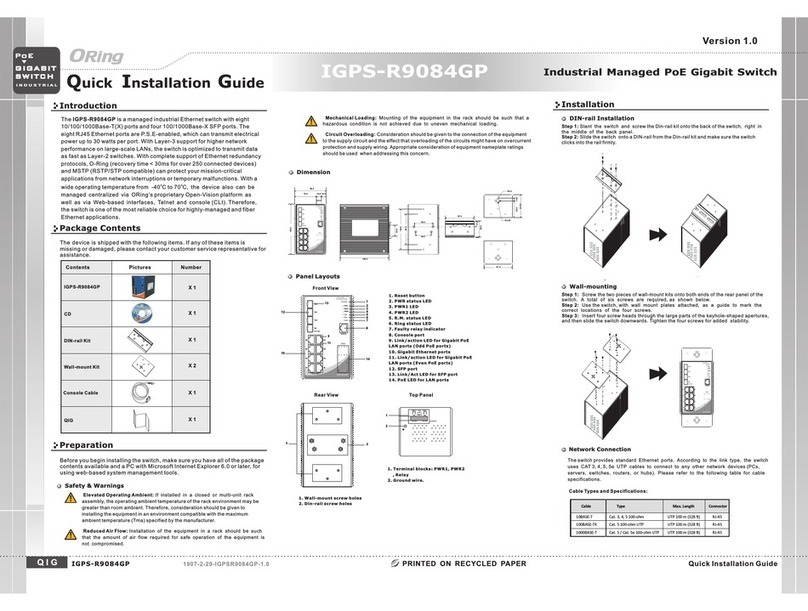
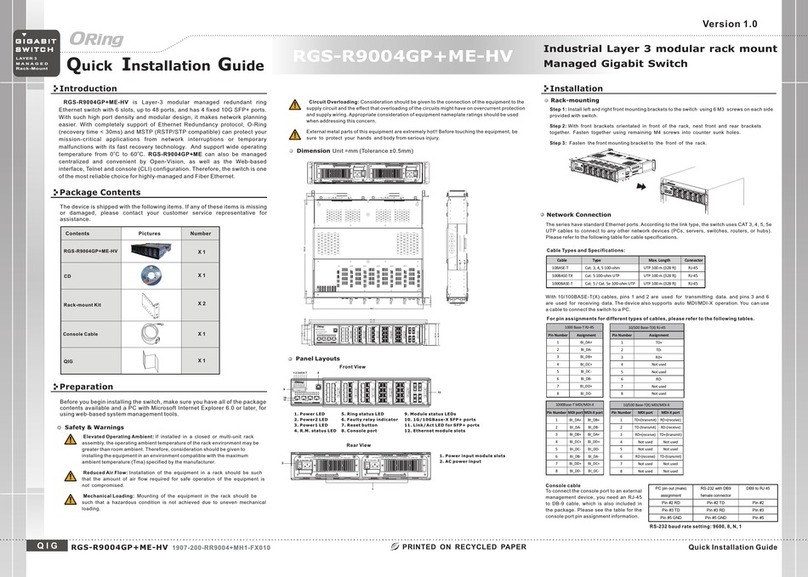
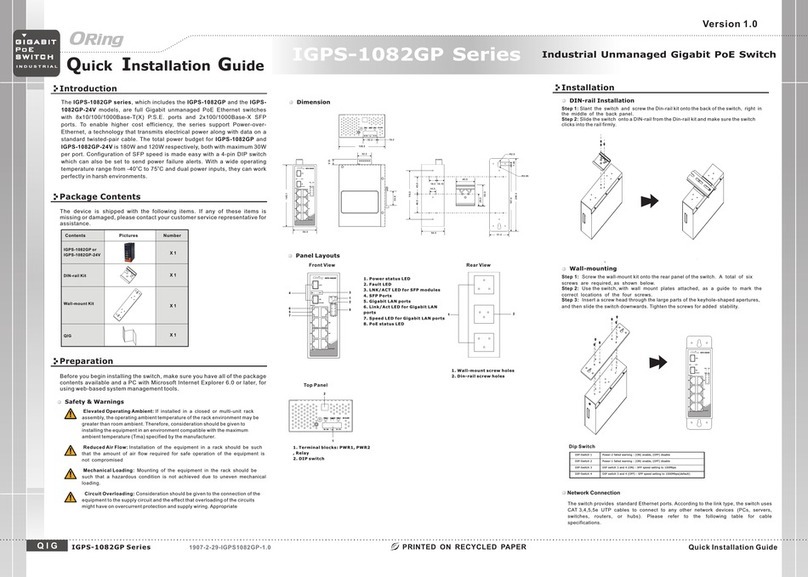
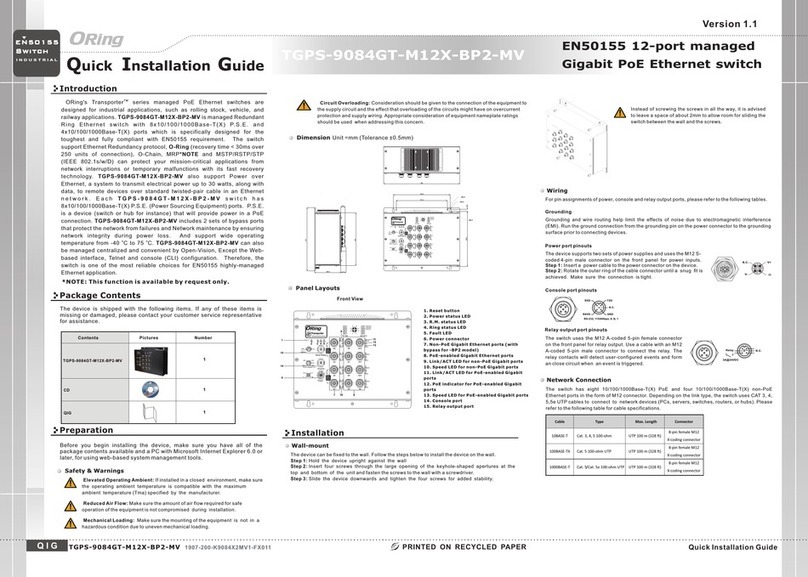
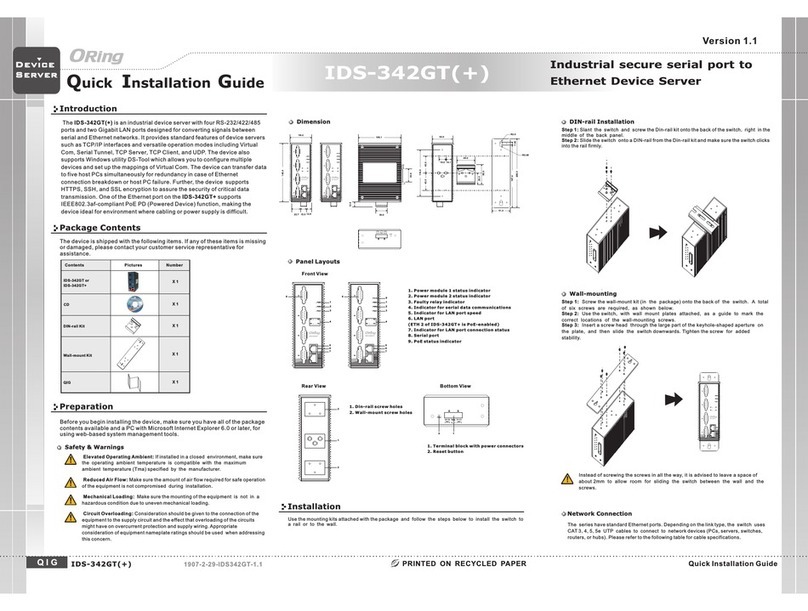
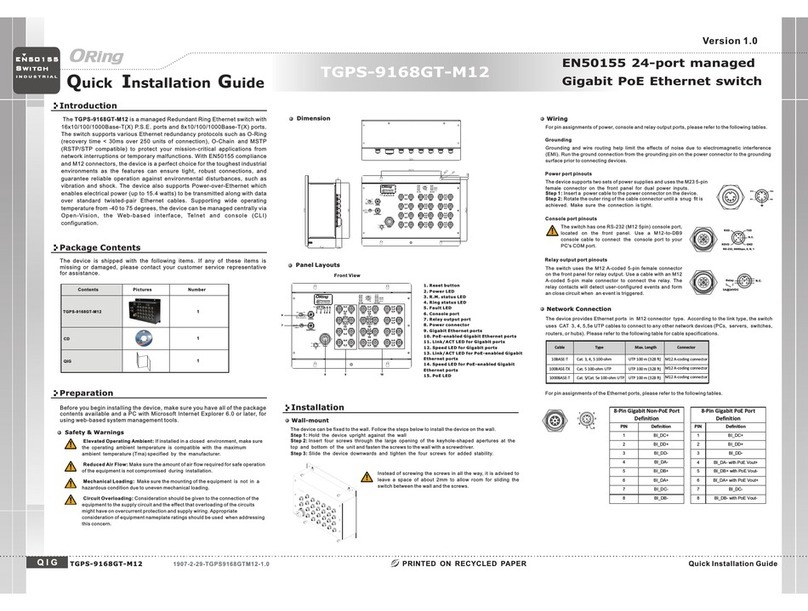
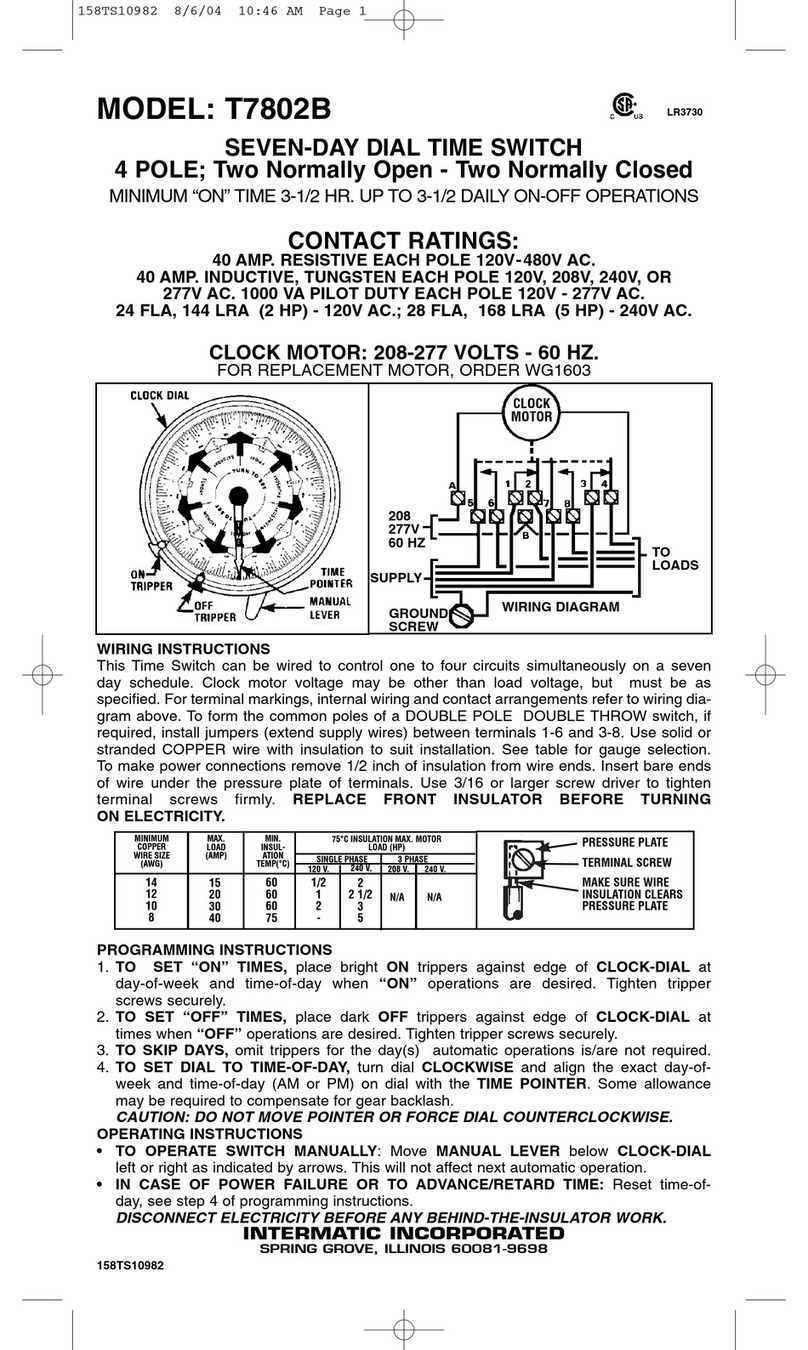
TRGPS-9084GT-M12X-BP2-MV User Manual
ORing Industrial Networking Corp
Below is a detailed description of each port type, including Unaware, C-port, S-port,
and S-custom-port.................................................................................................................63
Examples of VLAN Settings..............................................................................................66
5.4.3 Private VLAN..........................................................................................................70
5.5 SNMP .............................................................................................................................71
5.5.1 SNMP System Configurations ...........................................................................72
5.5.2 SNMP Community Configurations....................................................................74
5.5.3 SNMP User Configurations.................................................................................75
5.5.4 SNMP Group Configurations..............................................................................76
5.5.5 SNMP View Configurations.................................................................................77
5.5.6 SNMP Access Configurations............................................................................78
