eKey FS OM Crestron Series User manual

ID347/722/0/650: Version 1, 2019-07-25; Media Center ID: 3018
en
OPERATING INSTRUCTIONS
ekey Crestron

General en│2
English
Original operating instructions –ID347/722/0/650
Table of contents
1General .......................................................................................................................3
1.1 Note ....................................................................................................................3
1.2 Product liability and limitation of liability ...................................................................3
2Notices, symbols and abbreviations............................................................................4
3Safety information ......................................................................................................4
3.1 Life-threatening danger resulting from electricity........................................................ 4
3.2 Safety against tampering ........................................................................................4
4Product description.....................................................................................................5
4.1 System overview ...................................................................................................5
4.2 Scope of delivery and required components ...............................................................5
4.3 Additional components required ...............................................................................5
4.4 Supported finger scanners.......................................................................................6
4.4.1 Function of the Crestron access control system ....................................................6
4.4.2 Components of the Crestron access control system...............................................6
4.4.3 Correct operation of the finger scanner ...............................................................7
4.4.4 Optical signals on the finger scanner................................................................... 8
5Installation and activation ..........................................................................................8
5.1 Activating the system .............................................................................................8
6Activating the finger scanner......................................................................................8
6.1 Activating the finger scanner ...................................................................................9
7User administration ..................................................................................................11
7.1 Identification methods.......................................................................................... 11
7.2 Storing a user ..................................................................................................... 11
7.3 Storing identification methods ............................................................................... 12
7.3.1 Storing fingers .............................................................................................. 12
7.3.2 Storing RFID transponders .............................................................................. 13
7.4 Managing existing users........................................................................................ 14
Deleting a user/finger and changing permissions............................................................... 14
8Logs ..........................................................................................................................15
9Maintenance .............................................................................................................16
10 Disposal ....................................................................................................................16

General www.ekey.net en│3
1General
ekey biometric systems GmbH operates a quality management system in compliance with EN ISO
9001:2008 and is certified accordingly.
1.1 Note
These instructions form a component of the product. Ensure that they are stored in a safe place.
Please contact your dealer for further information about the product.
1.2 Product liability and limitation of liability
Safe operation and function of the devices can be impaired in the following situations. Liability due
to malfunctioning is transferred to the operator/user in such cases:
□The system devices are not installed, used, maintained and cleaned in accordance with the
instructions.
□The system devices are not used within the scope of proper use.
□Unauthorized modifications are carried out on the system devices by the operator.
These operating instructions are not subject to updating. Subject to optical and technical
modifications, any liability for errors and misprints is excluded.
Although these operating instructions cover some elements of operating the Crestron system in
conjunction with ekey finger scanners, ekey’s liability only extends to the finger scanners produced
by ekey which are integrated in the system.
Our general terms and conditions apply as valid at the date of purchase. See http://www.ekey.net.
ekey biometric systems GmbH provides a 36-month warranty for material or processing defects.
This warranty is only valid in the country where the product was purchased. The product may only
be used with original ekey spare parts and accessories.

Notices, symbols and abbreviations www.ekey.net en│4
2Notices, symbols and abbreviations
NOTICE
Denotes additional information and useful tips.
DANGER
Denotes imminent danger which could lead to death or serious injuries.
ATTENTION
Denotes possible property damage which cannot result in injuries.
Symbols:
1.
Step-by-step instructions
Reference to sections of these instructions
Reference to the mounting instructions
Reference to the wiring diagram
□
Listing without specified order, 1st level
ekey home FS OM
Product names
Button
Buttons
Abbreviations:
CP
Control panel
3Safety information
3.1 Life-threatening danger resulting from electricity
DANGER
All ekey devices are to be operated with safety extra-low voltage (SELV). Only use power supplies
rated protection class 2 according to VDE 0140-1.
Failure to do so will result in life-threatening danger due to electric shock.
Only certified electricians are authorized to carry out the electrical installation!
3.2 Safety against tampering
Mount the controller in a safe internal area. This prevents tampering from the outside.

