Dräger Infinity M300 series User manual
Other Dräger Medical Equipment manuals

Dräger
Dräger HP NO Series User manual

Dräger
Dräger Evita 2 Dura Supplement

Dräger
Dräger Atlan User manual
Dräger
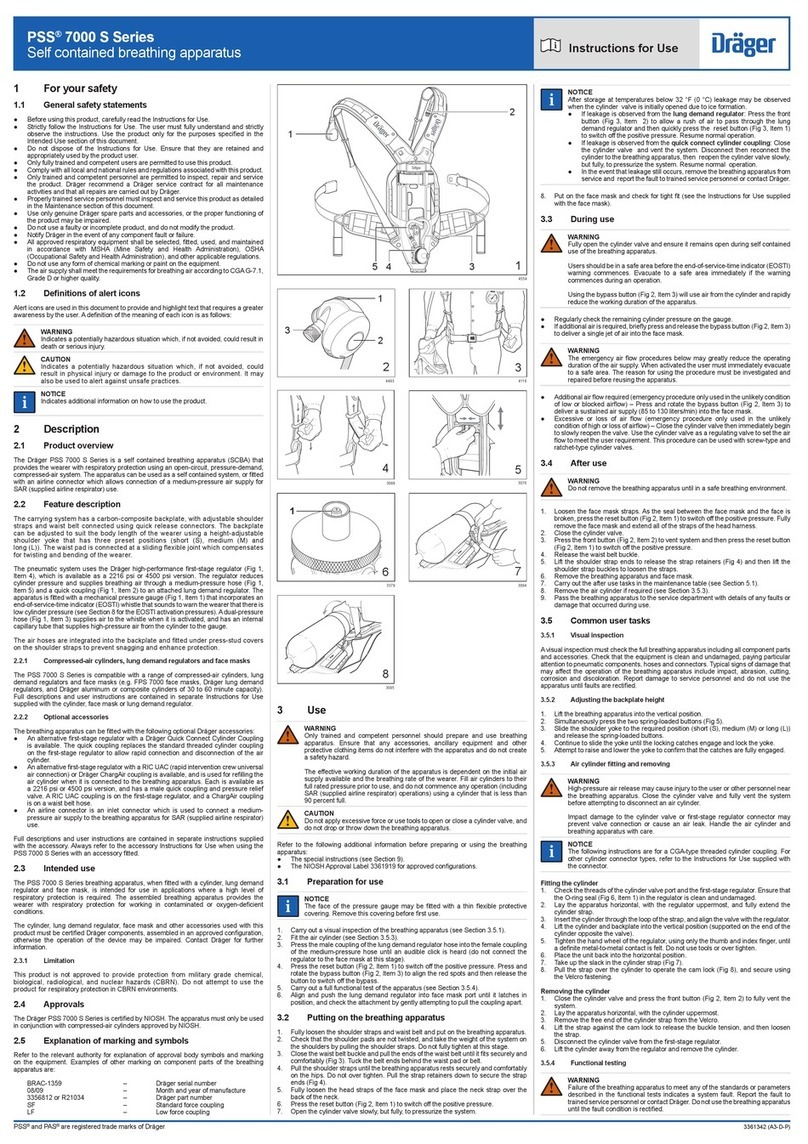
Dräger PSS 7000 S Series User manual

Dräger
Dräger Evita 4 Supplement

Dräger
Dräger Novametrix User manual

Dräger
Dräger Primus Quick start guide

Dräger
Dräger Fabius plus User manual
Dräger
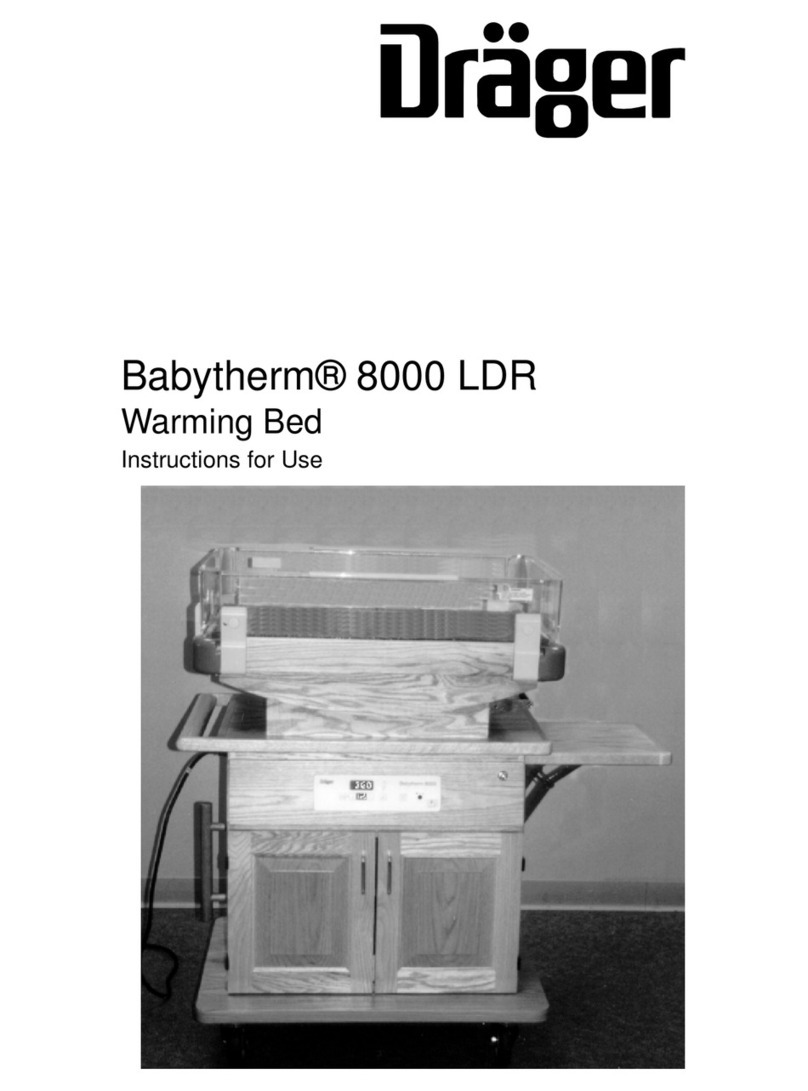
Dräger Babytherm 8000 LDR User manual

Dräger
Dräger Alcotest 6820 GB / SCT User manual

Dräger
Dräger Fabius 4116029 Operating manual

Dräger
Dräger Babytherm 8000 WB User manual

Dräger
Dräger BiliLux User manual

Dräger
Dräger Panorama Nova P User manual

Dräger
Dräger 8000 NC User manual

Dräger
Dräger Infinity Delta User manual

Dräger
Dräger Primus Infinity Empowered User manual

Dräger
Dräger Infinity Acute Care System Evita Infinity... User manual

Dräger
Dräger Drager X-node User manual

Dräger
Dräger Primus Infinity Empowered User manual