5.6 Traffic Prioritization .......................................................................................................79
5.6.1 Storm Control.........................................................................................................79
5.6.2 Port Classification ................................................................................................80
5.6.3 Port Tag Remaking ...............................................................................................82
5.6.4 Port DSCP...............................................................................................................82
5.6.5 Policing....................................................................................................................84
Queue Policing.....................................................................................................................85
5.6.7 Scheduling and Shaping.....................................................................................85
5.6.8 Port Scheduler.......................................................................................................88
5.6.9 Port Shaping...........................................................................................................89
5.6.10 DSCP-based QoS .............................................................................................89
5.6.11 DSCP Translation .............................................................................................90
5.6.12 DSCP Classification.........................................................................................91
5.6.13 QoS Control List...............................................................................................91
5.6.14 QoS Counters....................................................................................................94
5.6.15 QCL Status.........................................................................................................94
5.7 Multicast.........................................................................................................................95
5.7.1 IGMP Snooping......................................................................................................95
5.7.2 VLAN Configurations of IGMP Snooping........................................................96
5.7.3 IGMP Snooping Status.........................................................................................97
5.7.4 Groups Information of IGMP Snooping...........................................................98
5.8 Security...........................................................................................................................99
5.8.1 Remote Control Security Configurations .......................................................99
5.8.2 Device Binding.......................................................................................................99
5.8.3 ACL .........................................................................................................................105
5.8.4 Authentication, Authorization, and Accounting..........................................117