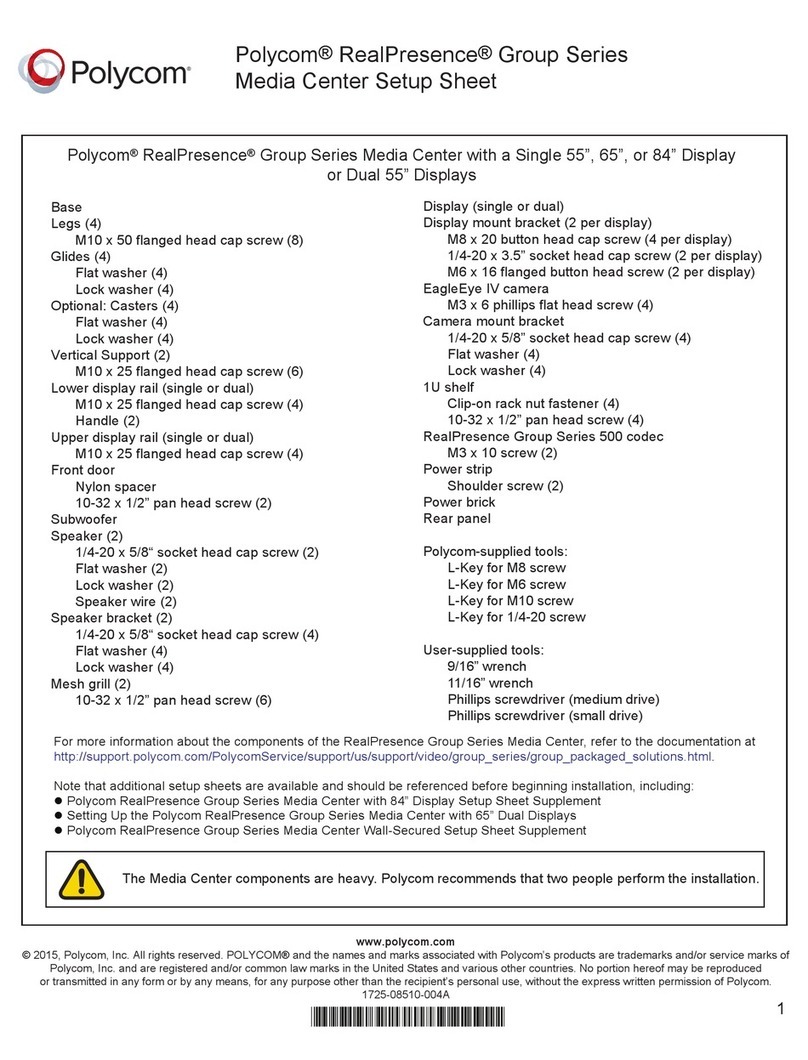
TE20 Videoconferencing Endpoint
Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
8.1.1 Desktop Icons ..........................................................................................................................................................66
8.1.2 Shortcut Bar Icons ...................................................................................................................................................66
8.2 Customizing the Remote Control UI ..........................................................................................................................67
9 Routine Maintenance .................................................................................................................68
9.1 Maintenance Items......................................................................................................................................................68
9.2 Checking the Indicator Status.....................................................................................................................................69
9.3 Checking the Operating Environment ........................................................................................................................69
9.4 Checking the Cleanliness............................................................................................................................................70
9.5 Checking the Connection Status.................................................................................................................................71
9.6 Checking Alarms ........................................................................................................................................................71
9.7 Checking the System Status........................................................................................................................................71
9.8 Checking the System Information ..............................................................................................................................72
9.9 Backup and Restoration..............................................................................................................................................73
9.10 Restoring Factory Settings........................................................................................................................................74
10 Security Maintenance...............................................................................................................76
10.1 Overview ..................................................................................................................................................................76
10.1.1 Purpose of Security Maintenance ..........................................................................................................................76
10.1.2 What Is Layered Security Maintenance.................................................................................................................76
10.2 Application Layer Security.......................................................................................................................................77
10.2.1 Application Layer Account List.............................................................................................................................77
10.2.2 Restoring Systems to Default Settings...................................................................................................................86
10.2.3 Configuring Encryption.........................................................................................................................................87
10.2.4 Web Management Users ........................................................................................................................................87
10.2.5 Web Access Control...............................................................................................................................................88
10.2.6 SSH Access Control...............................................................................................................................................89
10.2.7 Viewing Logs.........................................................................................................................................................90
10.2.8 Enabling FTPS.......................................................................................................................................................91
10.2.9 Configuring an FTPS Server..................................................................................................................................91
10.2.10 Managing Certificates..........................................................................................................................................94
10.2.11 Importing and Updating Web Certificates............................................................................................................95
10.2.12 Importing and Exporting Settings........................................................................................................................96
10.3 System Layer Security..............................................................................................................................................97
10.4 Network Layer Security............................................................................................................................................97
10.5 Management Layer Security.....................................................................................................................................98
10.5.1 Principles of System Maintenance Security...........................................................................................................99
10.5.2 Guidelines for Password Security Maintenance ....................................................................................................99
10.5.3 Log Maintenance Suggestions...............................................................................................................................99
10.5.4 Guidelines on Signaling Diagnosis......................................................................................................................100
10.5.5 Security Evaluation Recommendations ...............................................................................................................100
10.5.6 Backup Suggestions.............................................................................................................................................100
10.5.7 Defect Feedback Suggestions..............................................................................................................................100