Product description www.ekey.net en│5
4Product description
4.1 System overview
Fig. 1: Overview of the system
Features:
oOwn Crestron access system
oAccess logging
oCustomized access rights
oCentralized administration via the Crestron Touch Screen
oProgrammable time slots
oCan store up to 100 fingerprints and 100 RFID transponders
4.2 Scope of delivery and required components
The ekey finger scanner for Crestron comes with the following components:
•ekey finger scanner for Crestron
•Mounting instructions
•Wiring diagram
•License key
4.3 Additional components required
oCrestron Controller (3-Series)
oCrestron Touch Screen(s)

Product description www.ekey.net en│6
4.4 Supported finger scanners
Product
group
Illustration
Product name
ekey FS OM
ekey FS OM I Crestron
ekey FS OM I RFID Crestron
ekey FS OM E Crestron
ekey FS OM E RFID Crestron
ekey FS UP I SC Crestron
ekey FS UP I SC RFID Crestron
ekey FS UP E SC Crestron
ekey FS UP E SC RFID Crestron
Table 1: Finger scanner outlet mounted for Crestron
Product
group
Illustration
Product name
ekey FS IN
ekey FS IN E Crestron
ekey FS IN E RFID Crestron
Table 2: Finger scanner integra for Crestron
4.4.1 Function of the Crestron access control system
The ekey finger scanner detects the fingerprint by means of a line sensor. The controller processes
it. It then compares the result with the stored fingerprint image. The finger scanner only works
correctly and reliably with the front phalanx print. Swipe your finger steadily and evenly over the
sensor in the correct position.
1Front phalanx
2Fingerprint
Fig. 3: Fingerprint
The Crestron system offers an interface for individual permission assignment and central
administration via a Crestron Touch Screen. The system also logs the access events and enables
the user to program custom time slots.
4.4.2 Components of the Crestron access control system
System components
Function
Finger scanner
Identification of fingers or RFID transponders
Crestron Controller
Controls the Crestron access control system
Crestron Touch Screen
Interface for managing registration units and access
permissions.
Displays recorded access logs and any other elements
connected to the Crestron system.
Table 3: Components of the Crestron access control system
1Right guiding edge
2Sensor
3Left guiding edge
Fig. 2: Finger swipe
area

Product description www.ekey.net en│7
4.4.3 Correct operation of the finger scanner
Incorrect operation will impair the function of the finger scanner.
Step
Figure
Description
1st
Hold your finger straight, place it centrally between the
guiding edges. Do not twist the finger.
2nd
Place the joint of the front phalanx directly onto the sensor.
Place your finger flat onto the finger swipe area.
3rd
Stretch out the neighboring fingers.
4th
Move your finger evenly downwards over the sensor. Move the
whole hand simultaneously. Swipe the front phalanx fully over
the sensor in order to achieve optimal results. The movement
takes approx. 1 second.
General hints for achieving a good-quality fingerprint image
□Recommended finger numbering: .
□The index, middle and ring fingers work best. The thumb and little finger work marginally or
not at all.
□If the fingers are frequently wet, save the images with wet fingers.
□Children's fingerprints work from approx. 5 years of age.

