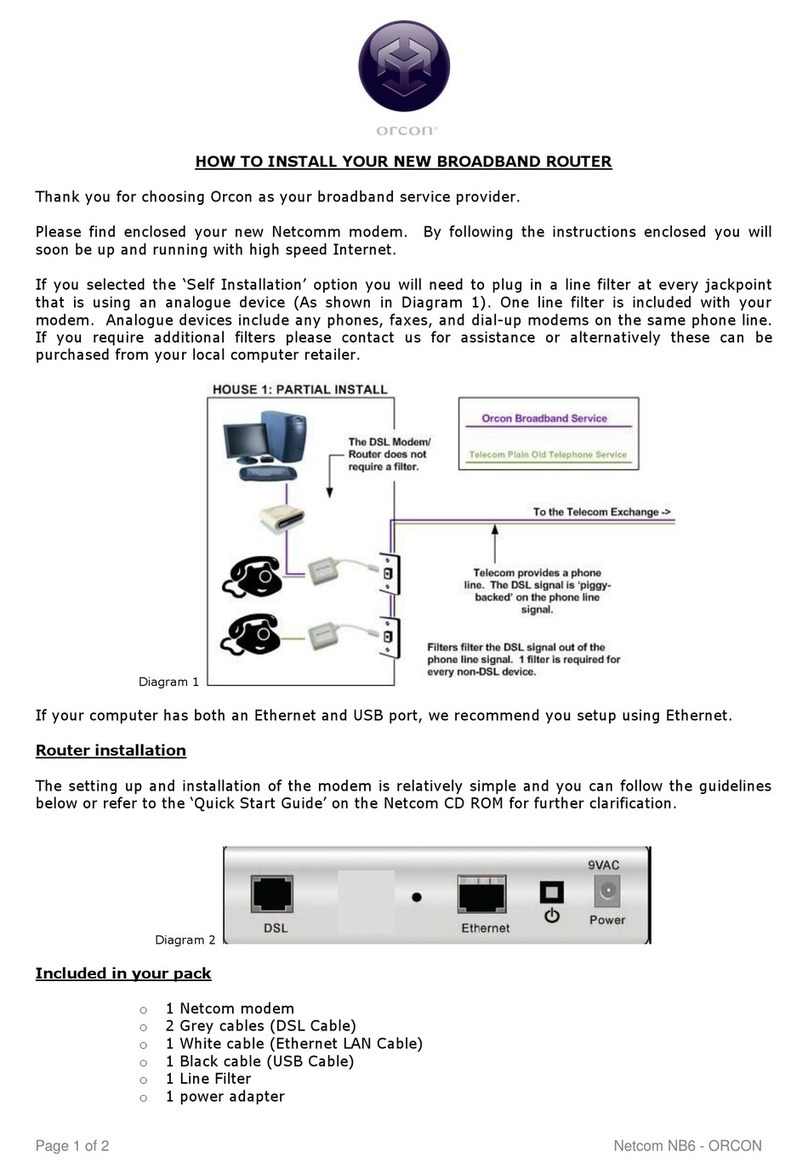
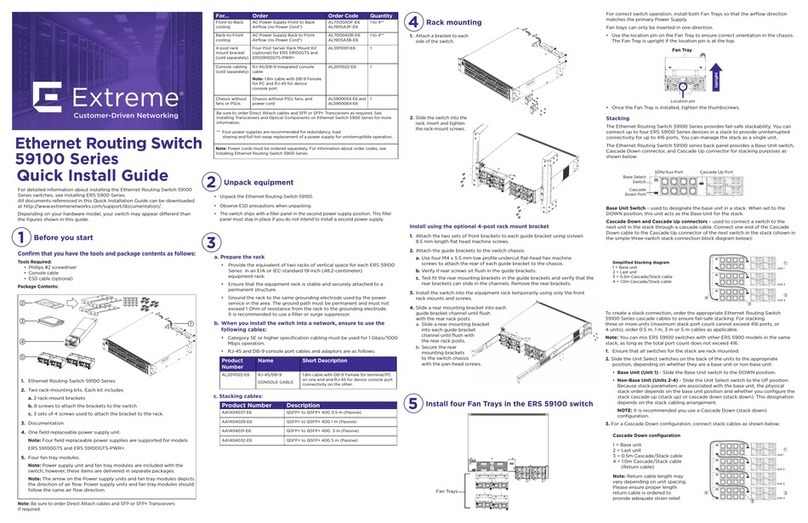
IES-3082GC User Manual
ORing Industrial Networking Corp. 3
5.1.1.1 MRP ......................................................................................................27
5.1.1.2 O-Ring...................................................................................................28
5.1.1.3 Oen-Ring ...............................................................................................30
5.1.1.4 O-Chain.................................................................................................31
5.1.1.5 RSTP – Repeater...................................................................................32
5.1.1.6 Fast Recovery........................................................................................32
5.1.1.7 RSTP.....................................................................................................33
5.1.1.8 MSTP.....................................................................................................36
5.1.2 Multicast.........................................................................................................40
5.1.2.1 IGMP Snooping......................................................................................40
5.1.2.2 MVR ......................................................................................................41
5.1.2.3 Static Multicast Filtering..........................................................................41
5.1.3 Port Setting ....................................................................................................42
5.1.3.1 Port Control............................................................................................42
5.1.3.2 Port Status.............................................................................................43
5.1.3.3 Port Alias................................................................................................43
5.1.3.4 Rate Limit...............................................................................................43
5.1.3.5 Port Trunking..........................................................................................44
5.1.3.6 Loop Guard............................................................................................46
5.1.4 VLAN .............................................................................................................46
5.1.4.1 VLAN Setting- IEEE 802.1Q...................................................................47
5.1.4.2 VLAN Setting – Port Based ....................................................................48
5.1.5 Traffic Prioritization.........................................................................................49
5.1.5.1 QoS Policy.............................................................................................49
5.1.5.2 Port-base Priority ...................................................................................50
5.1.5.3 COS/802.1p...........................................................................................51
5.1.5.4 TOS/DSCP.............................................................................................52
5.1.6 DHCP Server..................................................................................................52
5.1.6.1 Basic Setting..........................................................................................52
5.1.6.2 DHCP Server – Client List......................................................................53
5.1.6.3 DHCP Server – Port and IP Bindings......................................................53
5.1.6.4 DHCP Server –DHCP Relay Agent.........................................................54
5.1.7 SNMP.............................................................................................................55
5.1.7.1 SNMP – Agent Setting............................................................................55
5.1.7.2 SNMP –Trap Setting...............................................................................56
5.1.7.3 SNMPV3................................................................................................57
5.1.8 Security..........................................................................................................58