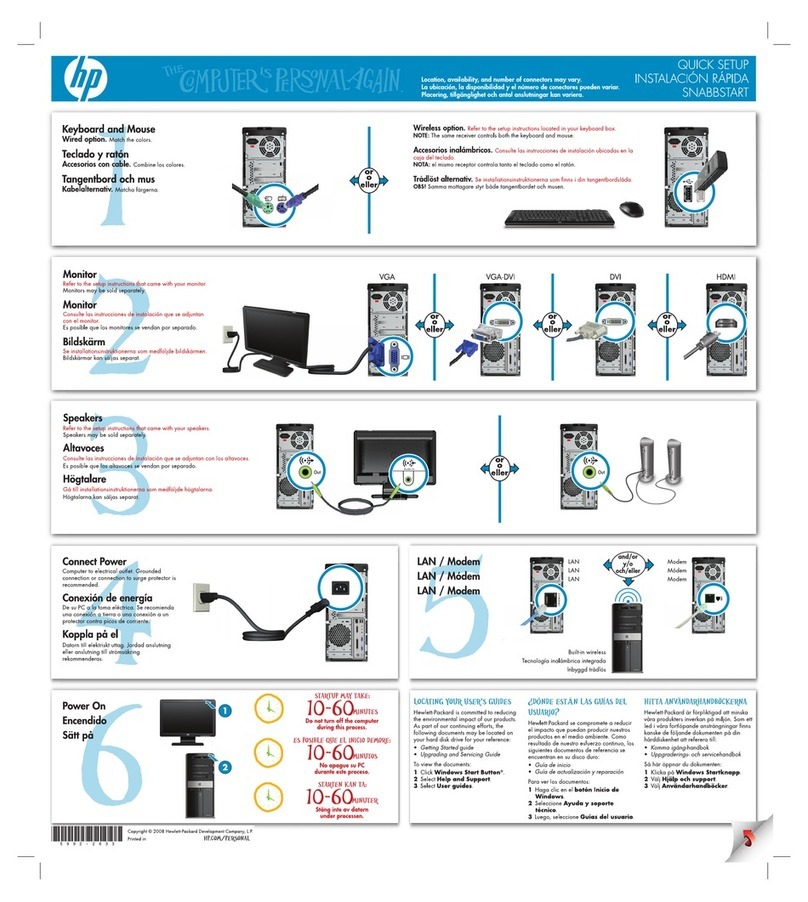
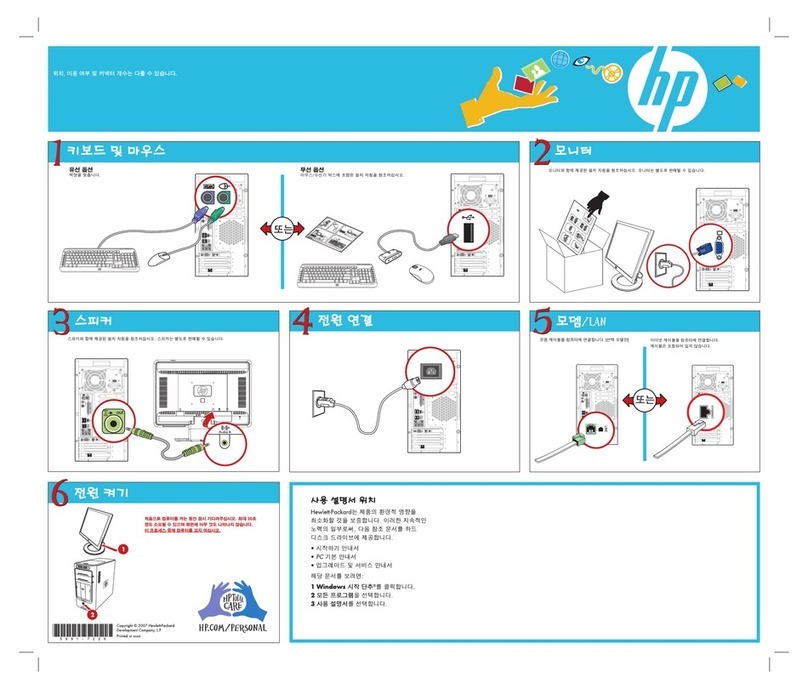
Sharp MZ-80B User manual
Other Sharp Desktop manuals

Sharp
Sharp MZ-808 User manual

Sharp
Sharp PC-4741 User manual

Sharp
Sharp MZ-350C User manual

Sharp
Sharp PN-TPCi7W7 User manual
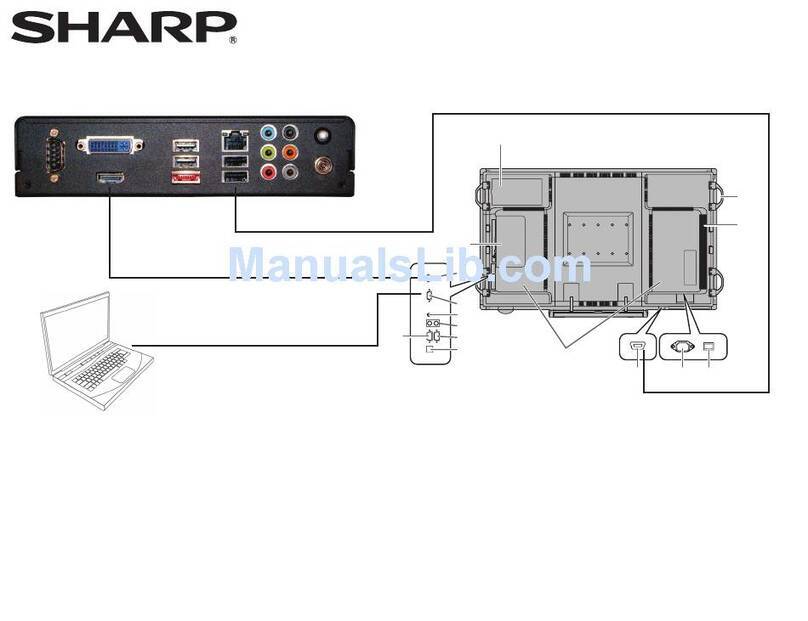
Sharp
Sharp PN-L602B Instruction Manual
Sharp
Sharp ZQ-4400 User manual

Sharp
Sharp MZ-700 Series User manual
Sharp
Sharp PC-AX40 User manual
Sharp
Sharp MZ-80A User manual

Sharp
Sharp MZ-700 Series Installation guide

Sharp
Sharp SCR3042FB User manual

Sharp
Sharp MZ-800 Use and care manual

Sharp
Sharp CE-159 User manual

Sharp
Sharp MZ-800 User manual

Sharp
Sharp MZ-700 Series User manual

Sharp
Sharp MZ-5600 User manual

Sharp
Sharp MZ-80B Installation guide

Sharp
Sharp YO-270 User manual

Sharp
Sharp PN-TPC1W User manual

Sharp
Sharp YO-250M User manual