Installation and activation www.ekey.net en│8
'Holding up the RFID transponder':
NOTICE
The 'holding up the RFID transponder' option is only available for finger scanners with an RFID
function.
Step
Figure
Description
5th
Hold the RFID
transponder face
parallel to the finger
swipe area of the
finger scanner at a
distance of 1 to
5 cm.
4.4.4 Optical signals on the finger scanner
There are 2 types of LED:
□Status LED for operating status
□Function LED for indicating the function of the overall system.
3Status LED
4Function LEDs
Fig. 4: Optical signals on the
finger scanner
5Installation and activation
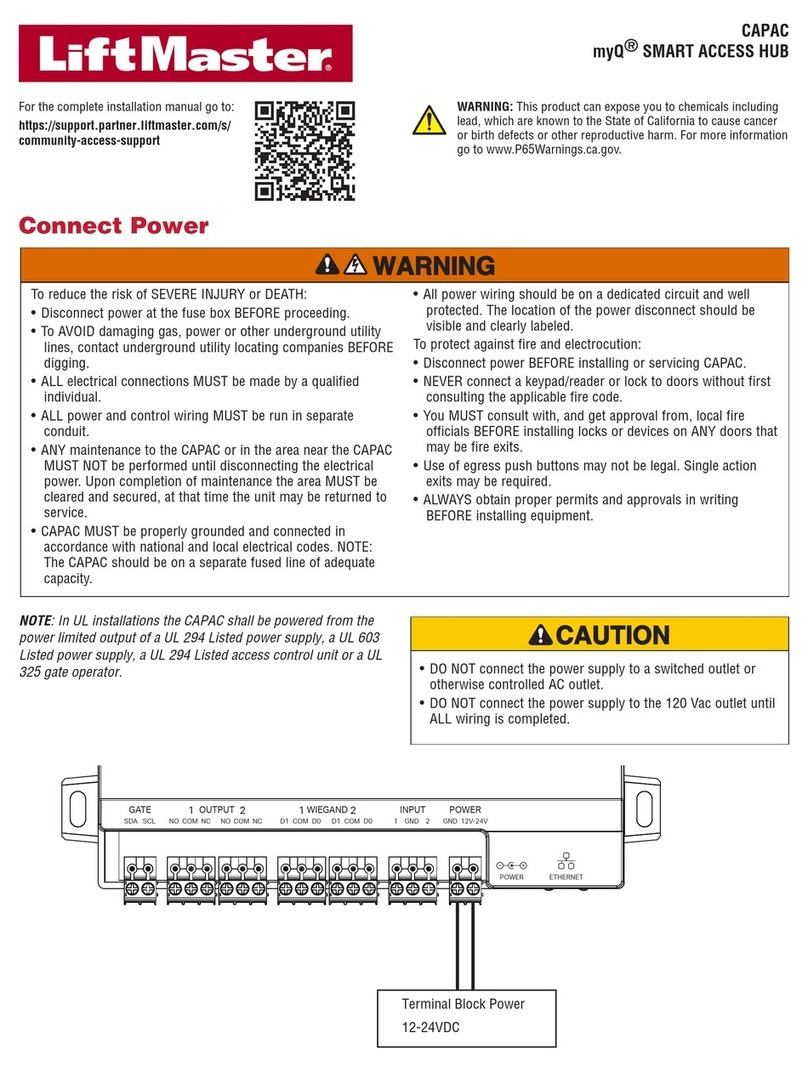
5.1 Activating the system
ATTENTION
Mount and cable the product correctly before connecting power.
Failure to do so will create a risk of possible property damage!
Do not connect the power supply beforehand!
Mount the system in accordance with the supplied mounting instructions.
Cable the system in accordance with the supplied wiring diagram.
6Activating the finger scanner
Activating the registration units and the controller couples these devices.
In order to begin activation of the ekey finger scanner in the Crestron system, the activation of
the Controller and of the Touch Screen must first be completed.

Activating the finger scanner www.ekey.net en│9
6.1 Activating the finger scanner
NOTICE
Notice: You need the serial number and license key to add the finger scanners. You will find the
serial number on the back of the finger scanner. The license key is included in the scope of delivery
and consists of 16 characters.
Step
Action
Display
1st
On the Crestron Touch Screen, tap on “Settings” (the gear icon in the
top right corner).
2nd
Under OPTIONS, tap on “ADD Device”. Enter the name, serial
number and license key of the device you would like to add.
The LED
flashes orange
If “SAVE Device”is not illuminated in green, the entries are incorrect
or incomplete.
3rd
Tap on “SAVE Device”.
The LED lights
up blue after
successful
integration.

Activating the finger scanner www.ekey.net en│10
Step
Action
Display
4th
Repeat these steps for each additional finger scanner.
✓Activation of the finger scanner is complete. The finger scanner is ready for operation.
NOTICE
Notice: You can add up to a maximum of 10 finger scanners.

