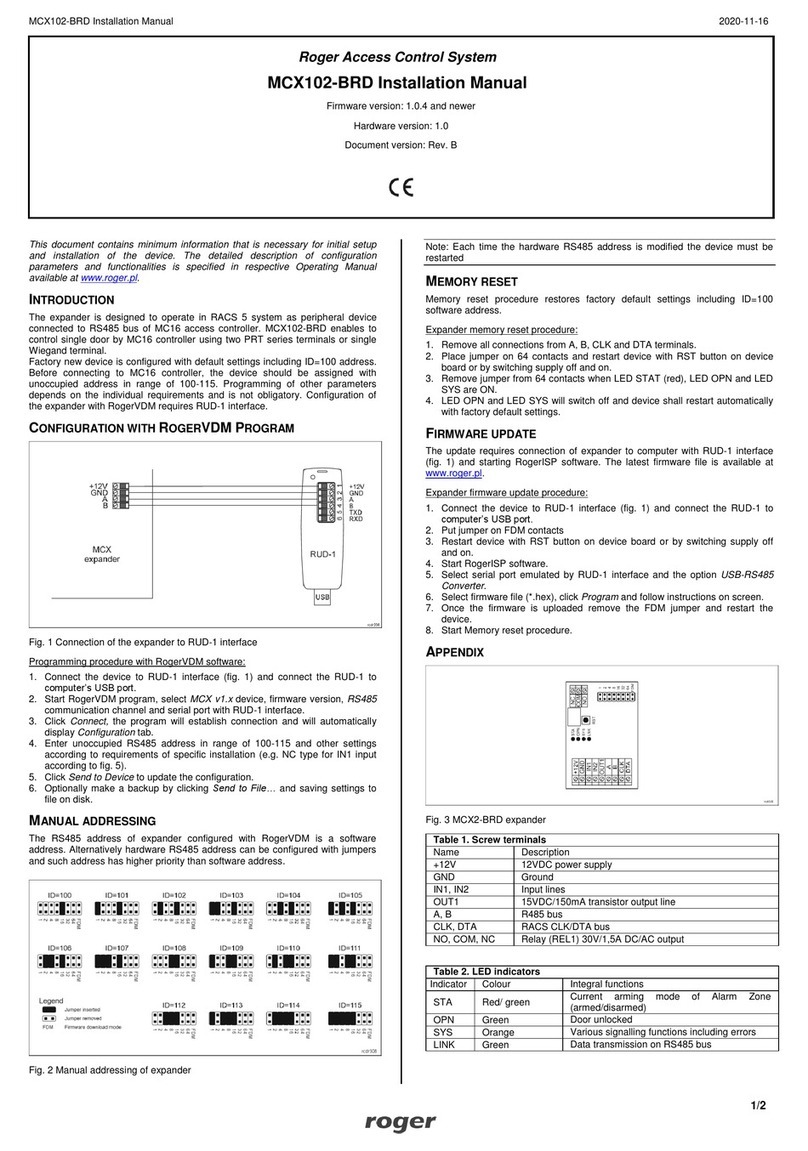
level configuration (RogerVDM). Function are assigned to outputs within high level configuration (VISO).
Multiple functions with different priorities can be assigned to the same output at the same time.
Identification
Following user identification methods are offered by the terminal:
•MIFARE Ultralight/Classic/Plus/DESFire proximity cards
•PINs
•Mobile devices (NFC and BLE)
MIFARE cards
By default the terminal reads serial numbers (CSN) of MIFARE cards but it is possible to program cards with
own numbers (PCN) in selected and encrypted sectors of card memory. The use of PCN prevents card
cloning and consequently it significantly increases security in the system. More information on MIFARE card
programming is given in AN024 application note which is available at www.roger.pl.
The technical characteristics of the device are guaranteed for RFID cards supplied by Roger. Cards from
other sources may be used, but they are not covered by the manufactures warranty. Before deciding to use
specific Roger products with third-party contactless cards, it is recommended to conduct tests that will
confirm satisfactory operation with the specific Roger device and software in which it operates.
PINs
The terminal accepts variable length PINs (by default 4-8 digits concluded with [#] key).
Mobile devices (NFC and BLE)
The terminal OSR88M-IO enables user identification with mobile device (Android, iOS) using NFC or
Bluetooth (BLE) communication. Prior to use of BLE/NFC identification on the terminal, within its low level
configuration (see section 4) configure own NFC/BLE authentication factor encryption key and NFC/BLE
communication encryption key while in case of Bluetooth additionally verify if the parameter BLE activated is
enabled. Install Roger Mobile Key (RMK) app on mobile device and configure the same parameters as in
the terminal. Create key (authentication factor) in RMK defining its type and number, then create the same
authentication factor in VISO software (fig. 4) and assign it to the user with adequate Authorisation(s) at the
terminal. When user wants to identify at the terminal using mobile device then key (authentication factor)
can be selected from the screen or with gesture.
Fig. 4 Authentication factor type in VISO software
2. INSTALLATION