Siemens SINAMICS G120P CU230P-2 Administrator guide
Other Siemens Control Unit manuals

Siemens
Siemens Simatic S7-1500/ET 200MP User manual

Siemens
Siemens LOGO! CMR2020 User manual

Siemens
Siemens SIMATIC ET 200SP User manual

Siemens
Siemens SINUMERIK 840D sl Owner's manual

Siemens
Siemens SIMATIC ET 200SP User manual

Siemens
Siemens 3VL9800-3MJ00 User manual

Siemens
Siemens Simatic S7-1500 User manual
Siemens
Siemens SIRIUS ACT 3ZX1012-0SU14-1KA1 User manual

Siemens
Siemens SCALANCE S623 User manual

Siemens
Siemens XLD-1 User manual

Siemens
Siemens PROFIBUS CP 1542-5 User manual

Siemens
Siemens SIMATIC ET 200eco PN Technical Document

Siemens
Siemens SINAMICS S120 Technical Document

Siemens
Siemens SENTRON PAC PROFIBUS DP User manual

Siemens
Siemens HOTEL SOLUTION HTC3.1/A User manual

Siemens
Siemens SINAMICS V60 User manual

Siemens
Siemens IM 328-N Operating and installation instructions

Siemens
Siemens SIRIUS 3SB3 User manual

Siemens
Siemens MPS-6 User manual

Siemens
Siemens SIMATIC S5 User manual
Popular Control Unit manuals by other brands
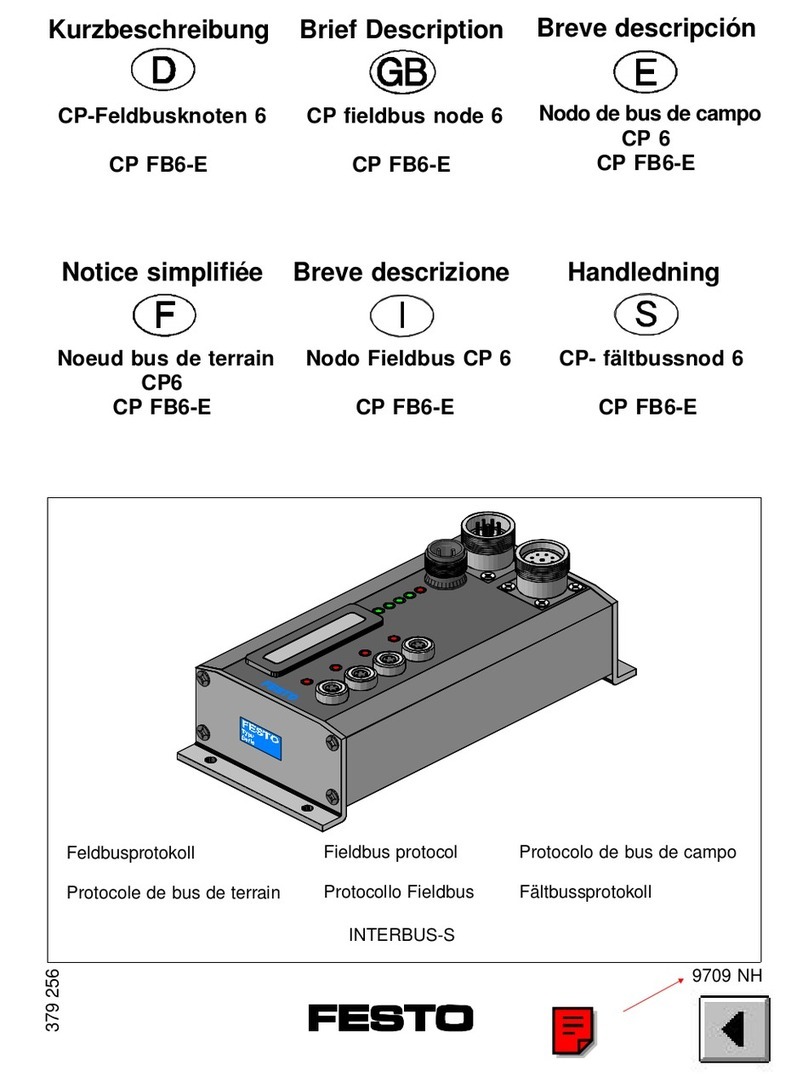
Festo
Festo Compact Performance CP-FB6-E Brief description
Elo TouchSystems
Elo TouchSystems DMS-SA19P-EXTME Quick installation guide

JS Automation
JS Automation MPC3034A user manual

JAUDT
JAUDT SW GII 6406 Series Translation of the original operating instructions
Spektrum
Spektrum Air Module System manual

BOC Edwards
BOC Edwards Q Series instruction manual

KHADAS
KHADAS BT Magic quick start

Etherma
Etherma eNEXHO-IL Assembly and operating instructions

PMFoundations
PMFoundations Attenuverter Assembly guide

GEA
GEA VARIVENT Operating instruction

Walther Systemtechnik
Walther Systemtechnik VMS-05 Assembly instructions
Altronix
Altronix LINQ8PD Installation and programming manual