User administration www.ekey.net en│11
7User administration
7.1 Identification methods
Under USERS, you can add users assign permissions, store identification methods and assign them
to users. The system allows the storage of up to 200 identification methods, including 100 fingers
and 100 RFID transponders.
7.2 Storing a user
Step
Action
1st
Tap on “Add User”on the left-hand side of the main page. On the right, the ADD/EDIT
USER field will appear.
2nd
Enter the name of the user under ADD / EDIT USER.
3rd
In the “Register fingers” field, select the finger that you would like to store.
This procedure is described in more detail in the following section.
4th
Under “Doors”, select which finger scanners should grant access to this user. Finger
scanners that you do not select here will reject this stored finger.
5th
Under “Schedule”, you can define time slots at your discretion.
The status LED shines green during these time slots when a permitted
piece of identification information is recognized, and access is granted.
The function LEDs shine red when an otherwise permitted piece of
identification information is recognized outside of the corresponding time
slots, and access is denied.
1-Status LED; 2-Function LEDs

User administration www.ekey.net en│12
7.3 Storing identification methods
7.3.1 Storing fingers
NOTICE
Notice: Store at least two fingers per user: one on each hand.
The process for storing fingers is initiated on the MAIN PAGE.
Step
Action
1st
Tap on “Settings” (the gear icon in the top right corner), then under DEVICES on the
finger scanner that you would like to use to store fingers.
2nd
Navigate back to the MAIN PAGE (arrow in the top right corner).
3rd
Under USERS, select an existing user by tapping and holding your finger on the
username (approx. 2 s), or add a new User by tapping on “Add User”.
4th
By tapping on “Enroll”you begin the storing process for the finger you have selected.

User administration www.ekey.net en│13
Step
Action
5th
Swipe your finger across the sensor of the selected finger scanner.
Repeat this step at least twice. Between each individual finger swipe, the finger scanner
lights up orange if the finger storing process is not complete.
During finger storage (after the first finger has been swiped over the sensor), no more
than 10 sec may pass between each swipe. Otherwise, the finger storing process will be
aborted.
6th
The finger scanner lights up green briefly and then returns to blue. The process of storing
the finger is now complete.
✓
The finger has been stored and can be used at any finger scanner to which the user is
granted access permission. You can now store additional fingers or manage the
permissions of this user.
7.3.2 Storing RFID transponders
Follow the same instructions as for storing fingers, but instead of swiping your finger over the
sensor, hold the RFID transponder next to the finger swipe area of the finger scanner at a distance
of between 1 and 5 cm.

User administration www.ekey.net en│14
7.4 Managing existing users
Deleting a user/finger and changing permissions
You can delete a user or finger, change permissions or add new permissions at any time.
Step
Action
1st
First, highlight the user in question on the main page by tapping on the username. Then,
under “Fingers”, select the finger you would like to delete or assign a function or relay to.
2nd
The “Edit Finger” field will appear.
3rd
In the “Functions Assigned” area, you can assign functions and relays to the finger or
deselect them at your discretion.
□ Tap “Save ”to complete the process of adding or removing functions.
□ Tap “Delete” to delete the selected finger.
□ Tap “Return”(arrow at top right) to exit this section without saving any changes you
have made.

Logs www.ekey.net en│15
8Logs
You can view the most recent access events. These events are updated in real time and displayed
on the screen, with the most recent at the top.

Maintenance www.ekey.net en│16
9Maintenance
The system is largely maintenance-free. The sensor surface is essentially self-cleaning due to
repeated use (swiping of fingers). However, if the finger scanner becomes soiled, clean it with a
damp (not wet), non-abrasive cloth. Q-tips, microfiber cloths, and glasses-cleaning cloths are
suitable for this purpose. Cotton-containing materials, paper towels, tissues, kitchen sponges,
damp dish towels, and kitchen roll are not suitable. Use clean water without adding detergent.
Treat the sensor surface with care.
10 Disposal
Pursuant to Directive 2012/19/EU of the European Parliament and of the Council of 4 July 2012 on
waste electrical and electronic equipment, electrical and electronic equipment supplied after
13/08/2005 is to be recycled and may not be disposed of with household waste. As disposal
regulations within the EU can differ from country to country, please contact your dealer for further
information as necessary.

www.ekey.net Made in Austria
ekey biometric systems GmbH operates a quality management system in compliance with EN ISO 9001:2015 and is certified accordingly.
Austria
ekey biometric systems GmbH
Lunzerstraße 89, 4030 Linz, Austria
Phone: +43 732 890 500 0
Eastern Adriatic region
ekey biometric systems d.o.o.
Vodovodna cesta 99, SI-1000 Ljublijana
Phone: +386 1 530 94 89
Germany
ekey biometric systems Deutschland GmbH
Industriestraße 10, D-61118 Bad Vilbel
Phone: +49 6187 906 96 0
Italy
ekey biometric systems Srl.
Via Copernico, 13/A, I-39100 Bolzano
Phone: +39 0471 922 712
Switzerland & Liechtenstein
ekey biometric systems Est.
Landstrasse 79, 9490 Vaduz, Liechtenstein
Phone: +41 71 560 54 80
United States
ekeyUSA Systems, LLC
1950 Northgate Blvd. STE D2
Sarasota, FL, 33637
T:+1 (941) 870-4757
This manual suits for next models
11
Table of contents
Other eKey IP Access Controllers manuals

eKey
eKey TOCAhome integra User manual
eKey
eKey ekey home CP WM 1 User manual

eKey
eKey Home Manual

eKey
eKey TOCAhome User manual
eKey
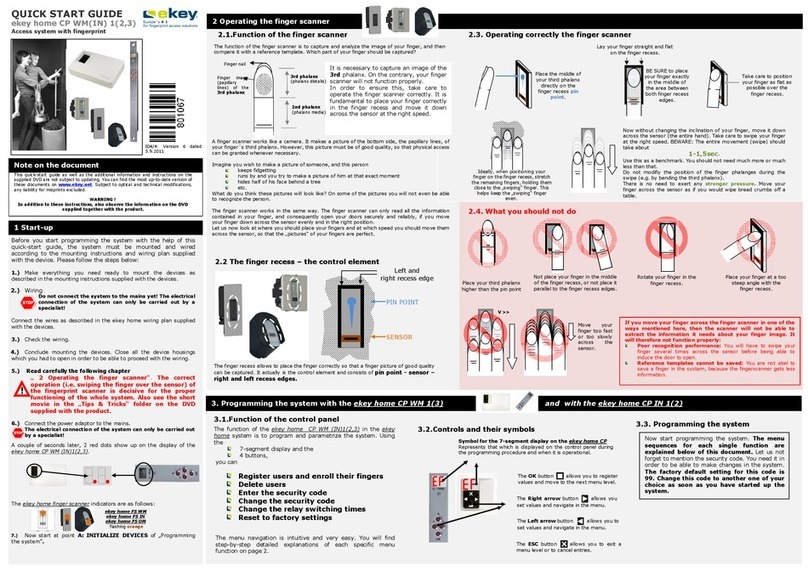
eKey TOCAhome Installation instructions
eKey
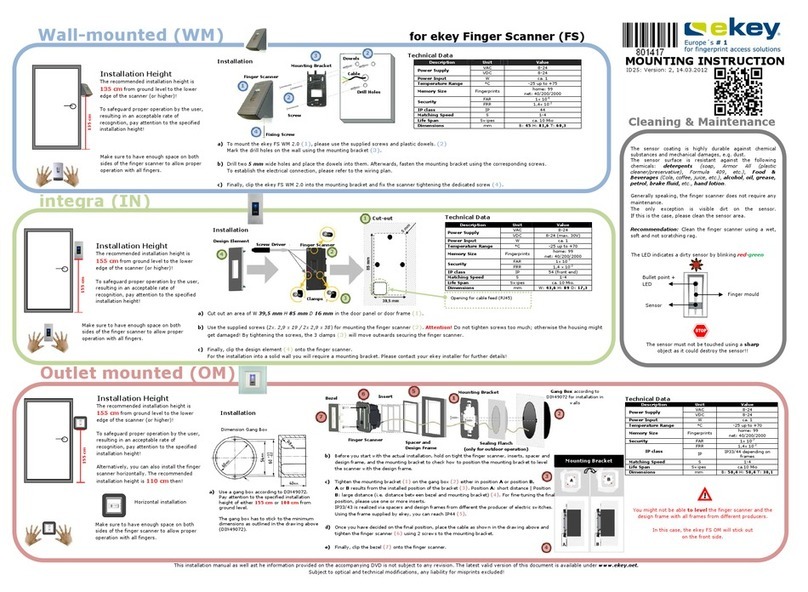
eKey Home CP WM 1 User manual
eKey
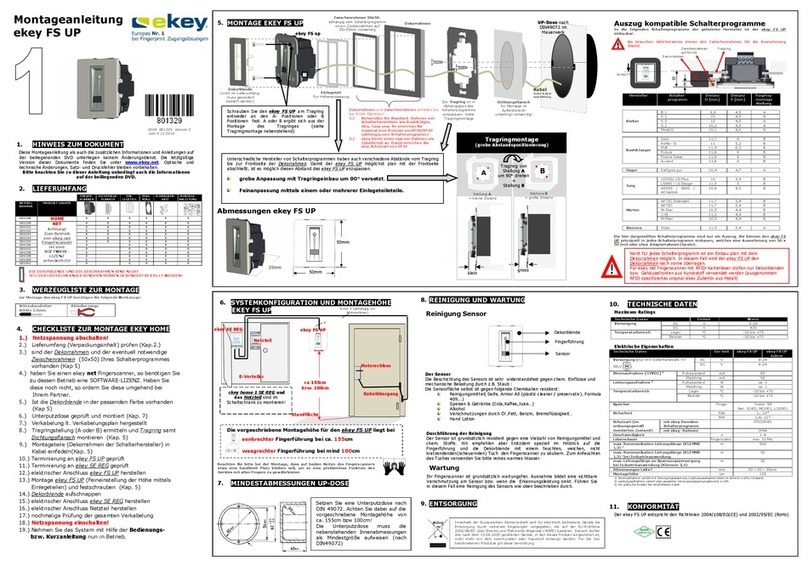
eKey FS WM 2.0 User guide
eKey
eKey FS UP User manual

eKey
eKey Multi User manual
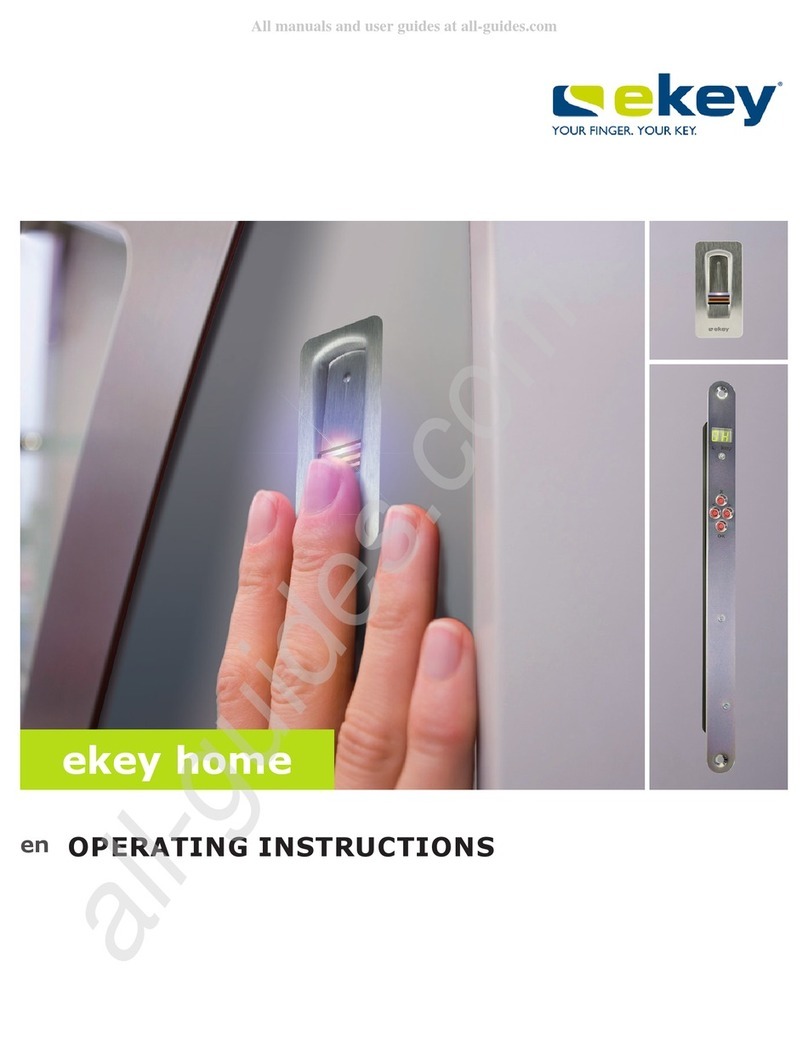
eKey
eKey home Series User manual
Popular IP Access Controllers manuals by other brands

Samsung
Samsung SSA-R1001 quick guide
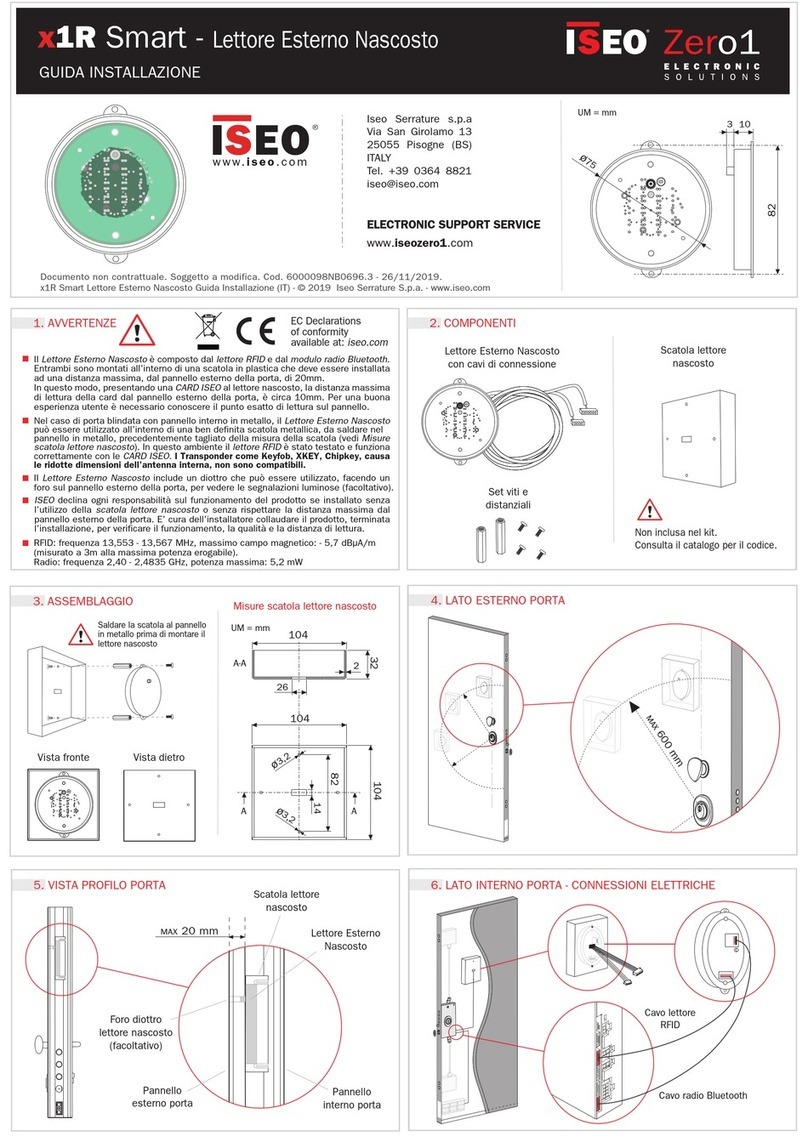
Iseo
Iseo Zero1 x1R Smart installation guide

Dea
Dea Digipro Operating instructions and warnings

Continental Access
Continental Access CARDACCESS 3000 - ARCHITECTURAL AND ENGINEERING SPECIFICATION... specification

Viking
Viking ES-1 Technical practice

Sebury
Sebury K3-3 instruction manual